Spectra Assure
Software
Supply Chain Security
Spectra Assure analysis for end-to-end software development workflows, containers and release packages
Learn MoreRL Researchers Identify Compromise of ETHCode, a VS Code Extension
Attacks on AI, Crypto, Open Source, and Commercial Software
Identify Risks and Threats in the Commercial Software You Use
Software supply chain is one of the biggest challenges that we face as an industry... We really need to be able to know how much we trust that piece of software. And that’s where Spectra Assure comes in.

Traditional software analysis tools exclusively detect vulnerabilities, leaving users unaware of active, severe threats hidden across their components. ReversingLabs Spectra Assure leverages the world’s largest threat repository to identify active threats, malware, secrets, tampering, and more. Development teams now have complete analysis of first party, open source, and commercial software components, identifying critical issues that legacy tools miss.
Know the software your organization is purchasing and deploying is secure. Legacy approaches towards vendor application security testing are incomplete and unscalable. Spectra Assure identifies threats and risks embedded in software, delivering trust in your third party risk management strategy.
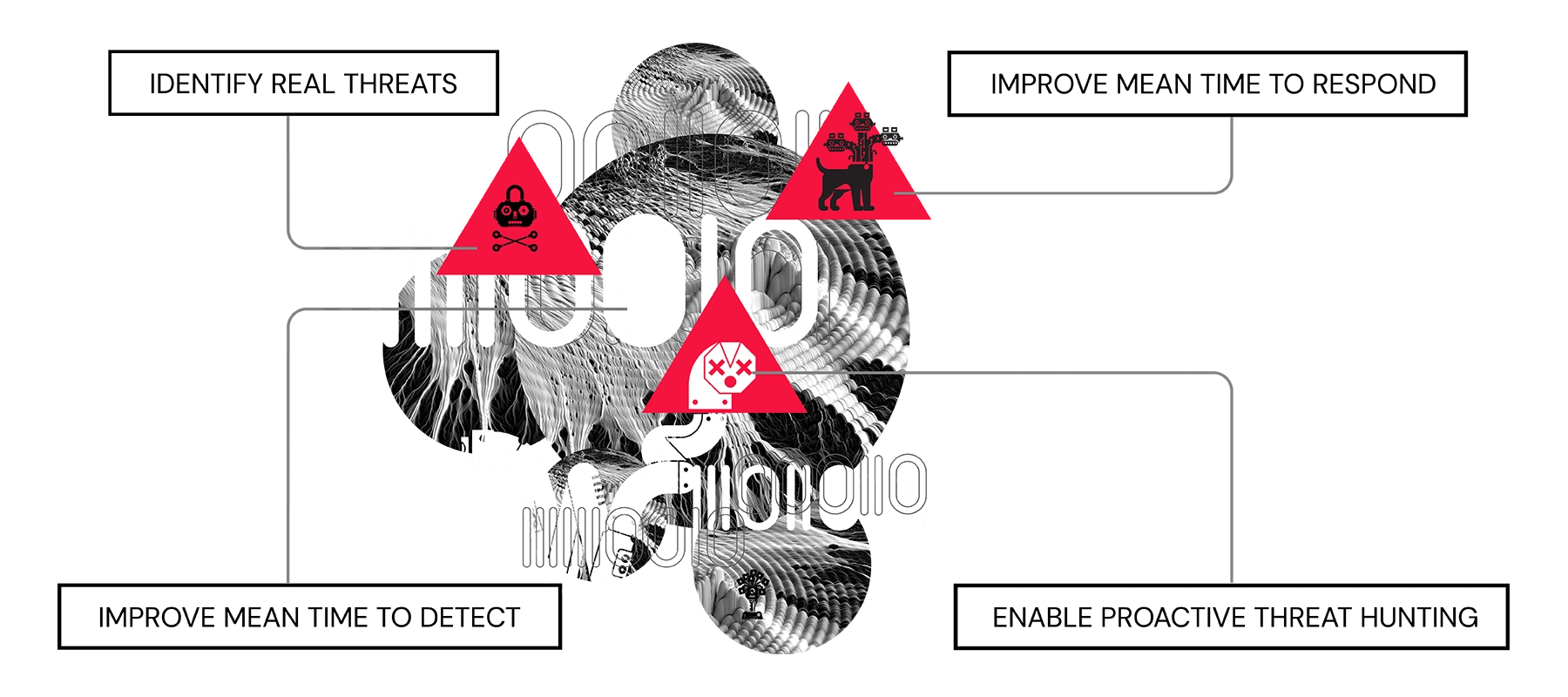
Elevate your security posture by boosting visibility, slashing costs, and supercharging efficiency into your security operations. Experience precision with the most powerful static binary analysis data, reducing false positives and accelerating threat convictions. ReversingLabs Malware Analysis and Threat Hunting solutions deliver an automated, integrated approach to your security operations, driving an enterprises evolution from threat chaos to data clarity.
Deep software and file analysis to speed release and response
Spectra Assure analysis for end-to-end software development workflows, containers and release packages
Learn MoreThe world's most trusted and authoritative data corpus of goodware and malware intelligence, consisting of more than 422 billion samples
Learn MoreHigh-volume, high-speed inspection of files from web, email, endpoints, file shares, and cloud storage – scalable to millions of files per day.
Learn MoreAn instant malware lab for automated, in-depth static and dynamic analysis, plus powerful search and threat hunting
Learn More
Discover key attack trends in RL’s third-annual Software Supply Chain Security Report. Get expert insights on emerging threats over the past year.
Learn More
Why legacy AST tools don’t provide adequate coverage for today’s threats.
Learn More
See what product and application security teams need to know to protect against software supply chain compromises.
Learn More