Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
In the course of our work analyzing malware samples submitted to our Spectra Core platform in recent months, ReversingLabs (RL) has identified four, new remote access trojans (RATs) that utilize the Discord platform for command and control (C2).
Minecraft RAT, first noted by X user @malcat4ever, is operated by a threat actor group who call themselves "STD Group." They also operate a series of very closely related RATs that use Discord as their C2 mechanism. The RATs are so closely related they may be the same code base, just rebranded. The two other RATs are "UwUdisRAT" and "STD RAT." The malware is written in C++ and incorporates a ROT23 cipher to encode a Discord bot token that is used to connect to the C2. The “Guild ID,” which is a Discord Snowflake Server ID, is hard coded in plaintext in earlier samples.
The fourth, Propionanilide RAT, shows the progression from a single payload to experimentation with a packer. The code base splits into two distinct files: A payload and a packed executable to distribute it.
Here's RL's analysis of four different RATs operated by STD Group, with file indicators, and two YARA rules that teams can use to identify the latest of the RATs and the custom packer.
The oldest samples are called “UwUdisRAT” with the earliest known PE header compilation timestamp being November 15, 2024 at 23:06:51. This sample contains one of a set of PDB path strings. In the path is a Windows user account name: "Digital." Additionally, a string found in this sample is "AnyDesks." This string, along with the username "Digital," is also found in an older and fairly prolific campaign of .NET malware. Most of these earlier .NET samples have the same filename: "AnyDesks.exe." Because this other malware family is quite old, it requires additional research by the community to fully understand if it presents any connection to STD Group.
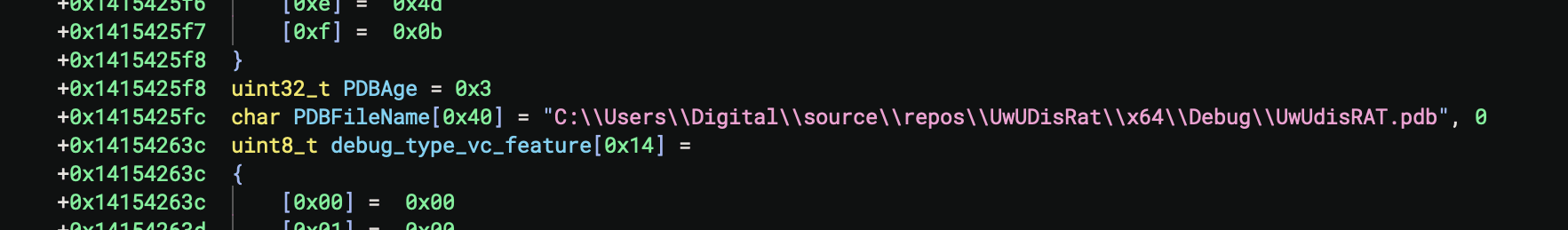
Figure 1: Program database string containing username "Digital."
One early sample compiled on January 30th, 2024 included a calling card string. A calling card is something left in the malware sample meant to be found by researchers or other adversaries.

Figure 2: Calling card string.
The earliest sample of STD RAT was compiled on February 14, 2025 shortly after the last observed UwUdisRAT sample, which had a compile timestamp of February 8, 2025. These samples both contain an unencrypted Discord token and server ID snowflake, which are Discord credential components.
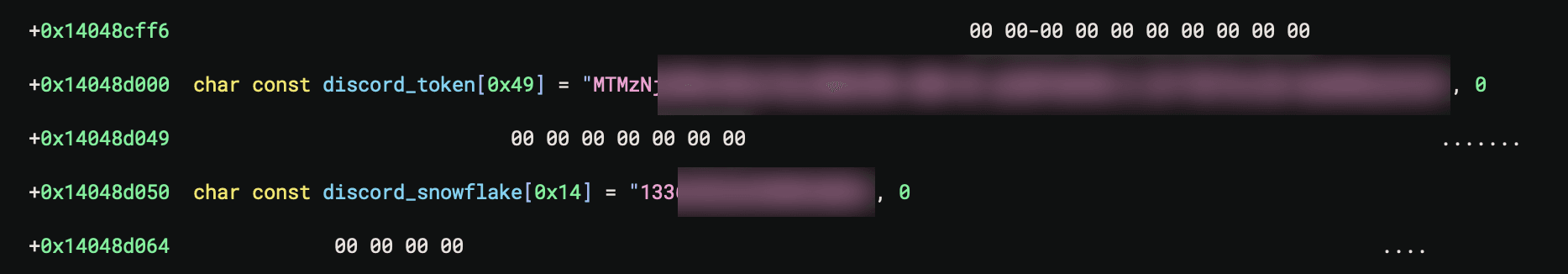
Figure 3: Discord credentials.
Later versions of STD RAT use a ROT23 cipher to obfuscate the Discord credentials. A function for decrypting this cipher is provided at the end of this blog.
A sample compiled March 19, 2025 is the first observed example of Minecraft RAT. This RAT is being operated alongside STD RAT and UwUdisRAT. This variant contains an obfuscated Discord token as well as an embedded regular expression that is used to match the character pattern of Discord tokens.
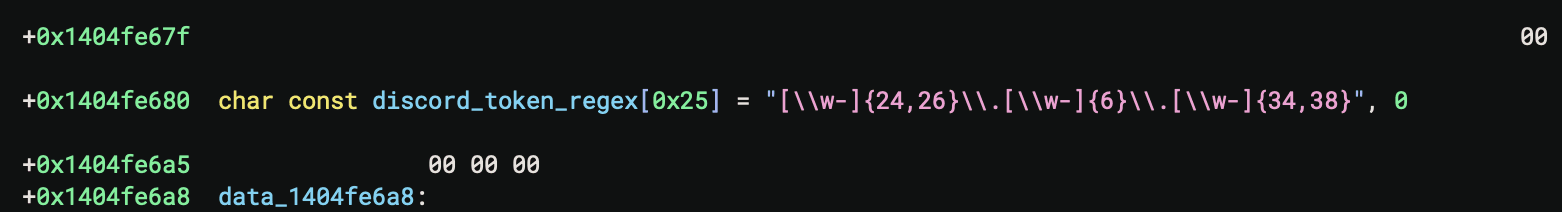
Figure 4: Regular expression for matching Discord tokens.
Most of the recent samples of both STD RAT and Minecraft RAT share a distinctive mutex string.
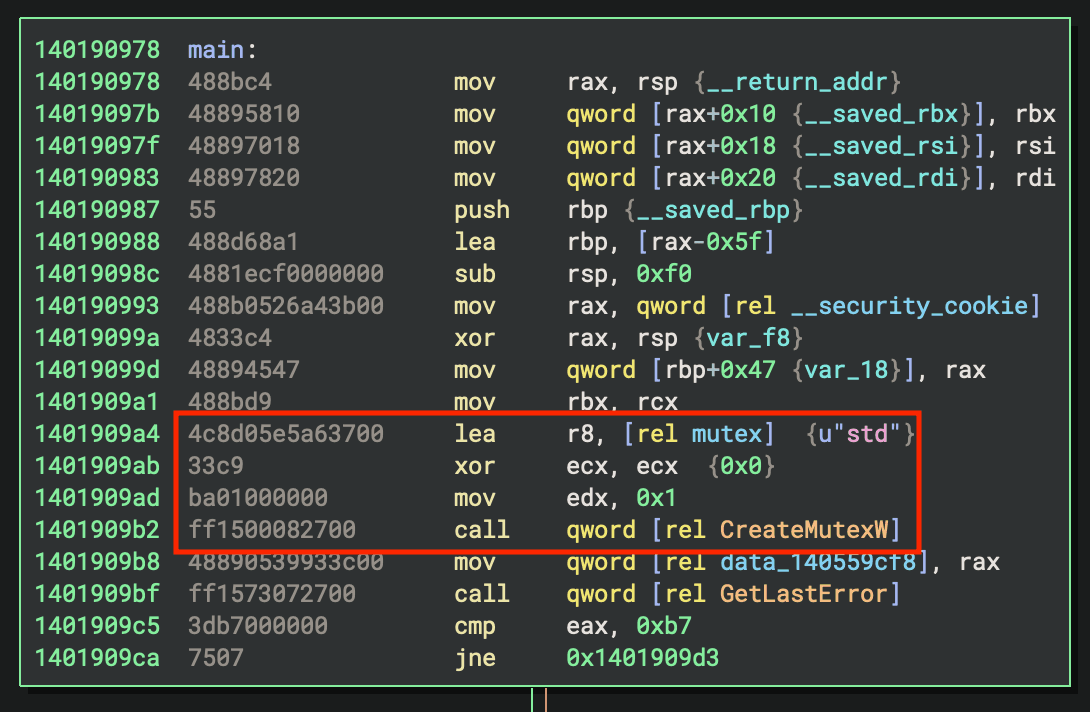
Figure 5: Function call to set mutex string "std."
There are two locations of difference when detecting this mutex: wide string or not, and the order of the instructions used to set the CreateMutexW input parameters. However, only three of the four potential combinations have been observed in use in the malware family.
One example of a dropper for the Minecraft RAT campaign was observed with a compilation timestamp of May 30th, 2025. RL Spectra Analyze extracted the payload from the dropper as shown in the Figure 7 below.
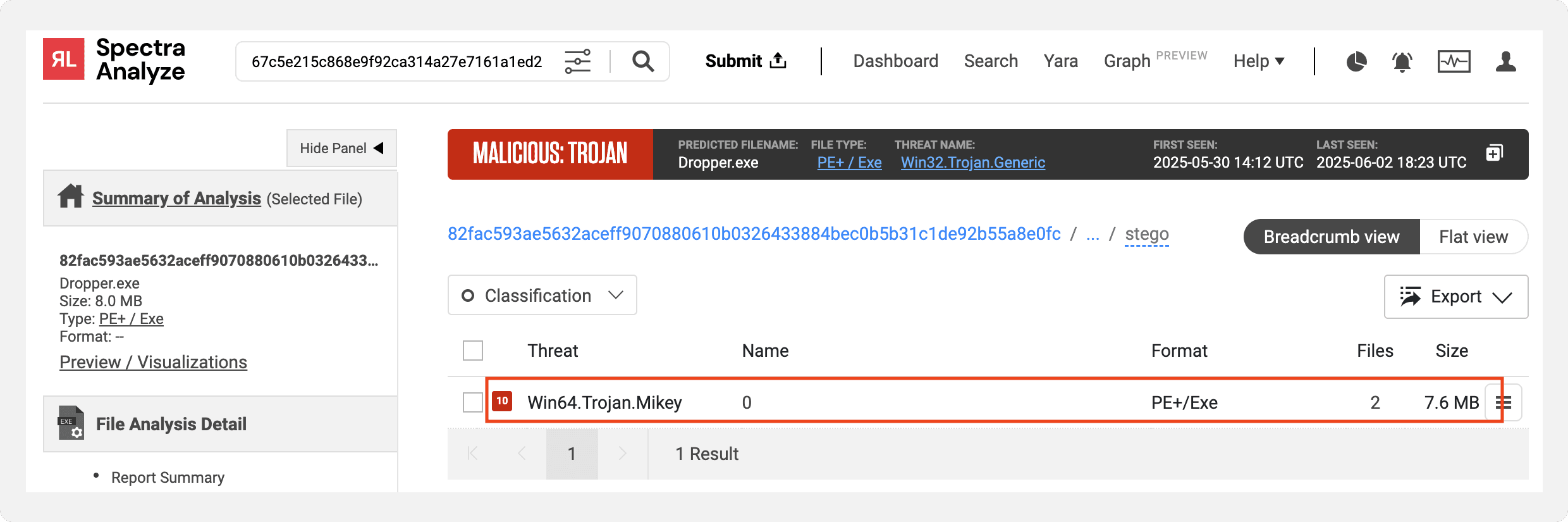
Figure 7: Minecraft RAT payload extracted from dropper by Spectra Analyze.
In more recent Minecraft RAT samples, the adversary has started using stack strings to obfuscate the location of the Discord token. Figure 8 shows the stack string on the right. This token is additionally encrypted.
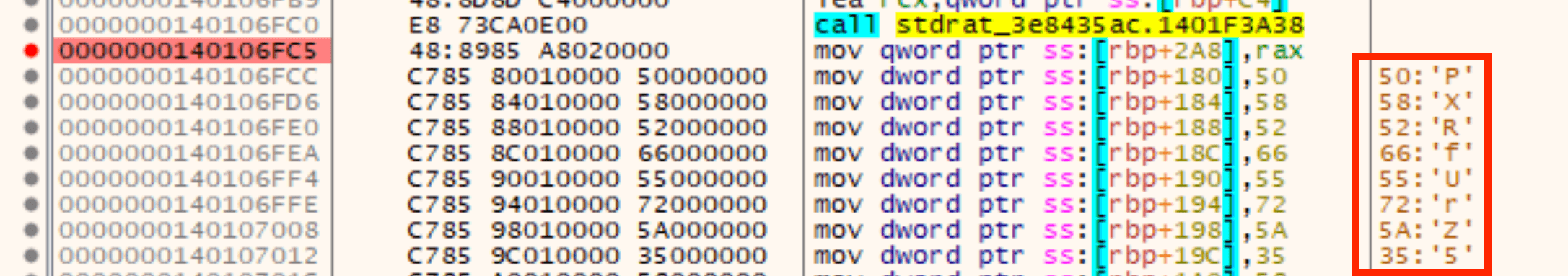
Figure 8: Encrypted Discord token obfuscated as a stack string.
In samples that employ a stack string with an obfuscated Discord token, another decoy string that is formatted to look like a Discord token appears to be loaded in the location, as can be seen in Figure 9 below.
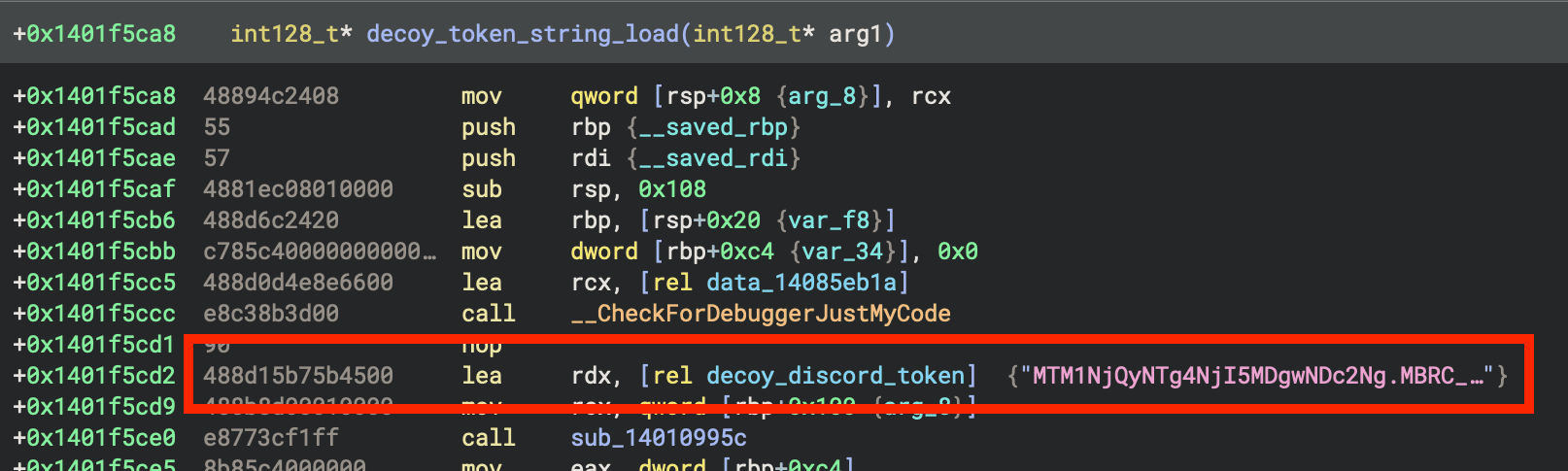
Figure 9: Decoy Discord token string.
However, the code block where this string is loaded is never executed. The call to this dead code is near the location of the decryption instructions used on the real Discord token. In Figure 10, the block on the left in red contains the call to the block with the decoy and the blocks on the right in green are a loop that decrypts the real token.
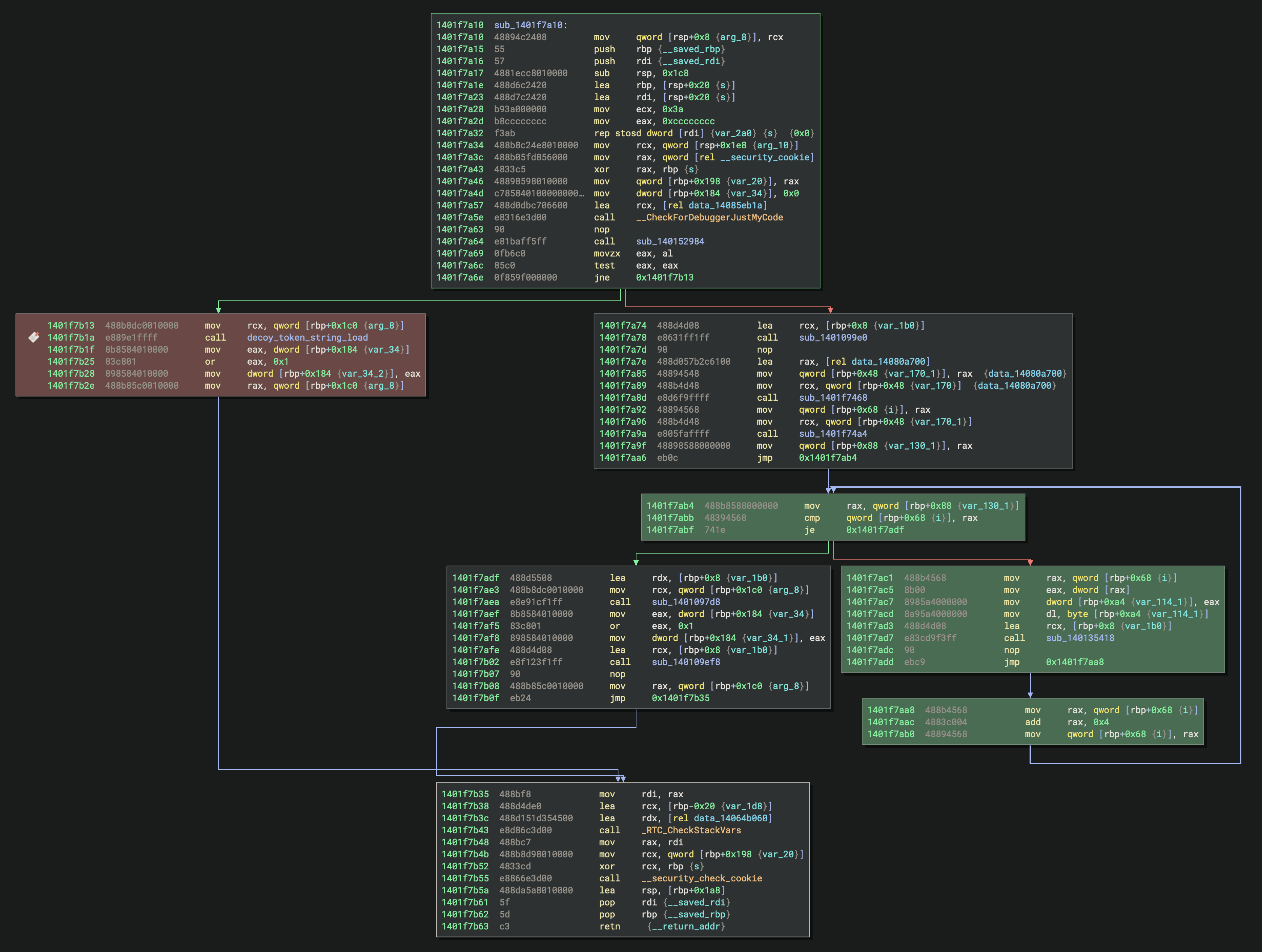
Figure 10: Decoy block vs. real decryption blocks.
Early builds of this most recent RAT used a distinctive main function that ran the Discord RAT functionality. However, later builds of Propionanilide RAT with almost identical capabilities dropped this main function for a much simpler main, which initialized the RAT and then entered a loop. The previous main function was then reused in the packed samples. The unpacking function was run in the same location that the RAT function was in previous builds. This packer is called “Proplock” or “STD Crypter” in certain versions.
The packer uses XZ format and LZMA2 compression to pack the payload. In the most recent builds, an additional layer of rolling bitwise XOR encryption is used outside of the compressed XZ format.
This adversary is also associated with a set of one-off and test files of various types. The following are the ones that we have observed. The spelling of “theif” here is as it is spelled in the malware sample:
In addition to the above, an earlier campaign of .NET malware overlaps with early samples of UwUdisRAT. In figure 11, we can see the string "AnyDesks" used in the main function of the very earliest example of UwUdisRAT. Here it is being used as a window name.
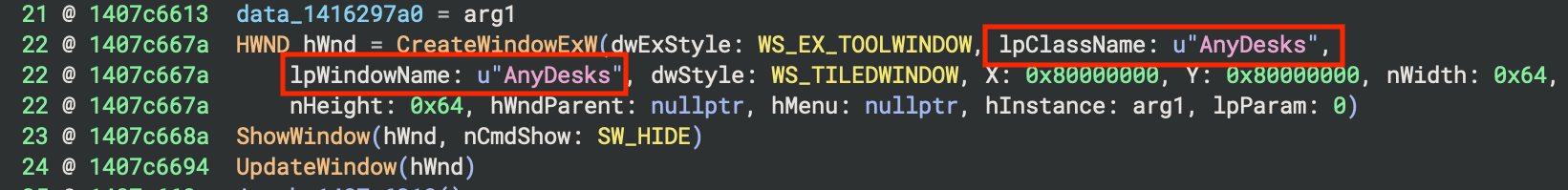
Figure 11: "AnyDesks" string window name parameter.
In Figure 12, we can see the local results of an advanced search query on Spectra Analyze showing files with the filename "AnyDesks," as well as the username "Digital" in the program database path string. This advanced search result reveals these older samples and campaigns.
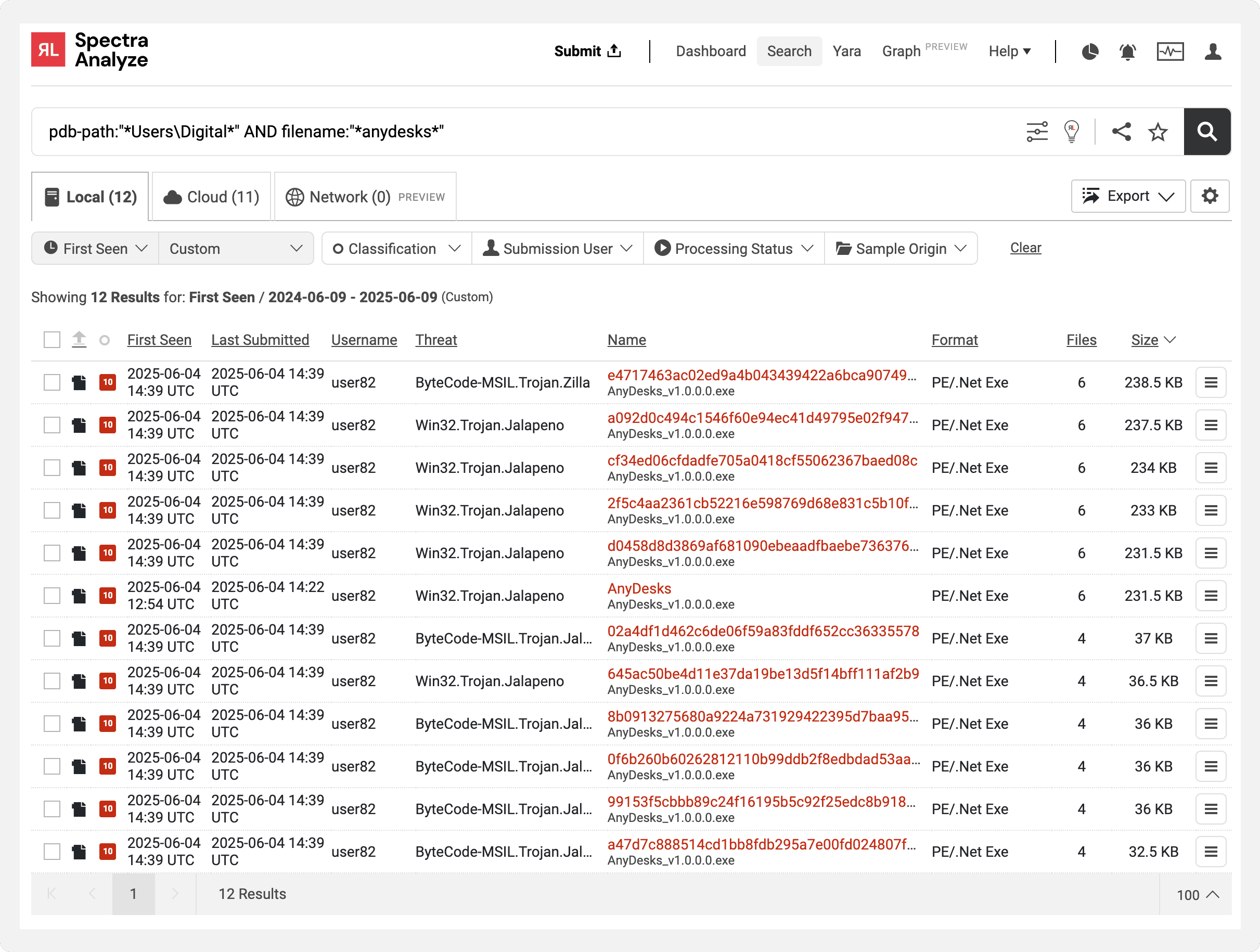
Figure 12: Spectra Analyze advanced search results with older related .NET campaigns.
Continue reading below to find the file indicators for all four RATs, as well as a Python decryptor and YARA rules.
Packed Samples
1a1d3d897d0b6eb8836e15359fc600b3790a3c621a3cf0d0cbd23c88e9e8af69
1ca659cfe2f40695a250ca3c6287ed3691a268d6f7fbffbf83a5b0bb0ed0a528
1cb3e126db89fa922616d5bee319775b366eb850948a14f29d1a6cb96866b63c
30501b866ca2f0c9a8db01ee842bd5a9527e413bf1fb52a39c70f21d74d337b8
307c6c77cb0c50ae427fb316ab8f2c1362715b6cabf43391d36cedc3f1a3e846
36a6e50c5fef6ec99151969ff90fbeb6dde974a37a0d3eb5ec4df5ffe3ca260f
3d3be605ba3d6532040023aca9461acc4b711889fc4411fa5ecb661cbf0ff5d6
5eb04ef949abaf560eba8d235aa00c8eba2e349c6201571961c904a23a778f1c
62a10917e3da538fe4d482f37b7939b54a08396665f484fe13accb3db9e64427
6603e7a118494282fa684be85dabec4c085492cacbd95c78cc45c30d4abc1d97
6eba18e9a1f0354d81fd124da7a716a587678821e855155a2bb1e2bb93713758
70fc6bed8574c2c2d0bc8f753d8d62430224b08bdaa26b8152d7756961c03a09
8e949697effe4c46daf0c7e0d00a5f2081f9e457fc8053826677d83ca769e363
90260da07172586c4e8a8653077edb8be7f846cc9fd5db2e18bce1aa521e565d
97a05771adc063f3223354ef4ea2956abce095a9ed56ecd40761abea322250c4
97aab6ebd8fac8a2ec7c48c06b886103ab8cf98a9760f60c8071a485c77c1fc8
9ac5bc1bc05457941d96bc5be8ad4c1dd5258fe337e5bdfa27c649ea4bbc49ae
a57025157be76361ec8fc1dce54b8964538f32f620cb22d5c8848e24978eaec6
af03448c80d22769103fb0025943eb0b0ef6f7c0acb3df170c78fe1de08bcb41
b2a5b626583786c84d7ebea403700b2785907e1766233c5a49d485ed46dface9
b3f7dee0b69c1f0fd8512cfcd673fa5d928e8415f356de7d2a598b9fdc0a31e6
bc9f0bec077a6f406191b035e5ae35246c12ffa7f36c3424002dbf0e01e49820
bd60d56fc8cd50b403f3171a2bd5ff540d9e741d9967297af132448b5dafbbf5
c3abd4e97d004df3094d44888dc19360333f5981afe2d0b85b80fff47c4628ce
d3346bddc69913ec98838fdbd63cb75a29fa9353e27be8ede9d8dc4fb9f40b42
d3446ac50fcdddb11c3b1d334e905b5823a43cf7bee690e666f0d0f624de5f08
d6f6947b56d4b1d6dc524b7940c7eac7f13930371d37347b77534c038c20140d
e8c4e84db1ccecb62499548e40393979f23ef3356b22a61bee08ebe8f5ef03c1
ea950729734765ece6fb230a65b110e4fb0d60b108a52459e2fc3854fd5547ff
f3ea2e40da7c674312ef379275b36777db95da21564d9bbb868f919802a58609
fcfbe3559b24a0468785f0d84880c9371b41bb9893fa74f69e130908dc6dd562
ff70fcaf5bf42d19f9eb15bcf7a8227f6af22c19eee1b034b427109960b52e37Payloads
1a4382141f9d4910a172089048157052a053d3ae81fd2ae660632b849d606f2c
202083aae976ab71a75d2d185e918430128bd845d125e55395617bddcc1d01e7
2232a2ec8a45c25ac04afbc38e3fd41bc9024033e1b3ed93f0422cfc6a84344a
2c105c535af48b11d568fb1e718ab172c0346937fd96b3b8039aaaf617edcf8d
340228a3396e378880837445c46bf2636d3973848a9513b877fb2bf1c5f4ffa3
35f24e9c2b1f349c42495b0b5f4d9d77c1fb9ef0a5bcd8a30e85966262e3b00c
3867ee71602b654d1f127901670003f06c699ab84edb8b1c63f8211045388d74
39b73542cd04fb0e74d788256653406a60830078a794b13bbab22aee111161d5
5a1df5702683628aac4657bfd80ed7571a746fa5242dc6a353a2f6830d027d53
64251424d1417e14d4a220d2cb30500961f659cd8f7969209a9bbe45d4cd312a
646fa42f3f05133345c9fc9cc7f8d4b4b1188af73415140604d9eb95e4ec905a
6a987d918f400dd3c0840917845743f8eedc0c83efc5a9e7089bcb09169dc606
73f310328bc78edaa86e4d6519e192af6bbabbf80591a57eab30dbd0d4a9002e
81d6b086ba1f84cc146011300b7787b5586c4d85f04d9b10ba1685ca2c5836ac
9d524c8444ee8d6d66976c22456e7ebf54395e53be35c5aa69e180f6f5dce74c
a618a75488fb3e0031fa15b89da4f118db452257b18907436ae3e64aa03f6877
c5863bdec64be0cb662efce9a8bbe2bde0b96132717d89c74ff0e566903143eb
d5c6e3ac4e471641995aa15c108d962f68e371caa5ad20d45d7f78e3732932d0
db7e53791455769db95e95e15c9a9ffc77ec1c4724b0c46e020478949996d097
f63fea79d76b97ff0e7c484c05739261c6beaef5cfd9eb93ad9e4fe5afc16aea
faf0556d746a0161f149db0ae8eb74a1dff4a114502360ca547920aad4cc9f3c
fb4c58ff61d8e43a744e3928ac0e0823ab1d106d8ef1f5171495c46eb3570780Tests
3fc319e3edd19c962179e8ed21bef5a9d2a32edd4f1b17677600505010a49611
49ff98529404bf03fd88341e6e9bc6eac54fb5f9c1bbfe46c3ea891533166de1
751ee3e15fd9454298bb0c3db714bd32b92b0e4e109e8218389d20de8bd935e2
94e2fe3928c4d3243a526a58bf3c854969d75dec7179adee967efa6b7f424d22
9a1d86487fd9eb3d36aaaa05afb382a1c37420491d61b3492c02a68eb50b709e
adbf546702820ead085f4f3b786993cf6e8a1f21fa55d9655bffccc70eec93c3
c901285252c58d1bbb0020a9def9bdb9a62a70df9a933199daeb694d21038b6d
ef2043b996d7ca0f5dc56c26e1b9299dbc732f879379e1b9845d523b683b3a8604589839ac2f6bd9ed2e958a6085c9070c6844e2c9abe15641f8befa70a65a98
061799cfc23d3689870ea6abed1f8cb5f595f63bb810ef7c829376c9c5cea921
0774e3488e6b762dc68c59c07576c6623f9066e38e4b0845e3b3a0fba8041958
0d0671b0da75b1730a3095d51b5f3f107ddbbbf1bac4369378cba083c414b886
12a01041764caa20c4f12f21531865ab73eac5539561f597adcb871b56e444de
13ea8800215e75c1427ffcbb1ab475d3cfdde7227d95688203f80fcd957ec817
142fb1ce5ee9b8ed3145caca2021da717ab546435f0303c63531a45522cf668e
1a6c4df56b01b53d31f5f263d96faa7c534c183ec59e6dcd14d7481ac1acc09f
1eabcc4e360b855521f0d3c5d3830daa169e81357dc8a109302ae9f76ffd45a4
2932b243514af400307955985d58dcaeae200b9d7c959146b60c93e2f2f1c485
2d90575dadcfebfb6599b17d70c8f9494819276629b116b4bb43515f90e827f5
36fcd429f3053afd1a3d80682b56216c0d24b4ec8b99fc943aadf36a64d4f35e
39866c5378fb9a7fcd22b8fdecc475e2cc7a2c91b57a953e514213a22fb5f194
3ae2fd48b95b8de8dbbbe1c3bbf80b89bd8885fa9a9a27e690eb808770338c0d
3b693725c879a30291408e01a82e6d8a433b4578206c84493b4898fc0ee49e72
400a9207d39e3eeb4256902a82ada6b78cfe43db5c53fe7e068c86b30e7d4461
41fcba17e81df0c852d70e6e2b13a8d3b163d70410dc05f737dcceab15fd4f2d
44122eb155dfb5a81f3d27999ff6f2a6bcba2bb8d4041a61c8553743871a1f89
4609455dfa0d1957c970bcfccbfbeeba78688f4b42ae6cf27aa6b3e43d3f08a6
48f10195a2d4dab6121f1dd2792e5958aeb2db454cf3276d90acc24fe74edc23
4aeeb684566572bf0b7f045c8a7b1a98d273767f6e0a8b76b9098ddc7a5301e3
5036e245217e91db237ba428be1e0ddeff71859a55a3cdc42db6e35be38661d8
510cd3b9de265e44ca4467833dc17336f2afdfd4df203e43bc51e85767e88702
58b0b01514ff9da571c18b0b8f91a7840884424811e21e4b19b8860d83b50a4f
5f30c71b5b83b3924cded96151a621b0292d6682d580861c95a916038aad9485
60b14a10d81a0253694003a2294f93ffb6d2c1efd32b644cd450fd0a8d8b6f5e
62652633076dd5e5a8ff6ef730bf6d0dfe01ffaf869395a5e3836f7b728b7602
69e2ff214cd59ffe3d58a07f53e6cb03cb7e610fc90b01635077a1612436e75c
6c87c3b522b1d84aef3f78a9d8099ecbdc8352e1b35ffc32436c90f228f825be
6f19308935915ff4b6b7d231f477cb90a31800671f2407a152d8547ffcfc9c9e
74537b0bebc09b7de8dcfaa72a2dcd28fc2a3d95a31f2f3f2671a18aab88e093
7464fa2a457d001dc7a3080391dfd1c9e33a8f43bdbcb8403b60b5e3d1c10229
772cba090376101576015e269f60cf50b2de1180aca84686307945b661ebc665
7d796e90c7b01e44220812e5a3e3ba32b0b3707b75491b3c81a23264616e5e70
7ed399614e5e234d32eadcc9513ce2001e4e09a81e8fa1f45fe9a93610a37225
8437f50e7fc6491d96ef41431f967fd9fde63525219f7fd0d9c9ff93b1fad3e3
89b0ffa674c8a2bb7636079a0c9b8505105bfdf4e0c76422aaeb5720423798e1
8be83c870b040890638e29798e7a7e2f77b2e298222785fb04653fd4d1943c95
92ab1a93499aae4c8b0c47476b24af5f1cf209f39857f654dc7e567e40f84c30
9437005de21d45f9ffa4d4a1f0989f42d1b513fa745213d76993c721b7f59667
99a56910caace53fd223710a10825683772d730ab11b41c0dbdf8ea50007edc3
9a4a2b8720cb6cbc16c6450a9d4f7e78b12406690ad77f72300029b5c0f852e4
9fb33b4a7acdd44c6d440560c8280024e72dfd0a6f8c8b1c83bcb4b7555b3c87
aeef6087b0d022bf8b103c5813c0bc0a5e964189583f03cfe55defc0c3bf2374
b0512b00c39de877b82417bb1aadaade779c1fb409284eb84da2ba8ebb2931a7
b4ec5581a655597ce432b1a4a161fc89cad73bad2c0bd2a09f155412e511b546
b8b68aef7ae26a5aae1e9d35a1cf2fb54b77307b48b596424683eeaed2343627
bed69afbdc147c31728bd79708c6056499c95edf731250493ca064de9c5f513c
c0d98ae50837044d61ecc88f2f1d9b74a35ba8e0898d3bdd80517323ba5fbfe4
ca54d10d45fcc04f8581f7c0c5a53b41f47858bd9ee6c224ee709b162cecdc05
cf37a6e873bcbf22841e27aa466cbf3e356bb389b862dcd55453097d79beadf8
d00b71ed37cd2c62f762b31b3f77a0f5791ea29931de317915682b1e967785d0
df299e3f32f08298c90f322491204079d888422fe0e73e87566e43583a3c534c
f411482e1e187d0b85c4be62459159ef83874b6bb19d88de38e70e530c6178b6
f6504c62569cd83f18f2cf50d7d7ae260ba0da38e86fa055d2892591f0544560
fa72c468e57411f896b71852621e5778a7dbaecc9f70119c0898dff8ba4247e8000eed382ebec21a1f27a860cc52613cdd98fc36dd12d37bad15caeb36846d7f
12c9cca4b13fb5fa772ef2991afe06c25a3f7dca89dc2faf15b0bf6a22c15c92
3e8435ac3726315d21afb12a8e47bdb347c2af362be4ccb1e05df5a33874c962
44623c837caf40341d187b5b5e1486eaec2528d0af715310ddf6c1c4b7b9ccee
6a201fc8696dc8ceff68c9829984b16e9994bc7c0a774bdd1859efec60f4d69b
8ca78f2eb59302102de3b8e471cd307513e655cfd0f872f27d2640eed0e3b4eb
9b60635bf858d1f432e726a029c7386ec6d17b2cc2e77845dc647200c7802312
c3141c72e98fd48da3546217ada5e31b6786041bd0b24373ae91c9e36ee7a67d
c78d8f99b69fc5c7ceb6d0d0755cb7b8aa818a77ec4ef574a25e8d79734aa0dd
d582c6bc50fa4f6c5a3f1e07ea33f61d4bd5276f76a66e65c68f5a57c3c1f511
e3a8ad4428b9aa93ab4c3bd83e5f7aebca9a70a1f7043b022411691a3aae3715
09959d473a1b842bb3d953a71ed0e7230ae32f16036805b09806dd626fbef580
0a54750e93f9e716b3ce206933b0c8d0d4b2771696ae0104478fe009879b0ea8
0cde3036878b3f0fc3dfe44a281769823948bc7bcff22f9c2fced9d5406ddf50
116d35b441fab38e6d72a58ec113535620a7c13e36f7e11d3f36cabeb71d3032
12507941a6f3742efa8fc866112524217ee7f906ac19f3e20a0bda5bc28397c1
1582a8f6c5bd486192de99a286566d09bf11a47cf3d3fd55fae0a3ee646b1f28
1e4856791ff06948959bce04f815ed6bb58a5e220e3abaee5b7d50d6b9a1d65c
20ec15898814ac2bb574b526a7070c7044e33b6f87575206677ba3ea5cf2a24c
28b6c2afff094e05a68c2ecd05b0507a4bd290a74410a89e0c35fa30f78c788c
28fd5a8e4d69285724858b8d8fdaef0f9af65deca01c6a0b335c544b7b51eb90
30fe2f72e06a5d1cb966e868196bde5547e586ba8f09bb8152fa8d2086372d0a
3391c12d268cc10419bf6a48bf235fab1006d2e61ac91cf039a30ccfac6649e2
33d6cbdcc208875a1e83b4fe215ca0d902ee3860165fb9b94b3d2a00025f925c
3636ab2e6bd670b933378e844159bf3600250f0441f14160cb83859c30c7c4ee
40802de4630cfb94f9a458ae678559680d6a459152bd96fb565e2a45a85531b3
4739dc5f11c309e520825b71054e83cbe0d5477fb69ded411162993da67b1211
481dfd997779ebadc3b9390c97a267db3d5b61cb8275c2ca1c55561efa49a220
4c682ee5f1646c4821e3ac88c570d3f65f1e34e13b139459bd8b165dca36c49b
4cce2b038ddd73ea8d6ee059bd8bc2a814829823f69647d7f87c9f5af75ea1b4
5180c17fd25d52422d1246ccff4961e44d7932fadf8633b03668953fa3f3a664
5d16e3b5930da291790c6ba70caf4a88067b1e11aecfd1f7ea3a88eb9e06dfb7
667e4d67acff2b8e60e3ca14075d33e51cb5269512b9208241d9381b25192f17
679cc9ff7ed27407e37a028d945ab0895becccea18f7ca70ea8bfbb79e2d82de
683453d1b92f8b3db65ec7de31036b248ea04fe8f250a4c0e3a8596f1236d1a0
68dd4aa92850fab76a6a23df41166f0f706da811aeb340710459c21b357794ea
6de6fd9270dfd007f375782b76854b7cdd21b48994def97457265d3c047fb092
6ebc9ae70ca7c605acf342c7bccad069fe4dac95b850812c7585ccf2bc28e24c
7a594591ece534e74299e4660ac0e2c458fca1136920f68904b6408c7e7e1071
82906c572d6bb9f511183a4c18fdff6d399bbad646c0d47394c8329f0d9dd47a
84a01c5607791856c849e0db4b15e29dc21f7a04fc8540c085b86a820d687a15
85f8ccf69bed672d92b40c45f9571378a7d00c80b86004a76018d9e120eeaa01
8afaad8f3657e978790860174412ff82a7673543fc23228012fa13a894ea1e72
8d47a214344c1af6da38772556c3b9e1dec27c53ea23360e3219845c67cda5b2
98b4c878d93fbed658aa05f518e610506cd78f3e0d871c92eeb84ee781dcbf24
9d524c8444ee8d6d66976c22456e7ebf54395e53be35c5aa69e180f6f5dce74c
a5fbdc052a07a2ea2f13891596001e9ec1d8fac940ea0a3599597a7c48d67a77
a6287162def3932558debccc288f2a2a1f04eba7dca9e2a2d64de8146808466b
ac5a5a5f76815b9d61f7ce83d555b237b3ffe5dc92ec3719e0990ce4ed85fe3b
b44f58b17096abf899f48a1703ca0564950634d90acb7ceded6d372642dec346
b536d4655560395df4eb3d8f9b46590f31023a1b96a75e32cd8d20192435a1e2
b71a133ae09604f17fbebaea4512e251e9404c865b619d18f07ec3008d1f2f6d
b8a13d7758cdf9d8b80fc2504866e9a26ca348f4a940ca6a451754fa61564f73
b8b4021fb3083a2feadcf5cb755f2e66561a1f20949cefcf83c21b508ff8dbec
bc800e5252da33803ce2cf6ffc06c899703735ad72240b54f34b0ea7389cfd47
ced35c008c4d1d774d2fdc493f66ac4bcc623ada7f7008ff5b12f895848f7e31
e18519525f442b8e6e97b5b503c041c0f548d4bc9b1538881f31dc5bb72d6f18
e4eb15c56cb3711b83a6dabc7cb9489e209205aeea7b4a92b1039ddc069f6e69
e545da3a7624d5c8c7fef362194619e39d215385991a79978a518d5be4212691
e6353eb093a2ca1dd4bf336a5ea80bef7306be0c1d2848e59ed8f87e5df825bc
e6689e14ec941295ff2b33ac484999239504ebcb6e9daf803b11d2652eaecdda
e6fa6f2b014ea80b19fe14ed20aaadc8ff7b7505efa326833c96fe3ff37b9261
e89a30a0a7c387d74b274566557a1b45a62dd8dd9842181a0dc082d626657c69
e8ec993c0ab37471ddd3a6a7e117147dc2d404817cab5845a6eb5def60c5d0c4
ecac78dc376b08a004d056ad29d57ddd96905b94675695e4d5fa78d81c02dbc4
edb9be32ce811b0d51bc871b5ad75036f7750f5d46587855e01d167532486b6a
f98916ba5138dd6f233023a3b9fe5e969a50bee3d7cfffb69900f4d1d39e02b6
fc213a5f50b671e5b0914b2cea4354a3394aaafbf7a4a99ecccb2db31b78c76a
def decode_rot23(input_string: str) -> str:
"""
Applies a Caesar cipher rotation of 23 to all alphabetic characters in the input string.
Non-alphabetic characters are left unchanged.
The transformation preserves the case of each letter.
Parameters:
input_string (str): The input string to transform.
Returns:
str: The transformed string after applying ROT-23 to alphabetic characters.
"""
result = list()
for char in input_string:
if char.isalpha():
base = ord('A') if char.isupper() else ord('a')
rotated = chr((ord(char) - base + 23) % 26 + base)
result.append(rotated)
else:
result.append(char)
plaintext = ''.join(result)
return plaintext
rule STDGroup_Crypter_1
{
meta:
author = "Malware Utkonos"
date = "2025-10-06"
description = "Detects Proplock or STD Group Crypter packed samples"
strings:
$check1 = { 50450000 ( 7? | 664139 | 6639 ) }
$check2 = { ( 64860000 | 6486 ) ( 7? | 664139 | 6639 ) }
$check3 = { 4d5a0000 ( 7? | 664139 | 6639 ) }
$virtualalloc1 = { 40000000 [1-12] 00300000 }
$virtualalloc2 = { 00300000 [1-12] 40000000 }
$virtualfree1 = { 41b800800000 3?d2 }
$virtualfree2 = { 3?d2 41b800800000 }
$init1 = { 41b90000cf00 [0-20] b980000000 }
$init2 = { b980000000 [0-20] 41b90000cf00 }
$res1 = { c74424??2c010000 [0-10] c74424??90010000 }
$res2 = { c74424??90010000 [0-10] c74424??2c010000 }
$compress = { fd377a585a }
condition:
uint16(0) == 0x5a4d and uint32(uint32(0x3c)) == 0x00004550 and
all of ($check*) and
1 of ($virtualalloc*) and
1 of ($virtualfree*) and
1 of ($init*) and
1 of ($res*) and
$compress
}
rule STDGroup_Payload_1
{
meta:
author = "Malware Utkonos"
date = "2025-10-16"
description = "Detects Propionanilide RAT payload samples"
strings:
$alert = "@everyone A new computer"
$discord = "discord"
$dormant = "Going dormant..."
$ip = "Computer responds with the IP:"
$op1 = { 05000000 488d15 }
// 140166a54 48c744242005000000 mov qword [rsp+0x20], 0x5
// 140166a5d 488d151c1cffff lea rdx, [rel sub_140158680]
$op2 = { c745??05000000 488d4d?? 48894d?? 488d55?? e8 }
// 1400a5dfd c745d405000000 mov dword [rbp-0x2c], 0x5
// 1400a5e04 488d4dd8 lea rcx, [rbp-0x28]
// 1400a5e08 48894dc0 mov qword [rbp-0x40], rcx
// 1400a5e0c 488d55d4 lea rdx, [rbp-0x2c]
// 1400a5e10 e87b54fdff call sub_14007b290
$heartbeat = "heartbeat_interval"
$hb1 = { 488b8d[4] 488d15[4] e8 }
// 14007a1ad 488b8d88000000 mov rcx, qword [rbp+0x88]
// 14007a1b4 488d1571a74c00 lea rdx, [rel data_14054492c] {"heartbeat_interval"}
// 14007a1bb e8f09ef8ff call sub_1400040b0
$hb2 = { 488d15[4] 488d8c24[4] e8 }
// 14015737e 488d156bfd5800 lea rdx, [rel data_1406e70f0] {"heartbeat_interval"}
// 140157385 488d8c2400010000 lea rcx, [rsp+0x100]
// 14015738d e86209fbff call sub_140107cf4
condition:
uint16(0) == 0x5a4d and uint32(uint32(0x3c)) == 0x00004550 and
3 of ($alert,$discord,$dormant,$ip) and
1 of ($op*) and
$heartbeat and
1 of ($hb*)
}Learn more about Spectra Core. And find out more about RL's YARA rules.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial