Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
The plague of ransomware threatening businesses, individuals and public sector organizations continues to rage in 2025. That is one clear message from ReversingLabs’ new Ransomware Feed Report covering the first half of 2025.
The key takeaway: The ransomware threat remains as urgent as ever, but it’s not business as usual. The prevalence of infostealers is surging, including those targeting Mac systems. At the same time, detections of Remote Access Trojans (aka RATs) are declining, while the presence of late stage malware — such as ransomware binaries — is growing, ReversingLabs (RL) data shows. The good news: RL data suggests that adopting simple defensive measures could derail the vast majority of ransomware campaigns.
Here's what your team needs to know about the state of ransomware in 2025.
Learn more: ReversingLabs Ransomware Feed
RL researchers took the time to dig into the content of our Ransomware Feed, looking at data from the first six months of 2025. The last time the team did that was in 2022. Looking back over three years of Ransomware Feed data, one trend is clear: the malware problem isn’t going away. Instead, it’s an epidemic that’s become endemic, with shifting trends but also a steady cadence of campaigns and malware. Compared with three years ago, our latest data shows the same categories of threats persist: ransomware, remote access trojans (RATs), and infostealers — only the names and tactics have changed.
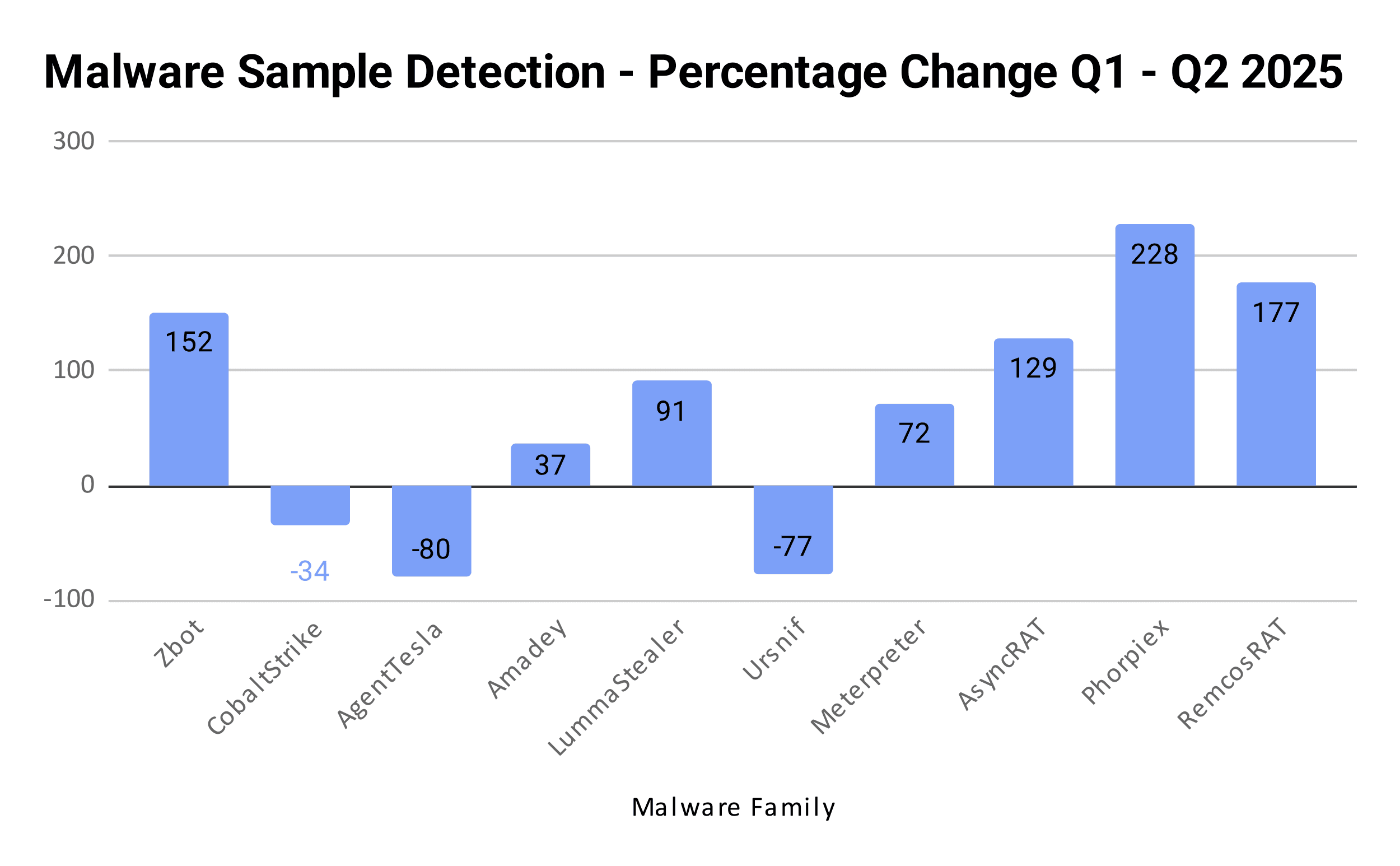
In the first half of 2025, infostealers and RATs were the most common among the top 20 malware families, where leading names like Zbot, CobaltStrike, and AgentTesla held steady. At the same time, families such as NanoCore and Cutwail made aggressive moves up the ranks of the most commonly encountered malware, fueled by new releases or increased use in malware distributions. Other notable families that moved upwards include Phorpiex, which moved up four spots in our rankings, as well as AveMaria, which moved into the top 10.
Rank | Malware Family | Q1 samples | Q2 samples | Total Detections H1 | Change (%) |
|---|---|---|---|---|---|
1 | Zbot | 19237 | 48388 | 67625 | 152 |
2 | CobaltStrike | 8674 | 5717 | 14391 | -34 |
3 | AgentTesla | 5034 | 1020 | 6054 | -80 |
4 | Amadey | 2358 | 3241 | 5599 | 37 |
5 | LummaStealer | 1316 | 2512 | 3828 | 91 |
6 | Ursnif | 2565 | 583 | 3148 | -77 |
7 | Meterpreter | 962 | 1652 | 2614 | 72 |
8 | AsyncRAT | 736 | 1683 | 2419 | 129 |
9 | Phorpiex | 547 | 1795 | 2342 | 228 |
10 | RemcosRAT | 540 | 1496 | 2036 | 177 |
11 | AveMaria | 355 | 1552 | 1907 | 337 |
12 | NjRAT | 442 | 1121 | 1563 | 154 |
13 | SmokeLoader | 405 | 871 | 1276 | 115 |
14 | Quasar | 351 | 611 | 962 | 74 |
15 | FormBook | 411 | 374 | 785 | -9 |
16 | RedLine | 272 | 462 | 734 | 70 |
17 | Cutwail | 65 | 601 | 666 | 825 |
18 | NanoCore | 319 | 346 | 665 | 8 |
19 | Azorult | 395 | 195 | 590 | -51 |
20 | Icedid | 112 | 437 | 549 | 290 |
Top 20 malware families by detected samples January - June 2025 (Source: RL) | |||||
Zooming in, NanoCore’s rise in H1 compared with the previous six months is notable, as NanoCore’s developer is currently serving prison time. The growing instances of NanoCore correlates with the release of a new, free version of the malware resulting in a spike in detections in April and May of this year.
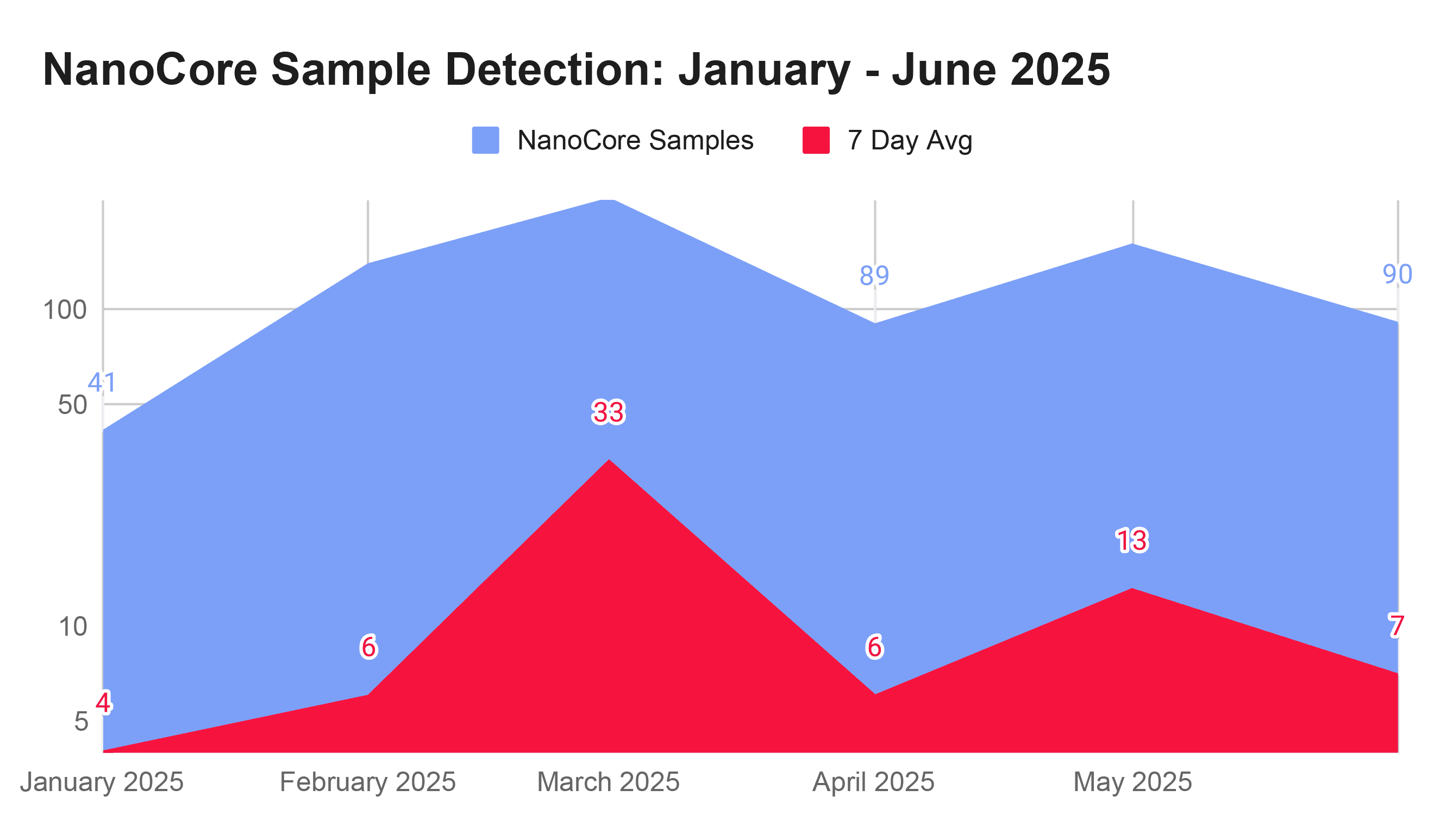
The steady rise and fall of AgentTesla across the first six months of 2025 was also cause for inspection by our researchers. In early March 2025, for example, RL saw close to 300 instances of the malware family on average each week. That number fell – drastically – to just 16 instances on average as of April.
The AgentTesla RAT, written in .NET, has been around for more than a decade and is openly sold online as a malware-as-a-service. The drop in use of AgentTesla may reflect improved detection of the malware, which has prompted threat actors to shift to other malware that is less likely to be detected, according to Ashlee Benge, RL’s Director of Threat Intelligence.
Ransomware on macOS remains rare, but macOS isn’t safe. The ReversingLabs feed shows that infostealers targeting macOS users—like Poseidon, Atomic macOS Stealer (AMOS), and North Korea’s Ferret malware strains—are on the rise.
Mac-focused attackers are getting creative. Campaigns like “Contagious Interview” use fake job recruiters to lure targets into downloading malware disguised as coding tests. Once installed, these infostealers open the door for further exploitation, including ransomware.
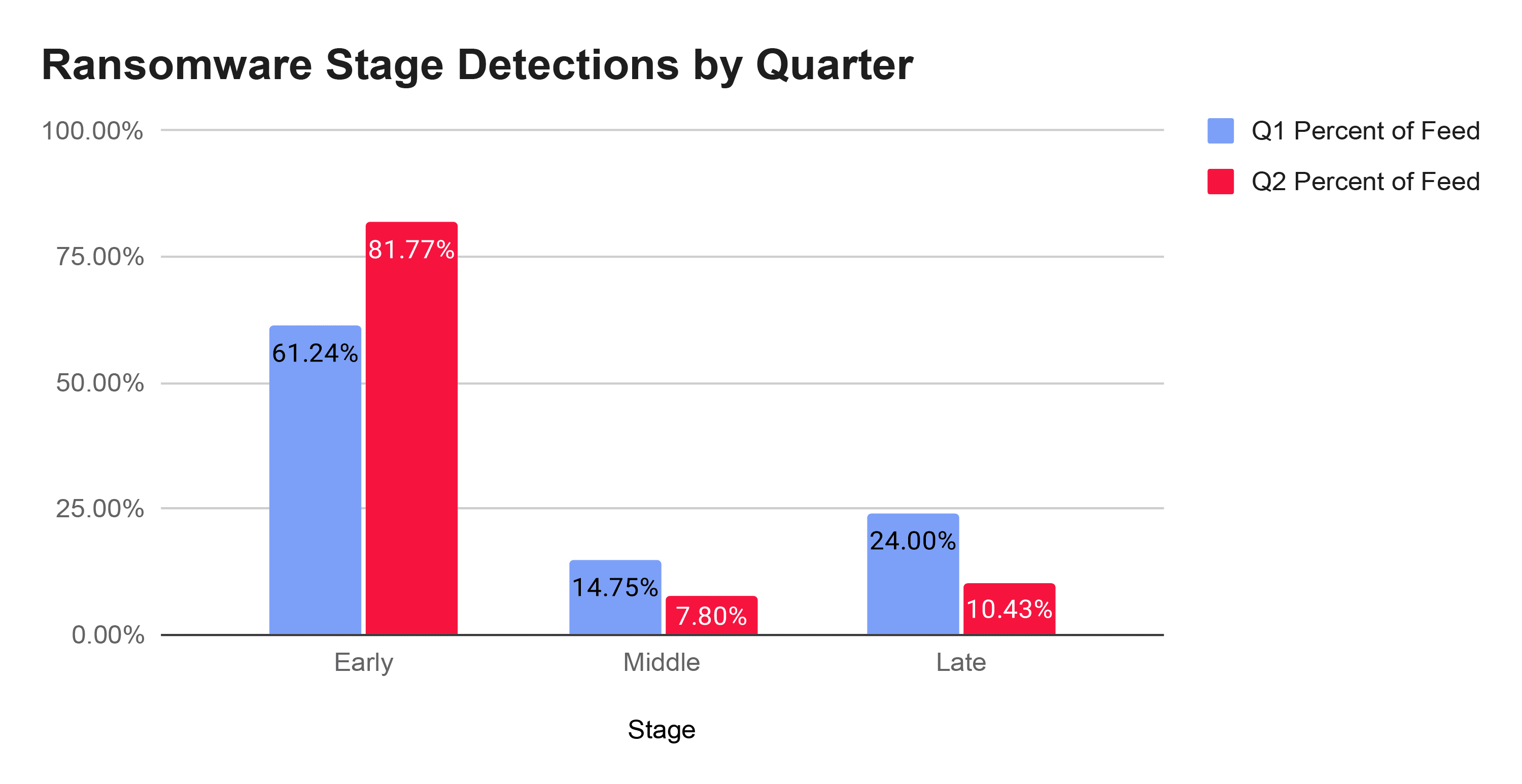
One of the more telling findings from RL’s analysis is how ransomware campaigns are changing in structure. Traditionally, the attack lifecycle includes early, middle, and late indicators of compromise. Middle-stage indicators—typically trojans like Emotet and Trickbot—are declining.
Instead, RL saw a more than 20% increase in early-stage detections like droppers and downloaders between the first and second quarter of 2025. Late-stage indicators—ransomware executables and CobaltStrike payloads—dropped by 13% while middle-stage detections fell nearly 7% during the same period.
This trend suggests that attackers are skipping past the trojan phase, relying on more direct routes to ransomware deployment.
The RL feed tags each malware sample identified with any applicable MITRE ATT&CK techniques. Of the thousands of samples collected in Q1 2025, the technique of “discovery,” in which attackers map out compromised environments, was the most commonly identified. Other leading techniques include “obfuscation,” “DLL sideloading,” and “sandbox evasion.”
In Q2 2025, this picture stayed largely intact, with discovery, DLL sideloading and obfuscation the most prevalent techniques, in addition to the technique of “process injection” jumping the ranks.
DLL sideloading, in particular, is a go-to tactic for ransomware gangs. In January, for example, RL researchers identified malicious PyPI packages that used this technique to run malware through legitimate apps—bypassing many detection systems.
Labeling a problem like ransomware “endemic” might make fixes for the problem seem impossible — or at least complicated. But organizations that want to stop ransomware can embrace simple, well established security practices that will greatly reduce the likelihood of a compromise.
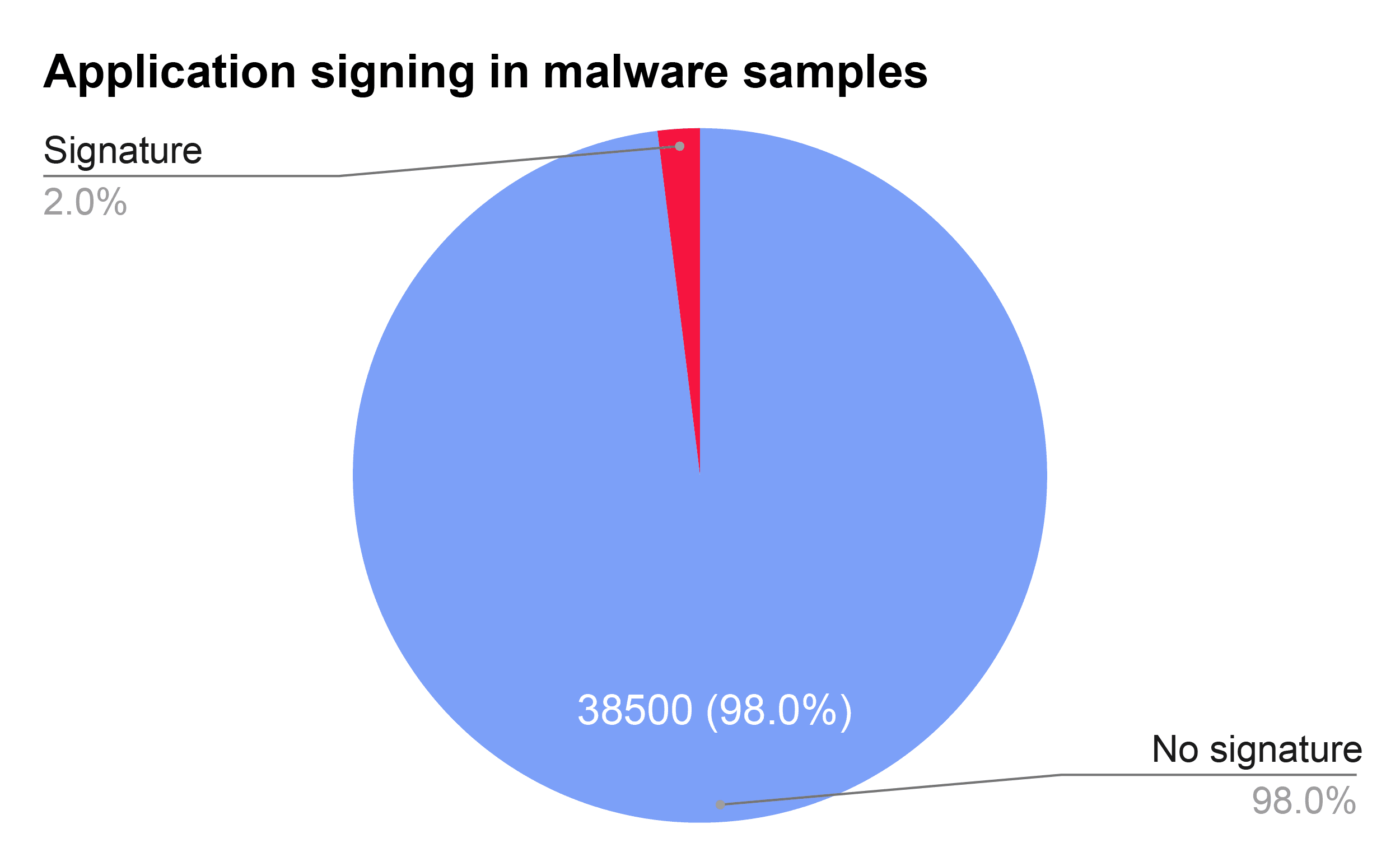
At the top of that list of practices is application signing. RL data shows that more than 98% of the more than 100,000 malware samples that appeared in the Ransomware Feed in the first six months of 2025 were unsigned. And, of the 2% that were signed, more than three quarters used expired or malformed certificates.
In other words, nearly 100% of the samples we detected had no signature, or an invalid one. That’s a massive opportunity for defenders. By introducing a policy to implement- and then enforce application signing, organizations can effectively block the vast majority of ransomware campaigns by restricting execution to signed and trusted applications. In this way, application signing policies could neuter the majority of ransomware threats before they take hold.
If one message comes through clearly from the first half of 2025 in RL's Ransomware Feed, it’s this: the ransomware threat is changing, but the fundamentals of detection and response remain unchanged.
Defenders have tools at their disposal. Application signing is one. Proactive identification of early-stage threats — like infostealers — is another. But it all starts with knowledge and visibility. Your organization must understand how ransomware campaigns are structured, and where campaigns are best intercepted. With that knowledge, the job of defusing them becomes much easier.
As the malware ecosystem evolves, RL will continue to monitor, decode, and report on these changes — helping organizations spot threats before they escalate.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial