ReversingLabs has recently released version 1.2.0 of its TitaniumCloud app for Splunk SOAR. This release introduces our new network reputation action to help SOC teams identify malicious network indicators, increasing the count to a total of 33 available actions to improve your SOC team's efficiency. Here are the network reputation actions, and some example use cases.
What’s new TitaniumCloud for Splunk SOAR 1.2.0
This update mostly focuses on introducing our new network reputation APIs. Here are the new available actions:
• Get network reputation: the Network Reputation API provides a classification of network-related indicators, including URLs, Domain names, and IP addresses.
• Network reputation user override: this action enables TitaniumCloud users to override and set a classification value for a network indicator
• Get list user overrides: this action returns a list of all overrides made by a given user
• Get list user overrides aggregated: this action returns an aggregate of all overrides made by a given user
Continue reading to learn more about the network reputation capabilities of TitaniumCloud and how to effectively utilize the provided actions to automate the process of detecting and responding to network threats.
Network indicator reputation: Key for identifying malware
Network reputation lookups are a new feature that we are excited to offer our TitaniumCloud customers. Where other solutions only provide a one-dimensional result, TitaniumCloud combines traditional reputation information with our massive repository of billions of files and powerful file analysis capabilities to help SOC teams identify malware.
In Splunk SOAR, using the new “get network reputation” action will provide SOC analysts with reputation information for IP addresses, domain names, and URLs. The screenshot below shows the formatted output of an IP address lookup:
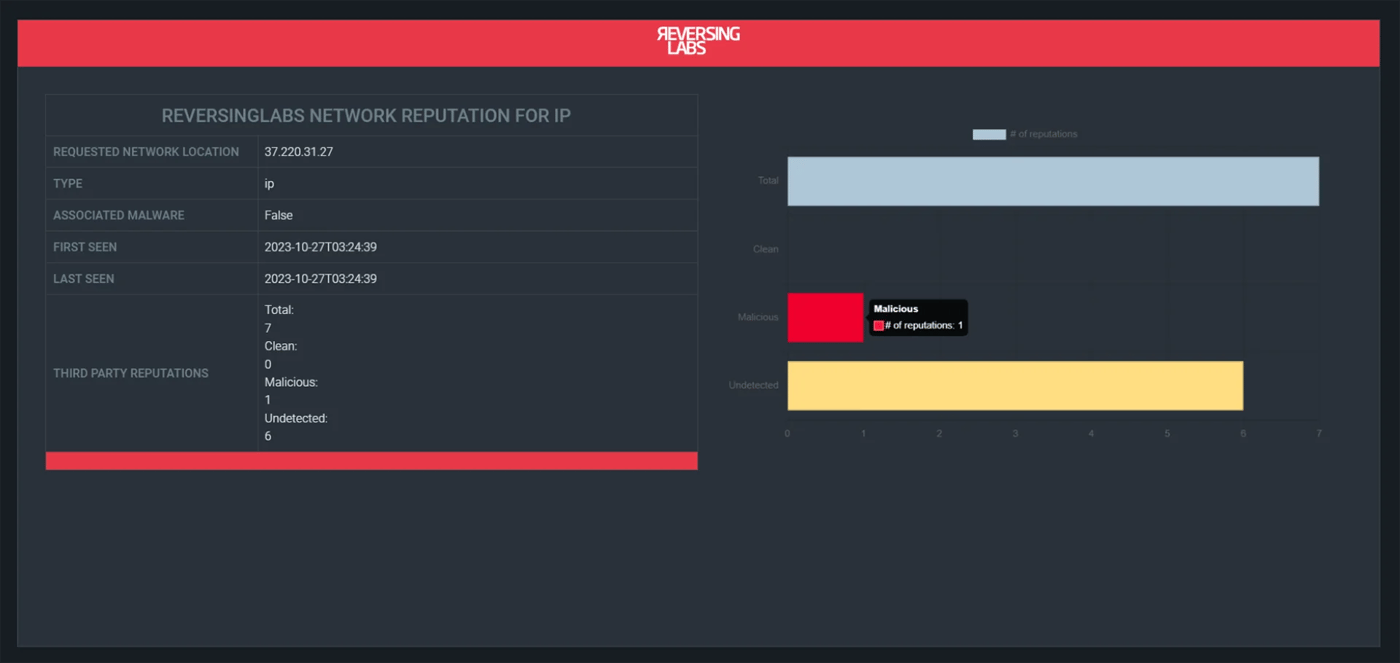
It is easy for analysts to gain insight into the reputation of an IP address, domain, or URL by referring to the bar graph that displays classification values from third-party analysis engines. Additionally, if TitaniumCloud has detected any malware samples related to the indicator, a simple True or False value is provided for quick identification.
Playbook use case: Artifact enrichment
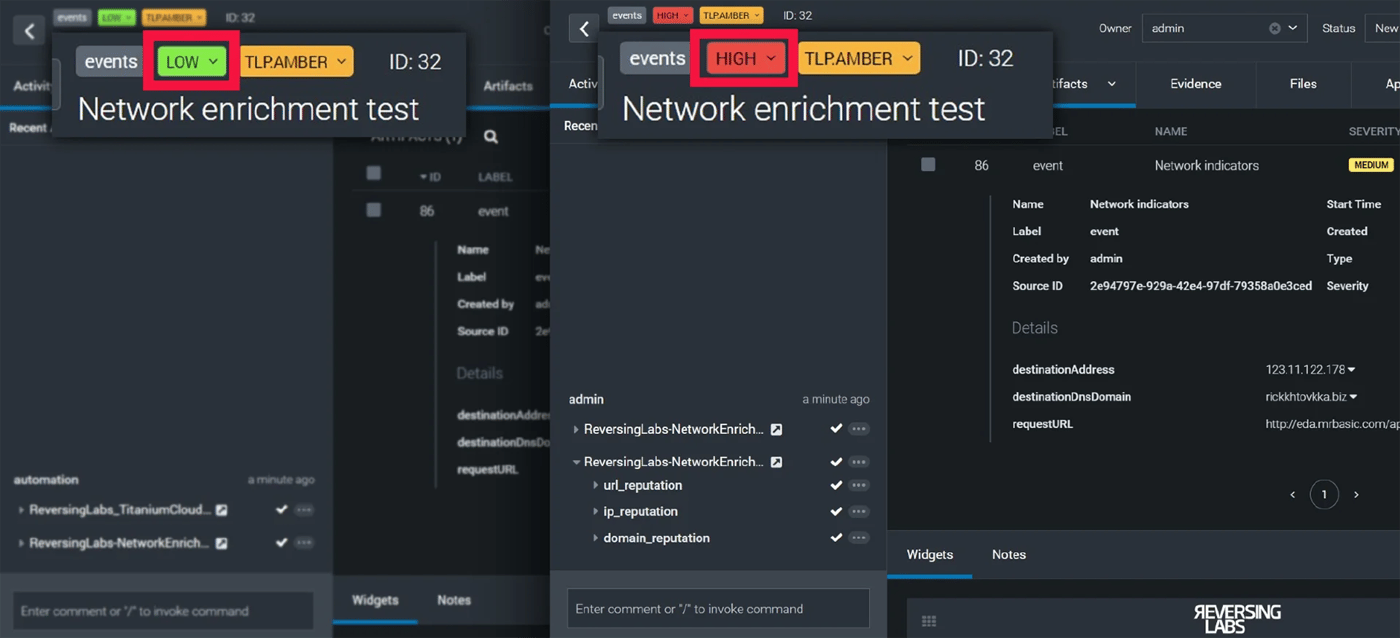
This is a simple enrichment use case that will use the network reputation API to enrich all network indicators in a container. If any of the indicators are classified as malicious, the playbook will automatically update the severity of the container to High. Here’s what the playbook looks like when it’s finished:
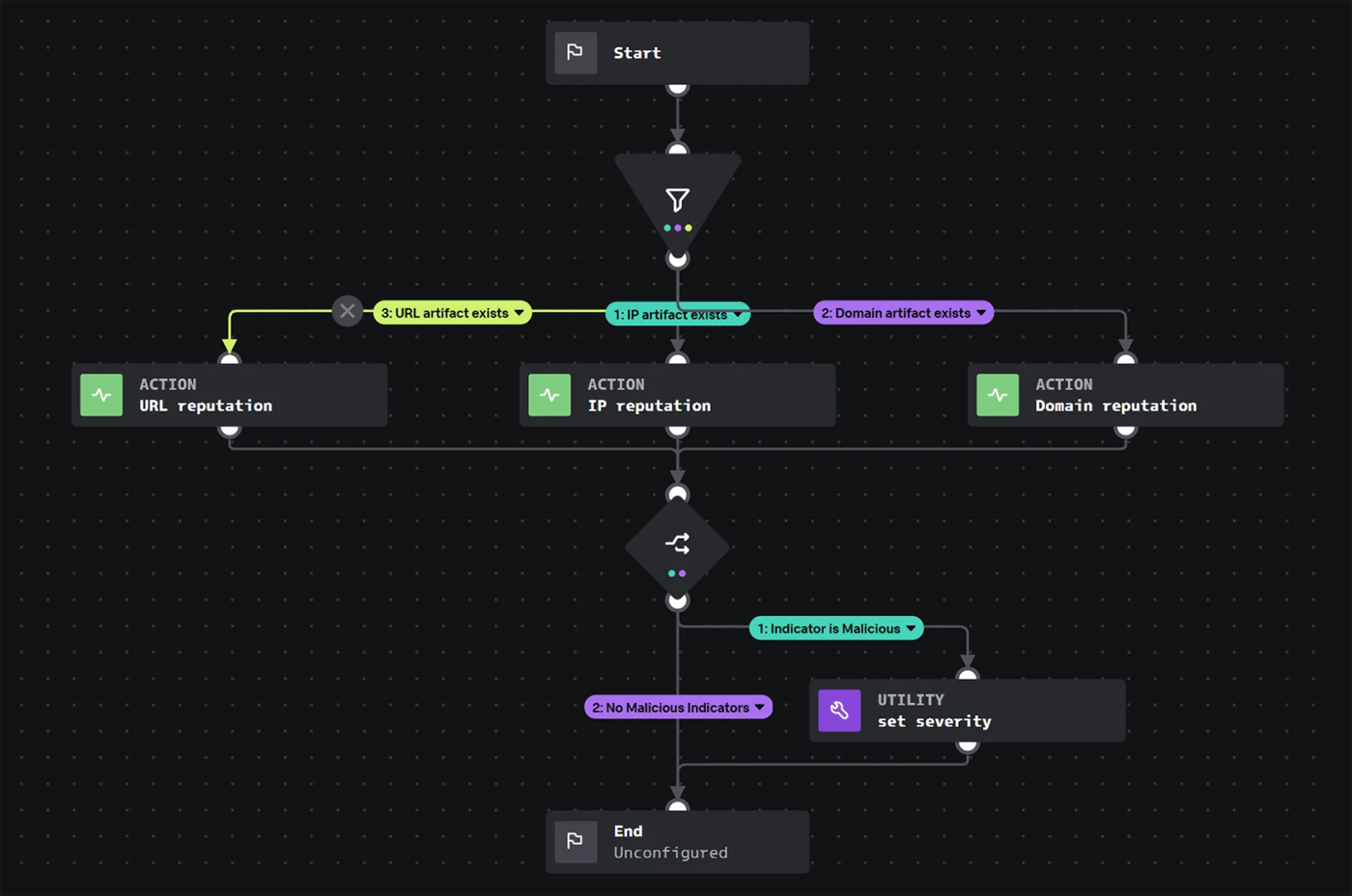
The steps are pretty simple. First, create a filter that checks if the relevant artifact fields exist in the container:
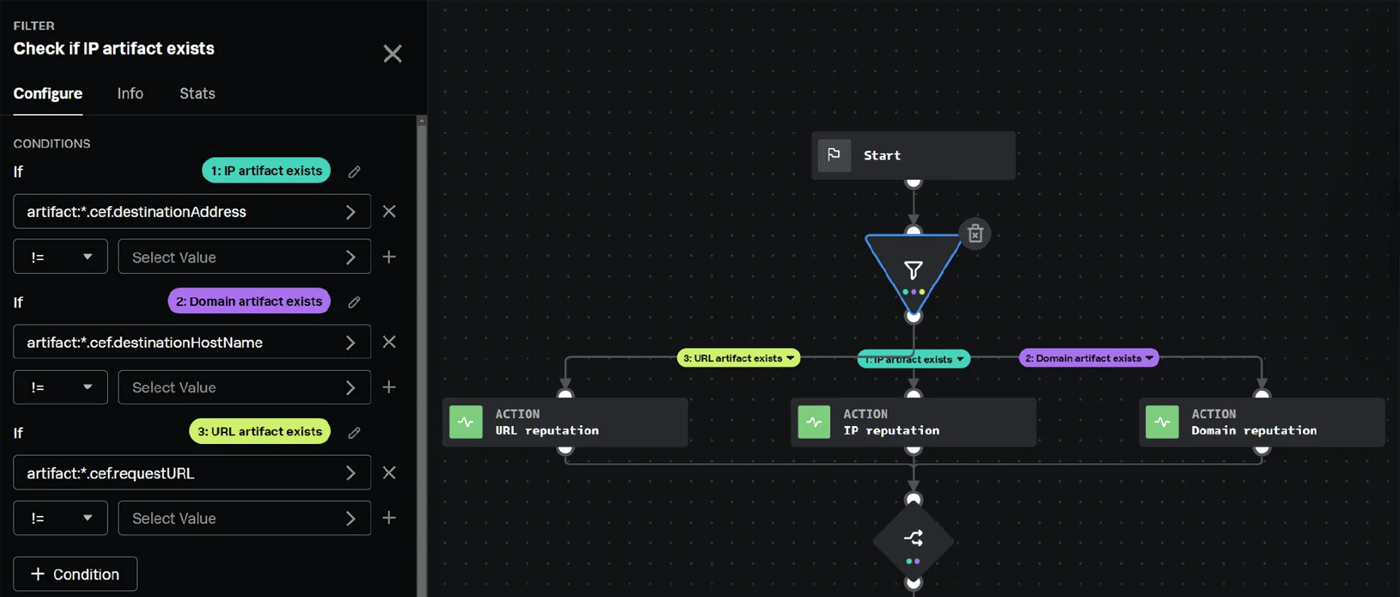
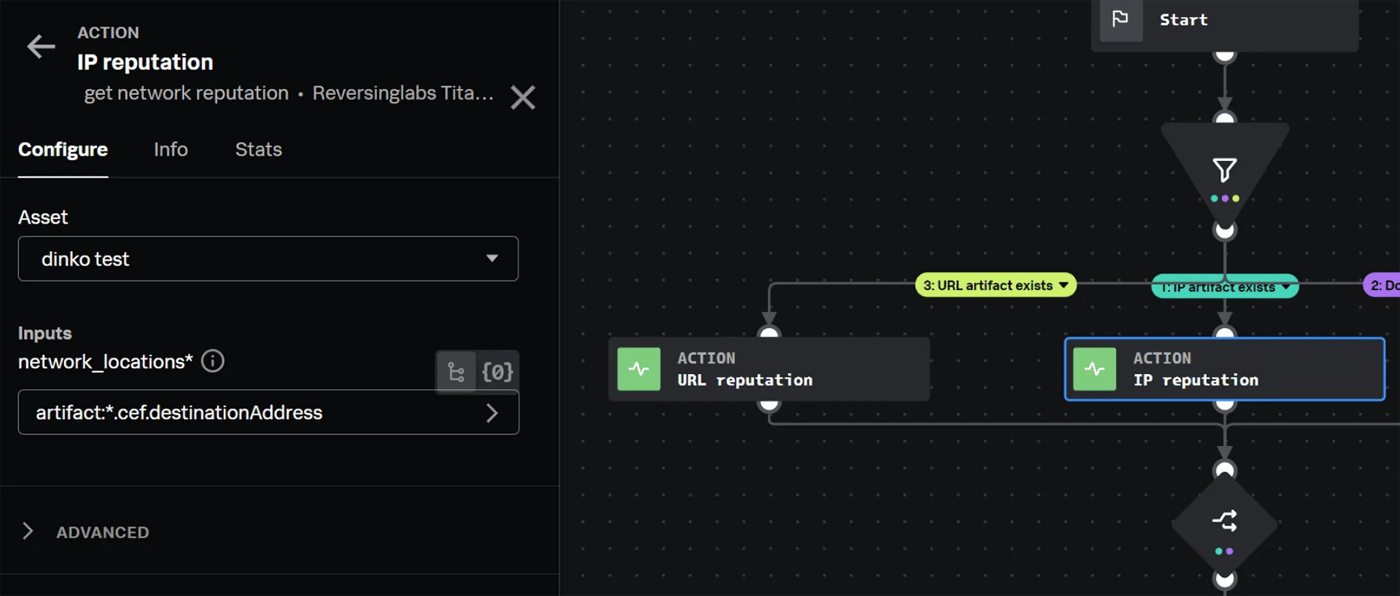
By setting the condition to equal to true if the value of each artifact field isn’t empty, you can save on API calls in the event that the associated field isn’t present in an artifact. The next step is to call the network reputation action for each condition, using the associated artifact field as the network location input.
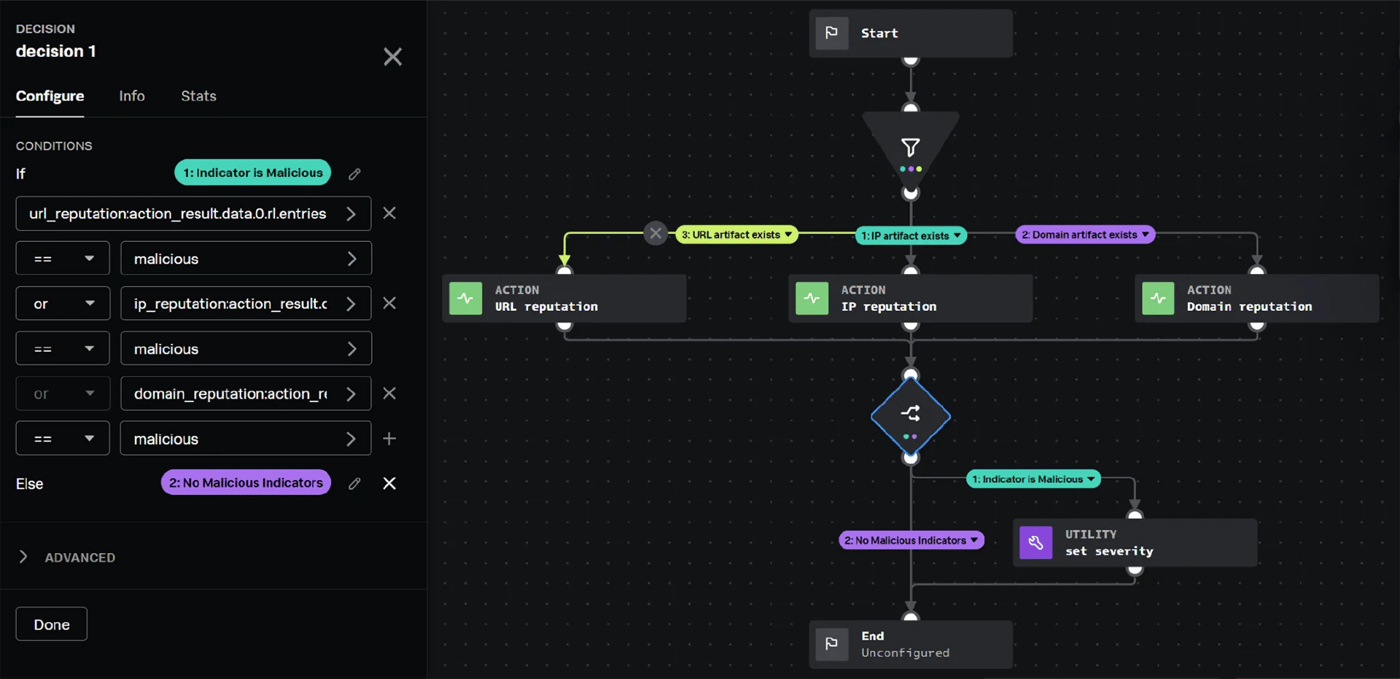
Next, add a decision step that checks if the classification value is equal to malicious for any of the reputation lookups. This can be accomplished by providing the classification value from each of the previous “get network reputation” actions as input to the conditional:
<action_name>:action_result.data.0.rl.entries.0.classification
From here, add another action that will set the severity to “High” if any of the indicators are malicious, and do nothing if none of them are malicious.
Using an enrichment playbook like this is a great way to help improve your SOC team's efficiency by focusing on the validated threats.
Playbook use case: IOC harvesting
By utilizing the "get downloaded files" action within the enrichment playbook, it is possible to expand its capabilities even further. This action checks in with TitaniumCloud to determine if any files associated with a URL have been previously analyzed for malware. This feature is particularly useful for identifying additional indicators of compromise and for blocking potential threats.
Simply adding the “network_locations” value from the previous network reputation action as input to the “get downloaded files” will return all files associated with the URL:
In this example, the supplied URL is hosting a single malicious PDF document. TitaniumCloud has already analyzed the file and determined it to also be malicious:
<action_name>:action_result.parameter.network_locations
The playbook in the previous use case can be further modified to take advantage of Splunk SOARs orchestration capabilities by integrating with your SIEM or EDR tool to check for instances of this document in the environment. The screenshot below shows an example of using Microsoft Defender for Endpoint’s Advanced Hunting query action to look for the associated SHA1 file hash:
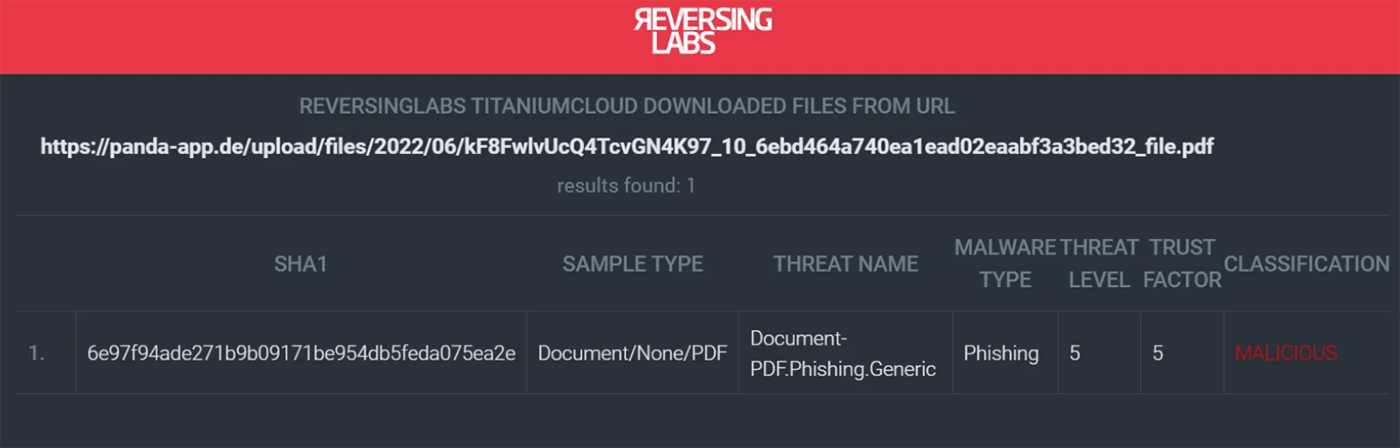
The rest of this example playbook continues along the same path as the previous example by setting the severity to High if any indicators are malicious, but you can use your imagination to add additional steps that are relevant to your environment and workflows. Consider taking actions to block the discovered indicators, send the indicators to your TIP, or even quarantine endpoints if samples are found.
Conclusion
We hope that SOC teams will find these new network reputation features useful in detecting threats in their environment. If you are an existing TitaniumCloud and Splunk SOAR customer and would like to use the example playbooks demonstrated in this post, see the playbooks in our Github repository.
Interested in learning more? See the demo for how you can get access to TitaniumCloud for increased SOC efficiency.
Special shoutout to our senior integration engineer Dinko Jakovljevic for making this release happen!
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.