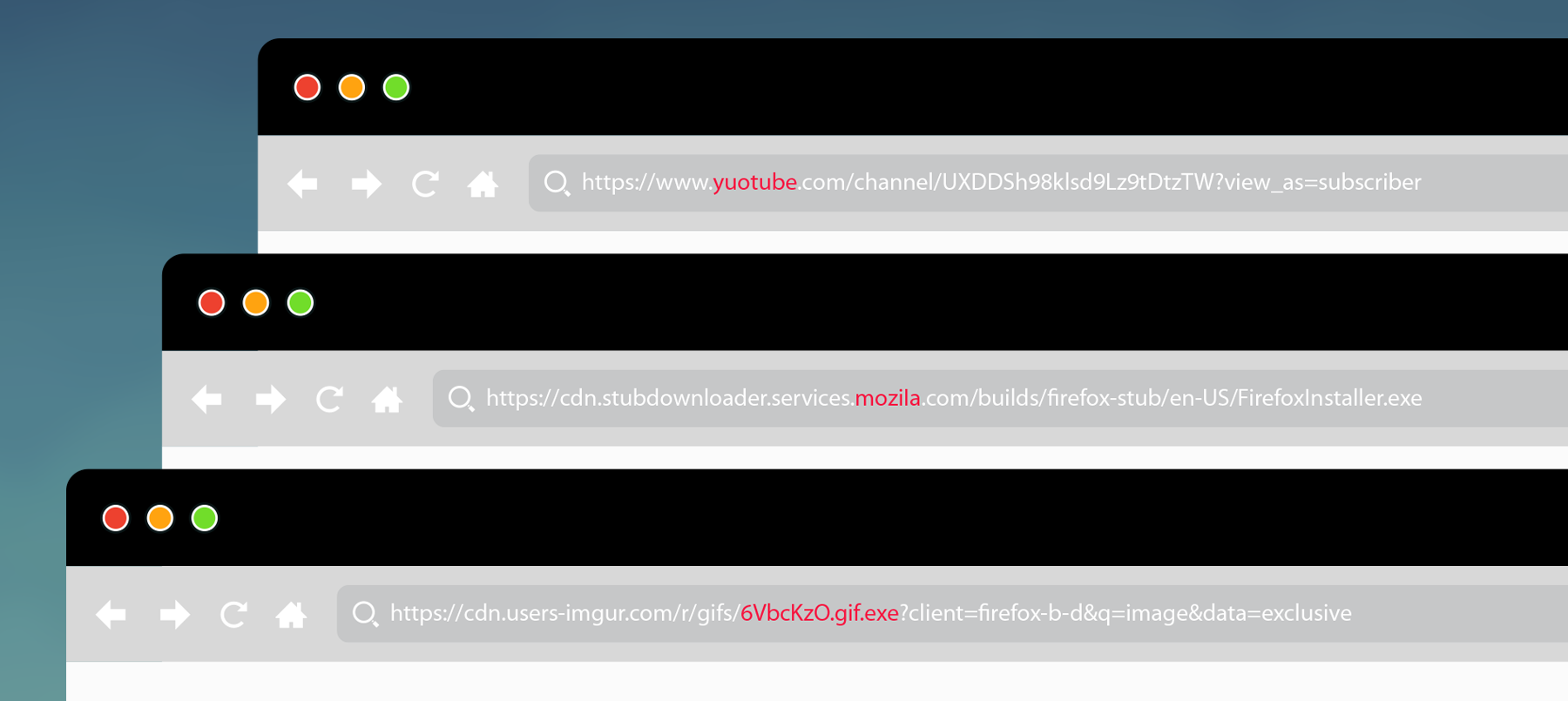
The PDF invoice that phished you
Phishing attacks are deception attempts that try to trick a person into clicking a link that leads to a credential-stealing page or a malicious application download. Relying on social engineering tactics, they have the potential to grant attackers unauthorized access to infrastructure, services, or information.
Read More