Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
Businesses are vulnerable to software supply chain breaches when software releases leak secrets such as authentication credentials, hardcoded passwords, API tokens, and encryption keys. Look no further than the CircleCI, Toyota and CodeCov incidents.
Behind the scenes, attackers are automating secrets detection to find credentials and attack software development tech stacks and delivery pipelines. Once compromised, software supply chains leave software providers and their customers exposed to further attacks including the placement of malware, the theft of sensitive data, and the loss of intellectual property. Development secrets - critical for today’s complex software to function - are challenging to manage across every software component and within every stage of software development.
That's why we are unveiling first-in-kind features within the ReversingLabs Software Supply Chain Security (SSCS) platform to improve:
With our new capabilities, ReversingLabs is giving developers and application security teams something that other offerings don’t: broader visibility into software supply chain risks and data-driven prioritization to automatically suppress third party secrets and other false positive results that are not actionable by developers.
See Deminar: How to keep your secrets SECRETSpecial Report: Secrets ExposedExplore ReversingLabs' secrets capabilities
Our binary analysis and enhanced support of 250+ types of credentials extends visibility beyond code analysis, into entire software packages and containers before release or deployment. This delivers a comprehensive view of whether secrets will be exposed because of:
This broader secrets detection scope is important as breach research from Verizon and IBM show the increasing use of compromised credentials during multiple phases of an attack. However, the bulk of our new capabilities are focused on solving the reason why detection alone hasn’t prevented leakage or use of exposed secrets in software supply chain attacks: noisy results.
Secrets scanning solutions will always detect a lot of secrets. As software has become larger (ReversingLabs has scanned 10GB software containers) and more complex -- with open source, third party and commercial components -- the number of detected secrets will only increase.
The problem is many detected secrets are not actionable by developers, for example:
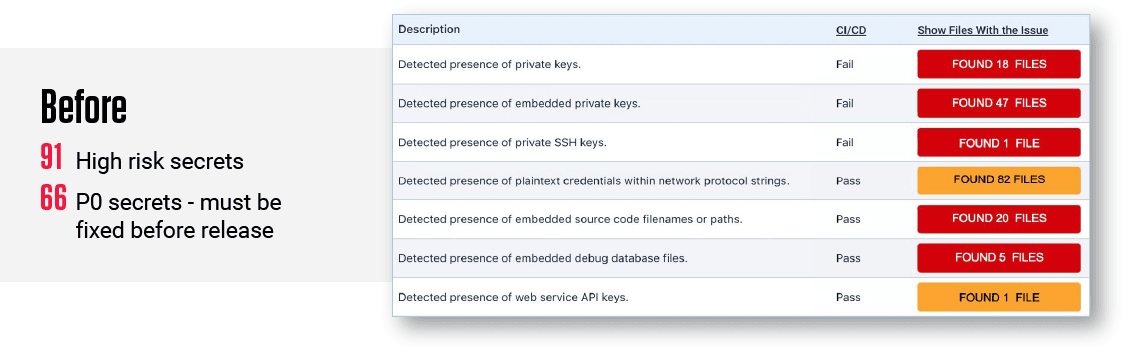
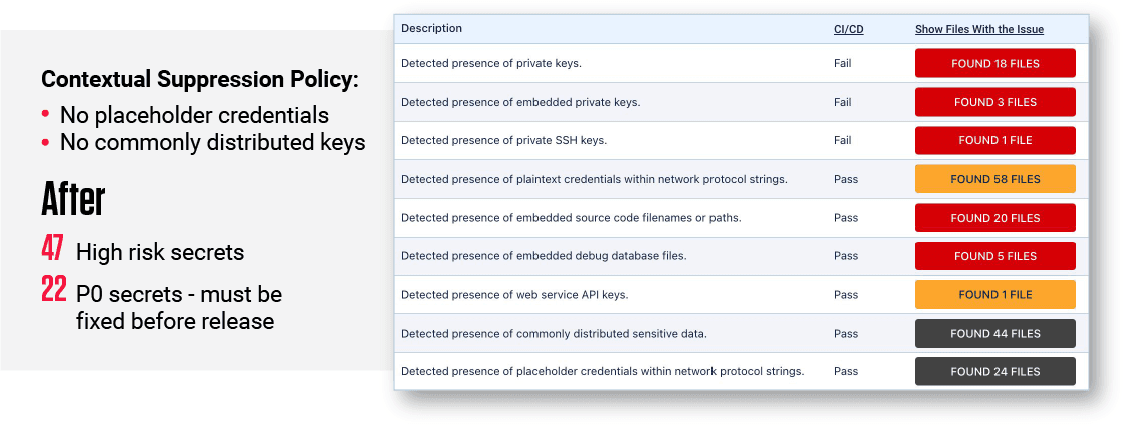
Figure 1: Detection + Contextual Prioritization = More Effective Secrets Management
To support this contextual prioritization, we need to know what- and when exposed secrets entered into the public domain. We have this visibility because of ReversingLabs huge repository of threat intelligence from scans of billions of files. This repository, the largest known private commercial storehouse of malware and goodware, has been gathered continuously for over 10 years and curated by our threat research experts to ensure it's kept up-to-date with the latest information.
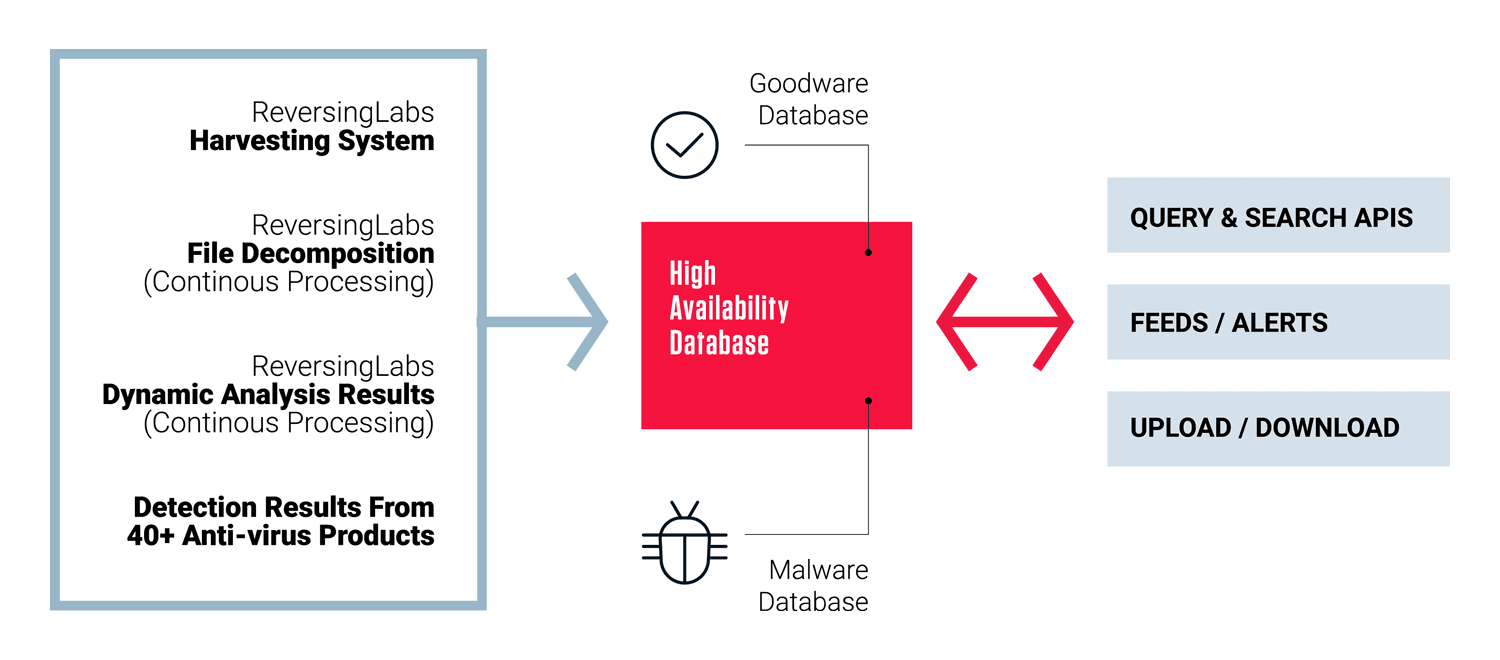
Figure 2: How ReversingLabs Threat Intelligence Repository Is Curated
A quick lookup in our proprietary repository can tell us if and when leaky secrets discovered while analyzing software are a match to secrets already publicly available in:
This is exactly the context needed to save countless hours of triage and/or unnecessary remediation with accurate, automated suppression of commonly shared secrets used for testing open source components that have been public for years.
Our data can also indicate when the level of risk has increased, for example, discovering that proprietary credentials rotated a month ago entered our repository a few days ago. In other words, secrets you’re working hard to protect have been found “in the wild”, where any malicious actor can find and use them. Leveraging that data you can take action to minimize risk of a software supply chain breach with “just-in-time” secrets management, i.e. by immediately rotating that secret with your secrets management solution.
Maintaining the status quo isn't likely to get you different results. That's why innovation is so valuable. Expecting software supply chain breaches to stop happening without innovating tools and process that streamline how secrets in software are found, prioritized and managed is not realistic.
With ReversingLabs, development and application security teams can take the toil out of identifying, prioritizing and remediating secrets in software that create software supply chain risks for their organizations.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial