At ReversingLabs, we believe in genuine ingenuity. We are constantly working to make our security solutions even better for our clients. That’s why we are pleased to announce the availability of Version 6.4 of our A1000 Malware Analysis Platform.
New features in Version 6.4 include:
- Greater flexibility in threat status classifications
- Reliable dynamic and network analysis
- Smoother workflows and maintenance
Here are the essential updates to A1000 6.4 that will aid enterprise security operations centers (SOCs) as they defend their organizations against today’s most pressing cyber threats.
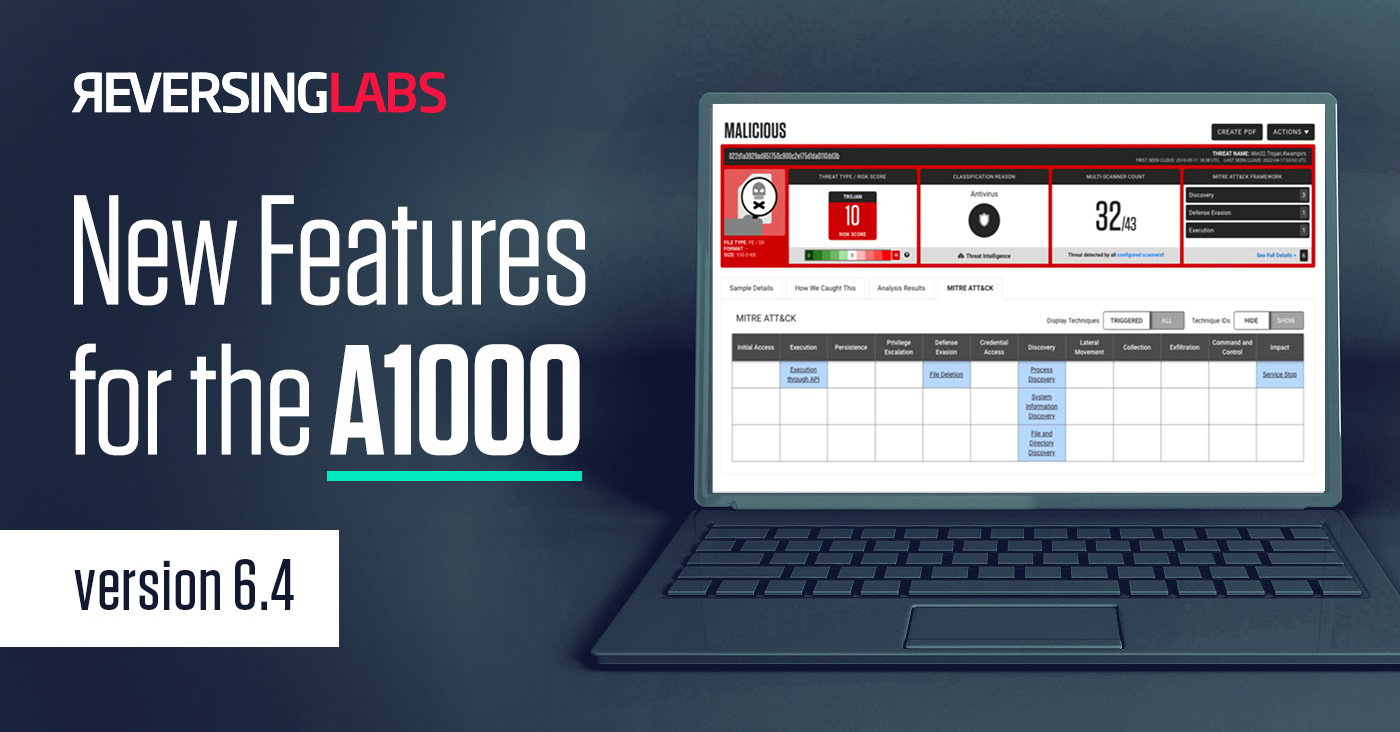
About the A1000
The A1000 provides advanced hunting and investigations through the TitaniumCore high-speed automated static analysis engine, and integrates with file reputation services to provide in-depth rich context and threat classification, identifying over 4000 file types. The A1000 supports visualization, APIs for automated workflows, MITRE ATT&CK framework and integration with third-party sandbox tools. It provides a database of YARA rules and supports custom YARA rule creation.
Improvements in threat status classification
There have been several additions to the product’s static analysis based on feedback from our customers and users.
A key new feature, based on customer feedback, is enabling users to update the ReversingLabs assigned threat status on a sample or bulk of samples via API based on local or internal threat intelligence. SOC teams can now more accurately track the threat classifications.
Reliable dynamic and network analysis
The major highlight of the updates to the Dynamic and Network Analysis functionality of the A1000 is improved network threat intelligence. SOCs using A1000 6.4 will be able to perform the following tasks:
- Analyze URLs and domains. For example: A1000 users can now analyze URLs or domains in suspicious emails for malware
- Block an organization’s access to a URL or its entire domain
- Perform domain analysis, providing details on classification, top threats from a domain, third-party reputation and DNS records
- Provision domain-level information in addition to static and dynamic analysis.
Other highlights of the Version 6.4 update include more efficient and richer triage capabilities for users. These give a SOC full access to the ReversingLabs data corpus. Users will also enjoy an improved setup of file types and configuration options in a single view, increasing the efficiency of a SOC.
Finally, A1000 Version 6.4 includes an optimized cloud sandbox, giving users an out-of-box experience — a top request of our customers.
Smoother workflows and maintenance
The A1000 offers new features that will directly aid threat analysis and IT operations.
Updates in A1000 6.4 include richer concurrent triage and hunting workflows for SOC analysts. The changes will improve response team productivity as well, allowing SOCs to work smarter when responding to pressing threats. Finally, we’ve improved error handling for YARA rules and features for importing and editing invalid YARA rulesets.
Improvements to the A1000 maintenance features include improved Microsoft integration that allows Office365 emails to be forwarded for analysis and inspection by the A1000; a system health indicator, as well as redundancy and quality improvements.
The modern solution for SOC teams
Constantly improving the solutions we offer continues to make ReversingLabs a leader in crafting premier, modern products that respond to today’s most pressing cyber threats.
If you’re interested in learning more about the A1000, schedule a demo with us!








