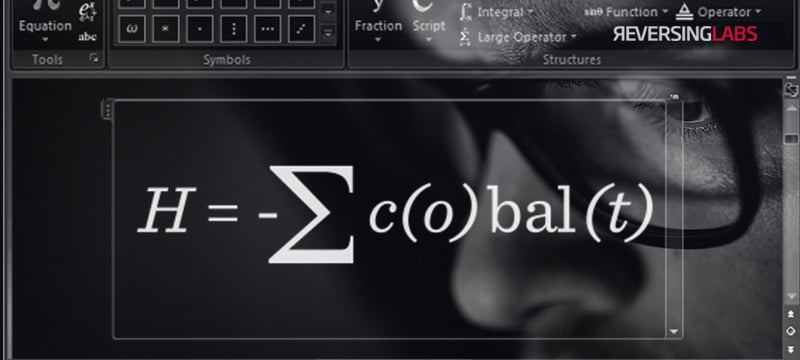
Seeing that Microsoft Office is the world's most widely used office suite, vulnerabilities found in its components present a major security issue. The risk is even greater with remote code execution vulnerabilities, as the attacker does not need physical access to take control of the affected system.
One such vulnerability is CVE-2017-11882, discovered in Microsoft Office Equation Editor, the application for creating math and science equations within Office documents. The memory-corruption issue has been present in the Microsoft Office code for 17 years - not even the latest Windows 10 Creators Update was spared.
Exploits that take advantage of this vulnerability have already been detected and analyzed. Sample analysis performed by ReversingLabs supports the conclusion that the infamous Cobalt relies on this particular vulnerability for their attacks. Read on for more details from our findings.
The starting point of our analysis was an RTF seen in the wild:
bc4d2d914f7f0044f085b086ffda0cf2eb01287d0c0653665ceb1ddbc2fd3326
Using MS Equation CVE-2017-11882, it contacted
hxxp://104.254.99[.]77/x.txt
for first-stage payload, executed through MSHTA:
5f434901d4f186bdc92ee679783bdfad80281423848462e445704d5a10b0dc20
When run, it downloads the next stage payload from
hxxp://104.254.99[.]77/out.ps1
677426cdd9c6945de3a3858f12fae62914e4d914a24f51475b859f2bcb545095
The script drops the embedded final second-stage payload - Cobalt, one 32-bit or second 64-bit DLL, depending on the system architecture:
d8e1403446ac131ac3b62ce10a3ee93e385481968f21658779e084545042840f (32-bit)
fb97a028760cf5cee976f9ba516891cbe784d89c07a6f110a4552fc7dbfce5f4 (64-bit)
The MS Office dropper can be detected using the YARA rule “potential_CVE_2017_11882_v2.yara”. Download the YARA rule here.
Additional IOCs:
MS Office documents exploiting CVE 2017-11882 seen in the wild, leading to malware payload:
e14d0f34b2eafd600234d4d6c1e3e9970eaabec497cdc8b8cd62681e43760a39
a6d6a9107d992048739cb04bd4fb89647b28877d7d4d86b747d7920de04bb116
5734f4a975d39ca6d6d3ff7c2e4d5133501fa39489c1c6ade7c7c1c261d4656c
0a596c67b3733fbc6b7dffbce69d65dc649162c2ac7a25c54c0e4679b5baf5c9
94b9dd0eecc2ee5411c91bb6bef4edcf0db00d4360937a0fc31fdb9aae811844
b6bafc9586de3b5d351ffabaee47157a1eb9ddf93bd2c04c28d68df8e374824f
17f9db18327a29777b01d741f7631d9eb9c7e4cb33aa0905670154a5c191195c
3312ffa9941e1eb2ba2d64a4c6dcdb7a39fef86babd086efeeb1d6efc970bce8
c5f5f136bcdc259671d47ea30dd459b67dc1478a99f25a45c30950533ff150cf
43b58a960f6a29da9a755dd3c44c490124a70b52e6e2fcc4ec620be4367f09ca
c46af34a952e65cd964ff382e142e78176e660801f4f876095926656950ff5f5
ffc8be3a00cf241cacec8f919535ede12c7afd0202769653d4deebebec99dd8b
2b6004fe60b1896ca50ef9eef59d869df068c821e09a6050211ac4781538a262
5c68c0a32a8c59271afe3456430125f77b02b240fe578da6b7f398656f6cf972
172151f122193b2229ec6a6a63c259198e1d4ace06381ff20f74a9369612dd57
6ccdae80c4ae74c3c5ce47341fabfab53a09ac726c6ed8eec02ca549db532a77
1f689e3cb16533604fccfbe9b36ea913d4c354d2730e0ceac41a0ef711a0c5df
2b5b13215944f124cbff1e0029073e2e432c9788ec1a8c8d31a303ac827ac3d3
2e9ed723ed8f3f97ed205c534881f997a25546b3d2d8ef5719636a034dc90458
94b6f39f0203c9d82ed69a99a0443e4f9814394bb181359ffd906840696ff88a
1157602a1cfd3de2d448f0a18d4a3e6b7ddac9e9902bbabd46347a3295a1aa4e
c02b94af36f84f3c9a958f2b75eecde382c7438b837c2160ebe65b40e64058e0
0f282bb3a1913c8d4e807ece231c891d1faac8b16d02f6d7a965f7ca9d2fe541
5f27a664f38890e5dadac69a3c8e33679d4511cdbf65a4423a1fbb16ddf5edf0
6f2dbb3eb9f40fe5326f60bceff5fe58e7458ba2991dbe6e1aa500f4b44130e8
0fd8e3a2e55b4306b817396ea469aa4ef78612686934c1ec1bc8eabb337ed133
1bcc44b25363a6e9a2303eb8f1d00815d65c3f1d3ac870b6aafbba3b9c72f0fd
de45a12f21654bae67d0531b02603cef5ef2849609bfda7f96ae6ab10d53d769
e5217688074d10fd3a94761de1f8fbffd09caa7d7a89c567d551d2b5916c0fc2
f8274bbffb680bae6c6e8a7665149d83e06c6e5bfc4d056548bc8b44a030dc45
1b1bbe51dd75e00126b704ac80fce72178b05d96c145e28fb353ab55999a419e
1fefd2fc644d38d1c6e180e5edb65acacf90291f757c93a2c7af64aa3b243557
02a69029bf2b0c97bfb9ddbbe6e89409f1b11007a92d8ca4a6df6597b72eb453
18eed3b1f1fec188d0479b3247c6d857a946aaaf6e611f9ea739e511a622851f
34d791f76ca94cc971db533c99ce1ddf1f7dd2089f02bcda3e123dbab483c270
a85edbbc88bb10f663eeb1a9d9821f7c17d6316a7cab8216146337dc89ea70c0
aadfd6f891c0d3247e7ae010632d04c3b00d705924f0c024e2e8c2ea58cf3b7a
bc4d2d914f7f0044f085b086ffda0cf2eb01287d0c0653665ceb1ddbc2fd3326
2a4ae284c76f868fc51d3bb65da8caa6efacb707f265b25c30f34250b76b7507
4508e2452cc5836603326c4bd7cfffb6c56d3181d4399d0df245d7f0a11fd947
3f6539ade41798c93e754e2bb63c0cebd7722538c871e097f125116f939d56b2
8384f8c9c8dff0a842cc8d2654bd887dbac85973e0de8e2fa0a28208457ac0b8
153338d99d658853f44e4529a21c36c4dffd340ad20971b84b86648b729ca5cf
8eb4260e9edb33de8bb6c7bd191e456d53ad2183b8600d54e1b75a17090f5596
List of related second-stage Cobalt payloads:
df3a183cd356d14ca1dee36a0376de8ed7d8be2451e3e191caca004cbdba568d
0dedb345d90dbba7e83b2d618c93d701ed9e9037aa3b7c7c58b62e53dab7d2ce
1ed35c70a6379c59e7bbe5ee2d718913a7e0482b8a11500c938c5467b4430177
4e769cd80af0f82c84a3e00567d685a8098bdc24c104594b9a77ba5f2a0ae408
5f777cbad221cb2d89c59ff84ced2fd278d6d220c3cfc13e3fb8e2ca38698e0f
7e4767bb3997c942f138355a1e5ddf93d5c5b52a309e7c0bdd3fea75bddc0ca0
8aaee0a50686c45a7d564f0ab533a13183456f11fc983240baab940084763187
9c820c52697f0be2d457da1410c86659fbe47f93353dbfe87c4f3a9afd50472e
9d9d1c246ba83a646dd9537d665344d6a611e7a279dcfe288a377840c31fe89c
15ebcf18d77160bcb5c3bd5ce85475a4631036a67974d71a4540e185ad305017
55c46fb55ba8573fb8c0f012cc0943c9d44dc121bdd2b25e9134b2c3e617c816
070a2d3701c7c86530d0a6a9293319fbc899e6c9dd3ffff3bd85030efc602f24
619be697adf228db96272c81797b282fdab9236c2e042494b4132816b0419f7a
681a3d4d45b66d3268418a964e772f4cb5cb829b3fa1f5c7e229a6063f7d8f8d
1837db25557194057a0ec37048e67b3b21c0d45d8565fb8bbedeeea9205e7587
00015947e2b5eae9ebb41362e33c8ef52d1e6248018f14985b03c046d5ec23b8
414975d25881fe8b440dfd01615203501d511d0e87394add8e88c6496bdd45ff
a1e1dc07bc737f41a59e04eb22cd1fe03bb108b95f56b220489d87c76d63e6b5
c2a4b00b8ac3394764c4b604a3d439795556291233b2f6ae5145994e33a40814
c15c29771e3bd490d8afce6b36ee06f9f7a0fc7c173510941be95acedb270e26
d0dd18fe48a4348c8ac59215f46923e9ebfc1373400c5ff881b3e2516f602216
d8e1403446ac131ac3b62ce10a3ee93e385481968f21658779e084545042840f
dc9dbd7644f060d0aa2fe469a6bcafff7dbd5d696d782d153dcdd996f2999f50







