Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
From the malicious nullifAI campaign on the AI community Hugging Face to the two waves of the cascading Shai-hulud worm, software supply chain threats came to the fore in 2025 — and became a top priority for both application security (AppSec) teams and CISOs.
The biggest shift came as threat actors advanced their attack methods, moving from simple approaches such as typosquatting open-source packages to direct targeting of elements of the software development lifecycle (SDLC).
These are the core findings of ReversingLabs’ Software Supply Chain Security Report 2026, which offers an assessment of last year’s software threat landscape using RL Spectra Core’s rich malware analysis capabilities.
Here are the key findings from the Software Supply Chain Security Report 2026.
Download: Software Supply Chain Security Report 2026Join discussion: Report webinar
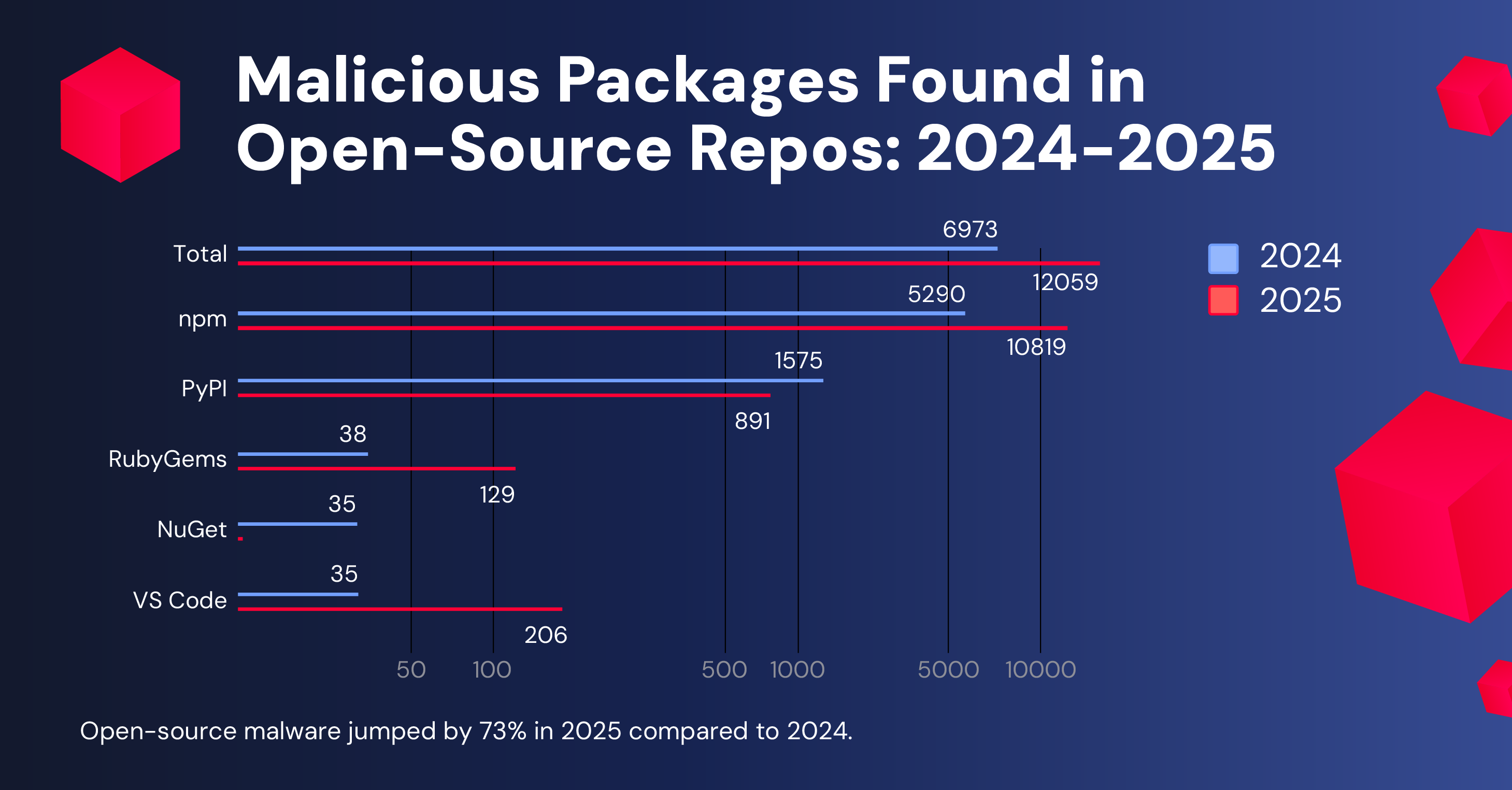
While this year’s Software Supply Chain Security Report recorded a decline in the discovery of malicious packages on open-source software (OSS) repositories Python Package Index (PyPI) and NuGet, the npm platform was a different story. In 2025, npm experienced a more than 100% increase to more than 10,000 (10,819) malicious open-source packages detected, accounting for nearly 90% of detections across various OSS platforms.
This increase not only included low-barrier attacks that RL researchers have been discovering for years, but also sophisticated campaigns that compromised the most widely used packages. Those included a first-of-its-kind, self-replicating registry-native worm dubbed Shai-hulud, which compromised close to 1,000 npm packages over the course of two separate campaigns.
Among the OSS packages compromised were widely used modules such as @ctrl/tinycolor (~2.2 million weekly downloads) and @asyncapi/specs (~1.4 million weekly downloads).
OSS maintainers — who often volunteer their time to uphold projects depended on by millions of developers — were also targeted via npm. In one case, Josh Junon, the highly respected maintainer using the handle ~qix, had his npm maintainer account hacked via phishing. Shortly thereafter, security researchers identified malicious code updates to packages that ~qix helped maintain, including five of the top 10 most widely used npm packages.
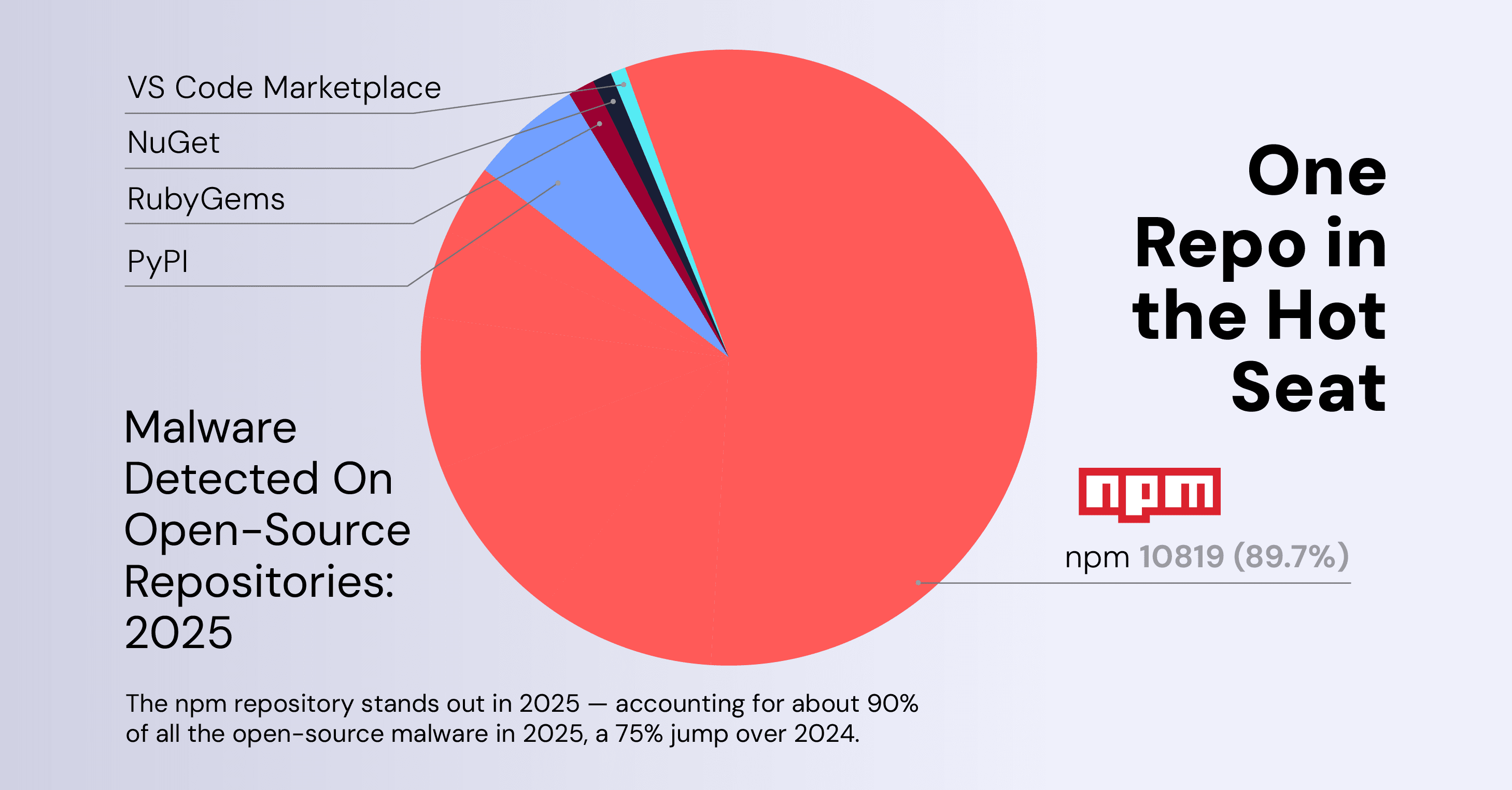
An important area of concern arose in 2025: the abuse of developer tooling — notably repository and CI/CD infrastructure. This marks a rise in sophistication and effort among malicious actors, who before had mainly focused on easy-to-grab, low-hanging fruit opportunities. Much of this newfound sophistication was targeted at Visual Studio Code (VS Code) Marketplace, a Microsoft platform that offers a source-code editor for all operating systems.
The RL research team discovered several malicious campaigns on VS Code Marketplace in 2025 that deliberately took advantage of the platform’s features and processes to infiltrate the developer supply chain. In one instance, RL discovered a loophole on the platform that would enable a threat actor to reuse the name of a legitimate but discontinued VS Code extension in order to upload a malicious one. Also, researchers identified that a threat actor abused the GitHub pull request feature to turn a legitimate and benign extension into a malicious one.
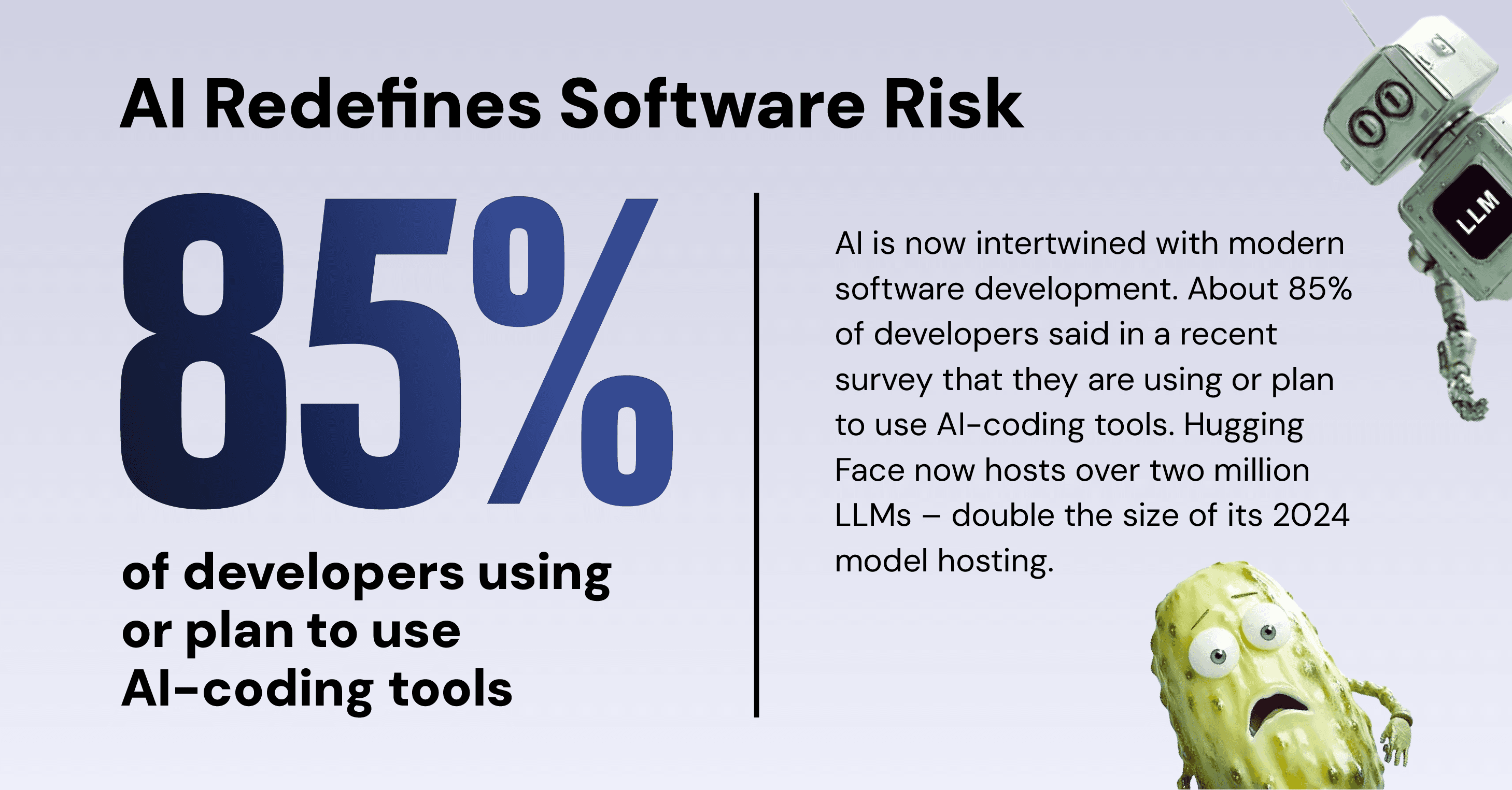
This year’s Software Supply Chain Security Report would not be complete without reflecting on how AI has fundamentally changed software development – and software supply chain risk – in 2025. With the rise of shadow AI in the form of AI-assisted coding and the popularity of public platforms such as Hugging Face, it became clear that enterprise governance is needed to manage the rising risks from AI.
One incident RL researchers discovered this past year showed how AI can heighten risk. The malicious campaign took place on Hugging Face after threat actors exploited the Python ML model file format known as Pickle to distribute malware. RL dubbed this new technique “nullifAI,” and it proved a fruitful one for threat actors, who used it again on PyPI to target users of Alibaba AI Labs – demonstrating that malware-embedded ML models have entered the threat landscape.
Other threats linked to AI expanded in 2025. For example, prompt injection, which is a form of model corruption where an attacker attempts to manipulate an AI model, was listed as the No. 1 threat in OWASP’s Large Language Model (LLM) Top 10 list.
And, with model context protocol (MCP) servers booming in popularity, researchers discovered the first-ever instance of a malicious MCP server spotted in the wild — and distributed via npm. The malicious package, postmark-mcp, showed how the fast evolving MCP infrastructure can be exploited by attackers to extend their malicious reach.
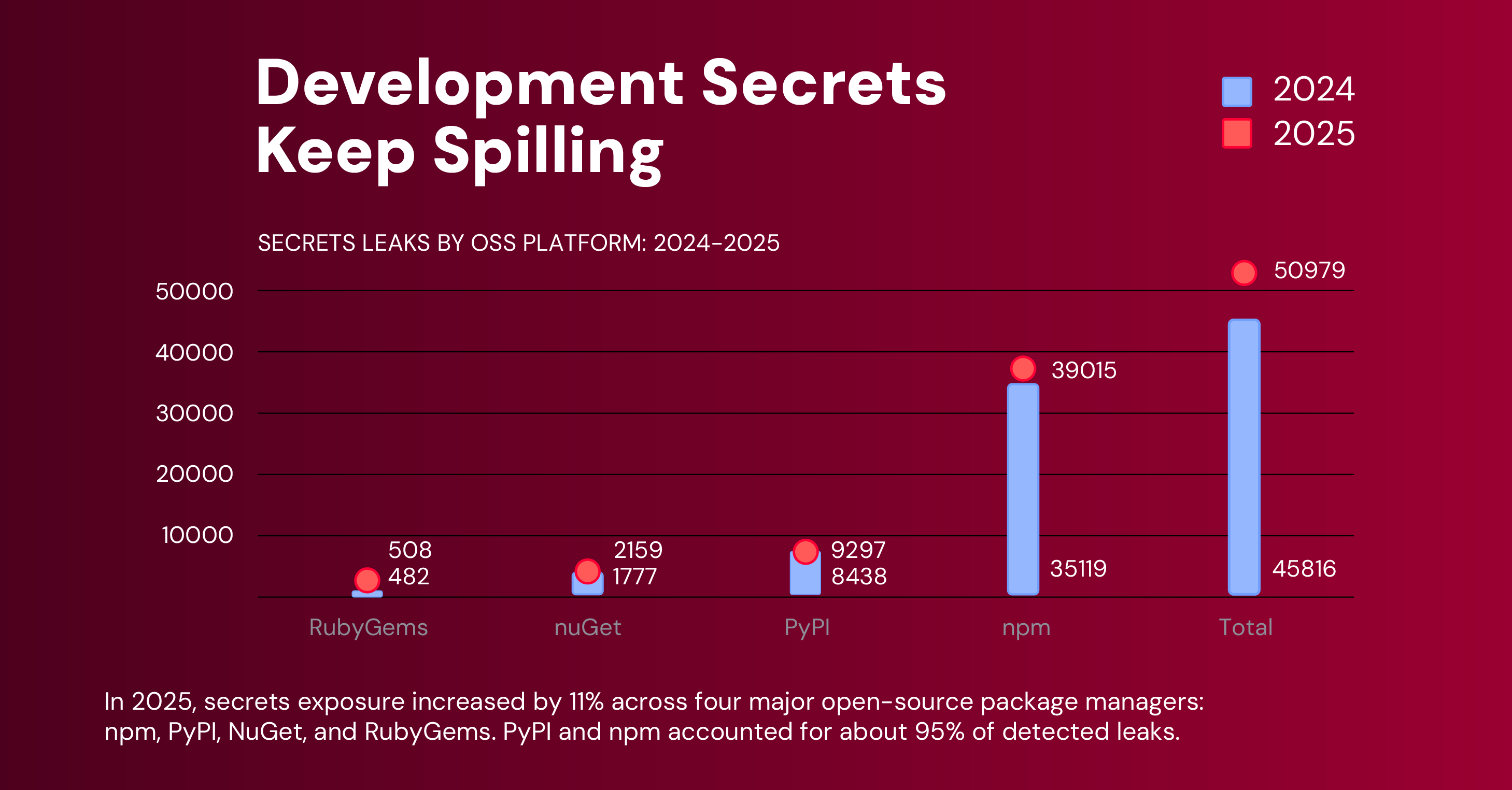
One trend that continued from last year’s Software Supply Chain Security Report was the exposure of software development secrets, which are used by threat actors to infiltrate high-privilege infrastructure. In 2025, RL researchers observed an increase in secrets exposure across npm, PyPI, NuGet, and RubyGems, with the first two accounting for about roughly 95% of the total number of detected leaks.
As for the kinds of secrets most often detected, private keys, web-service API keys, web-service access tokens, and embedded private keys made up more than three quarters of all leaked secrets (79.8%).
Attackers also took new lengths in 2025 to make secrets theft a key part of their attack paths. Both waves of the Shai-hulud worm used this strategy, with the malware “migrating” private-code repositories belonging to compromised GitHub accounts to publicly accessible repositories, making the secrets hardcoded within the exposed code publicly accessible.
A prior trend that expanded in 2025 was attacks targeting cryptocurrencies and the infrastructure that supports them. Also concerning, several of the incidents seen this past year employed tactics researchers had not seen before.
One particular instance involving npm showcased this increase in skill: two packages — colortoolsv2 and mimelib2 — abused Ethereum smart contracts to conceal malicious commands that installed downloader malware on compromised systems. Smart contracts, which allow users to interact with the Ethereum blockchain, became a tool for delivering second-stage malware to unsuspecting victims — via a tactic never seen until RL researchers discovered it.
Other OSS platforms experienced their fair share of sophisticated compromises targeting crypto. PyPI was hit with three separate crypto-focused attacks that targeted Bitcoin and Solana developers. Also interesting, RL discovered a set of 14 malicious NuGet packages, each with a malicious payload that either stole crypto-wallet credentials, crypto funds, or OAuth client IDs and client secrets.
RL’s Software Supply Chain Security Report 2026 notes that while threat actors continue to go after easy targets, their opportunities for exploitation increased alongside their sophistication. Threat actors are now working smarter and harder, taking advantage of overworked developers, lax security protocols, and innovative yet unsafe development processes (think AI-powered vibe coding).
Such developments make it clear that the trust we place in software ecosystems is being exploited. The takeaway is that defending your software supply chain is going to require a shift in mindset away from implicit trust and toward continuous validation. In 2026, both software producers and end-user organizations must recognize that the trust model is broken, and gain the ability to inspect open-source and proprietary software.
While the risks highlighted in RL’s report are real and growing, so is the industry’s collective ability to address them. The Software Supply Chain Security Report 2026 serves as both a warning and a guide to AppSec teams — and is a must-read for CISOs looking to better manage software supply chain risk in 2026.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial