Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
In September, ReversingLabs (RL) threat researchers were among the first to discover a first-of-its-kind self-propagating worm on the npm package repository dubbed “Shai-hulud.” That first wave impacted hundreds of popular npm packages accounting for millions of downloads, as well as a large number of affected parties.
Now, a new wave of infections linked to the Shai-hulud malware has hit the npm open-source repository, marking the second major outbreak of the self propagating worm. At the time of this writing, 795 npm packages have been compromised, many of them widely used by developers of open source and commercial applications. The list of compromised packages includes AsyncAPI related packages, including@asyncapi/specs, with more than 100 million lifetime- and an average of 1.4 million weekly downloads. This package in particular is also believed to be the “patient-zero” package for this wave of attack, meaning it is the first known infected package.
This new set of packages was compromised via a package version update that was released with two new javascript files added: setup_bun.js and bun_environment.js. Execution of the malicious loader in setup_bun.js is triggered through the preinstall script added to package.json file. The loader then executes the obfuscated payload from the bun_environment.js file.
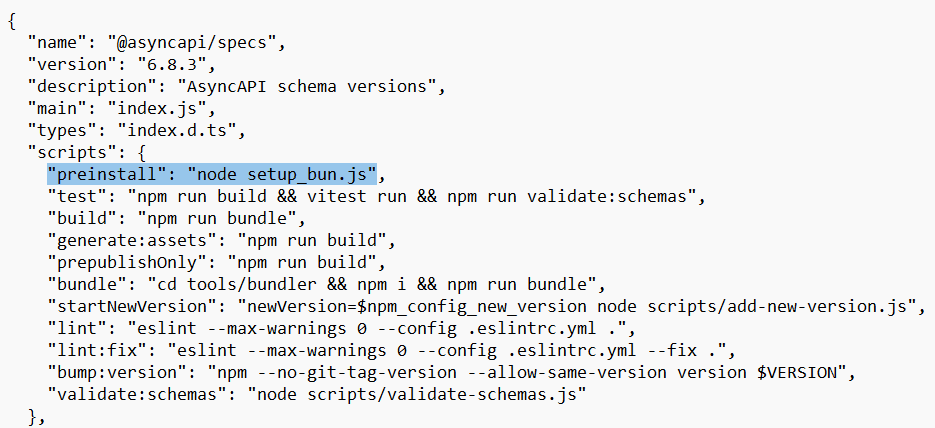
Figure 1: Preinstall script triggering malware execution
The malware copies most of the functionalities observed in the first wave, including stealing cloud service secrets and exfiltrating them to public GitHub repositories — this time with randomly generated names. However, the malware featured in this new wave comes with a specific description: “Sha1-Hulud: The Second Coming.”
The same worm capabilities used in the first wave are also present in the malware of this second wave, in that, once a package is infected, it spawns attacks of its own by allowing the worm to propagate through other open source packages the author maintains. The Sha1-Hulud: Second Coming-variant, also referred to as Shai-hulud 2.0, also adds wiper functionality to the malware, where in specific cases the worm deletes user data folders.

Figure 2: New wiper functionality
See FAQ: Shai-hulud attacksDownload: Software Supply Chain Security Report 2026
RL has identified more than 27,000 GitHub repositories created by the Sha1-Hulud: Second Coming malware in the latest attack (Figure 3). These repositories are intended for storing exfiltrated data harvested from compromised users. GitHub users concerned about whether their account has been compromised should search their account for “Sha1-Hulud:The Second Coming” to identify a (randomly) named exfiltration repository that would indicate a compromise.

Figure 3: Searching for compromised GitHub users
The RL Spectra Assure Community (secure.software) successfully detects the threats posed in this new wave of Shai-hulud. When searching for packages to use, look out for the TH15502 policy violation: “Detected presence of files with behaviors similar to malicious packages published on npm.”

Figure 4: RL Spectra Assure automate detection of this threat
RL recommends that development teams review all dependency updates from the last 12 hours. To prevent getting infected with Sha1-Hulud, disable automated dependency upgrading without prior verification.
The RL threat research team is continuing to monitor this malicious campaign, and more updates will be shared to RL Blog. For the most up-to-date, real-time updates, follow RL on X and/or Bluesky.
The Shai-hulud malware was first identified by RL researchers on September 15. That attack began with a compromise of the npm package rxnt-authentication version 0.0.3, published Sep 14, 2025, after which the malware quickly spread to infect hundreds of npm packages, including some with large weekly download numbers. (Read our origian Shai-hulud FAQ.)
Following the initial outbreak of the Shai-hulud worm in September, GitHub, which maintains the npm registry, unveiled measures to harden the npm package publishing process against account takeovers and malware injection. Those measures include requiring two-factor authentication (2FA) for all local publishing; limiting the lifespan of tokens to seven days; and promoting the use of trusted publishing- an approach pioneered by PyPI that removes API tokens from build pipelines.
Developers publishing a package directly from their own machine (local publishing), rather than via a trusted, automated system (trusted publishing), will need to use hardware security keys, biometrics, authenticator apps, or some other form of 2FA to authenticate themselves.
Indicators of Compromise (IoCs) refer to forensic artifacts or evidence related to a security breach or unauthorized activity on a computer network or system. IoCs play a crucial role in cybersecurity investigations and incident response efforts, helping analysts and security professionals identify and detect potential security incidents.
The following IoCs were collected as part of RL’s investigation of this malicious software supply chain campaign.
Weeks after the initial appearance of Shai-hulud in September, a second campaign was observed in November 2025, targeting npm maintainers and CI environments. Unlike the first wave, the November operation (“Sha1-Hulud: The Second Coming,” or more broadly refrerred to a Shai-hulud 2.0) emphasized credential harvesting and controlled propagation over broad typosquatting.
The threat actor reused parts of the earlier Shai-hulud toolset but refined packaging scripts and obfuscation, showing a deeper understanding of npm publishing workflows. The following FAQ updates and expands RL's earlier FAQ for Shai-hulud 1.0 with new technical details, detection priorities, and defensive actions taken from the second campaign.
Propagation did not change significantly between the first and second versions of Shai-hulud.
Analysts documented a wide range of new package names, staging URLs, and domain patterns distinct from the first campaign. Refer to RL’s published IOCs (PDF) for a list of the new indicators and populate your detection feeds with hashes and domains once confirmed.
RL observed packages associated with AsyncAPI, Browserbase, ENS, OKU Motion PostHog, Postman, Trigo, Zapier, and many other organizations that were affected by the Sha1-Hulud: The Second Coming campaign. Refer to RL’s published IoCs for a list of affected packages. (PDF)
Check for unexpected .npmrc entries, recent global installs, or hidden scripts in node_modules subtrees. Also, compare the registry’s published tarball to your repository build output to ensure alignment.
Additionally, RL's Spectra Assure Community successfully detects the threats posed in this new wave of Shai-hulud including SQ30109, indicating the presence of malicious files through analyst-vetted file reputation. When searching for packages to use, look out for designations such as that, or the TH15502 policy violation, which flags the presence of files with behaviors similar to malicious packages published on npm.
To help defend against future attacks such as Shai-hulud 1.0 and 2.0, developers should take steps to harden their npm package publishing process against account takeovers and malware injection. Those steps should include:
Yes, as npm provenance ensures published packages match a trusted workflow origin (e.g., GitHub Actions OIDC). If stolen tokens such as those harvested by the Shai-hulud 1.0 and 2.0 malware are used outside that path, publish attempts are rejected. This directly neutralizes the Shai-hulud method of credential reuse.
Development organizations concerned about threats like the Shai-hulud npm worm should configure alerts around suspicious behaviors associated with registry-native malware and other attacks including:
The November samples appear to vary string encodings and staging URLs per build but maintain a consistent behavioral signature that includes credential scraping and remote data exfiltration.
Yes. The latest Shai-hulud campaign showed how attackers can abuse automation tokens, which are not protected by user-interactive multi-factor authentication (MFA). To address this risk, organizations should mandate provenance enforcement and scoped automation tokens to close this gap.
Yes. Both Shai-hulud campaigns underscore how developers that install a tainted dependency and execute its lifecycle scripts are at risk of compromising the security of their code and potentially exposing CI credentials. Developers who rely on npm package dependencies should run installs with --ignore-scripts in untrusted contexts and prefer sandboxed environments to reduce the risk of compromise.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial