Spectra Assure Free Trial
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial
As a cybersecurity leader or application security professional, you are responsible for ensuring that vendor software deployed to your organization’s environment is safe. It needs to be free of malware, critical vulnerabilities, and other unacceptable risks. Likewise, it must not jeopardize the company’s regulatory compliance status.
ReversingLabs Spectra Assure allows organizations to scan third-party software to identify a wide variety of risks. No source code is required for the analysis, so this approach offers security teams a compelling way to evaluate risks that third-party software could introduce if deployed.
If unacceptable risks are found, the Spectra Assure platform’s Share Report feature makes the scan results available to the software vendor. Vendors often respond by addressing the issue and providing a patched release of their software. That’s ideal.
But what if the vendor declines to make changes? They may dispute the findings or argue that the risk is insignificant. In some cases, particularly with large vendors, requests may be disregarded or brushed aside entirely.
One option is to reject the software due to unacceptable risk. However, the business may try to override that choice if they view the software as mission critical. Another option is to accept the risks and deploy the software anyway. That’s not ideal.
There is another option: Developing a compensating control using an EDR solution that mitigates specific risks identified by Spectra Assure if the software were to be deployed.
Pairing Spectra Assure with an EDR offers benefits such as securely enabling the business with their preferred tools, and having proof of due diligence when it comes to deploying third-party software.
In one scenario, suppose your company's development team adopts Postman for API testing and development, and as a result, they request that the Postman desktop application be installed on all developer workstations.
Security teams aim to support the business— not slow it down. But they still need to thoroughly assess the risks of introducing new software and deploying it to employee workstations. That’s exactly where Spectra Assure comes in.
The process begins by scanning the Postman software package with Spectra Assure to detect possible risks. By using the URL Import feature and entering the download URL for the Windows Postman installer, Spectra Assure retrieves the file directly and initiates the scan. This streamlines the workflow and avoids downloading potentially risky files into the internal network.
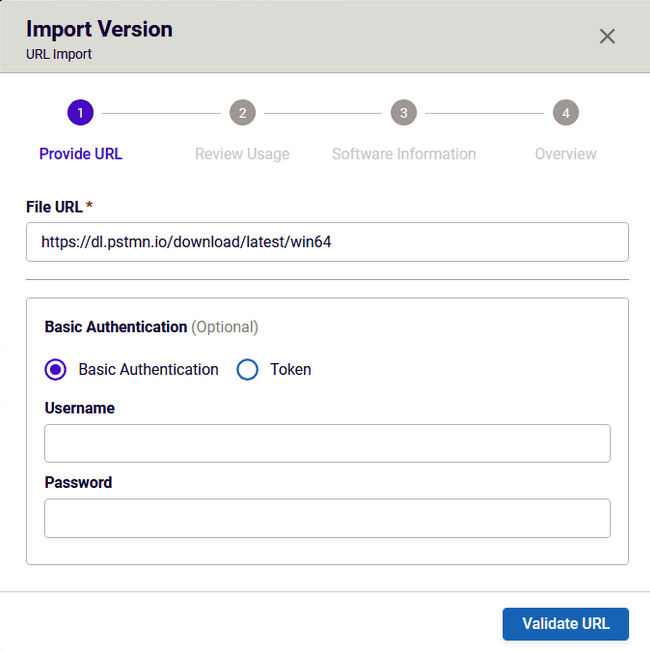
In addition to providing a full software bill of materials (SBOM), Spectra Assure outputs a SaaSBOM that delivers insights into cloud-native services and APIs. Beyond that, it also highlights potential network-related threats that warrant closer attention.
Looking at analysis of Postman, see how that policy violation TH17127 — related to URLs of raw files on GitHub — was triggered:

Although the finding may at first seem benign, it’s important to note that threat actors are known to abuse raw GitHub file references to deliver malicious content.
This threat hunting policy was triggered due to the presence of the following URL string, which appears in more than one file in the scanned package.

Policy violation TH18102 was also triggered because the package contains references to top-level domains of countries that have EU export restrictions.
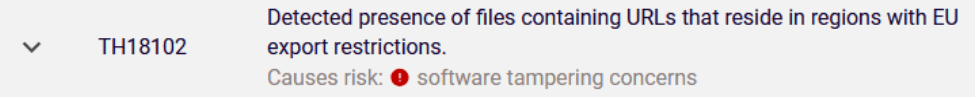
This threat hunting policy was triggered due to the presence of multiple URLs ending in “.by”. This is the top-level domain for the country of Belarus, which is sanctioned by the European Union (EU). Some EU organizations may have policies which restrict software running in their environment from connecting to servers in Belarus to reduce risk.
Other than those two issues, the Postman software looks safe to deploy — no malware, tampering, or critical-rated vulnerabilities were identified.
How can the two identified risks be addressed? One approach is to contact the vendor and request that they remove references to these locations from their software. However, this may not be successful and even if Postman agrees to the change, the process could take months.
Instead, you can leverage Spectra Assure and existing EDR solutions to implement a compensating control immediately to mitigate both risks.
In this example, Crowdstrike Falcon is being used to implement the compensating controls. However, any modern EDR platform should be capable of supporting the same approach. We begin by creating two firewall rules within Crowdstrike under Endpoint Security → Firewall.
For the raw GitHub files risk, it was decided that developers should be permitted to access raw.githubusercontent.com (since it does have legitimate uses), but each occurrence should trigger an alert to inform the Security Operations Center (SOC). The firewall rule below reflects this configuration. Connections are allowed, but watch mode is enabled to ensure visibility.
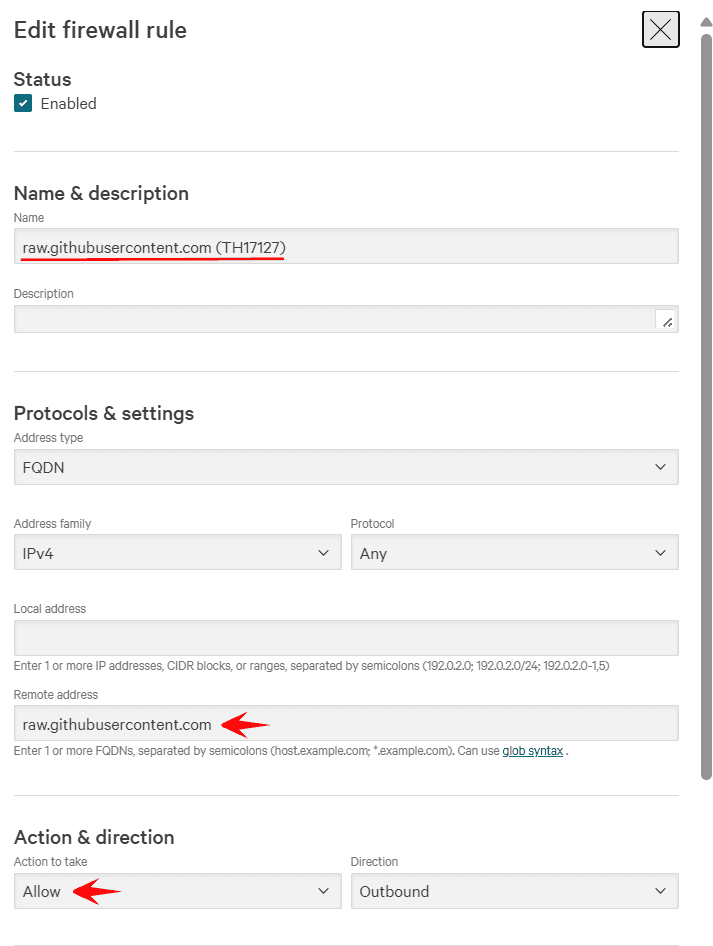

For the Belarus risk, it was decided that the control should block all connection attempts to “.by” URLs. Watch mode is also enabled for monitoring. The firewall rule below reflects this configuration.

Next, a firewall rule group called Postman Compensating Controls is created and the two new rules are added to the rule group.
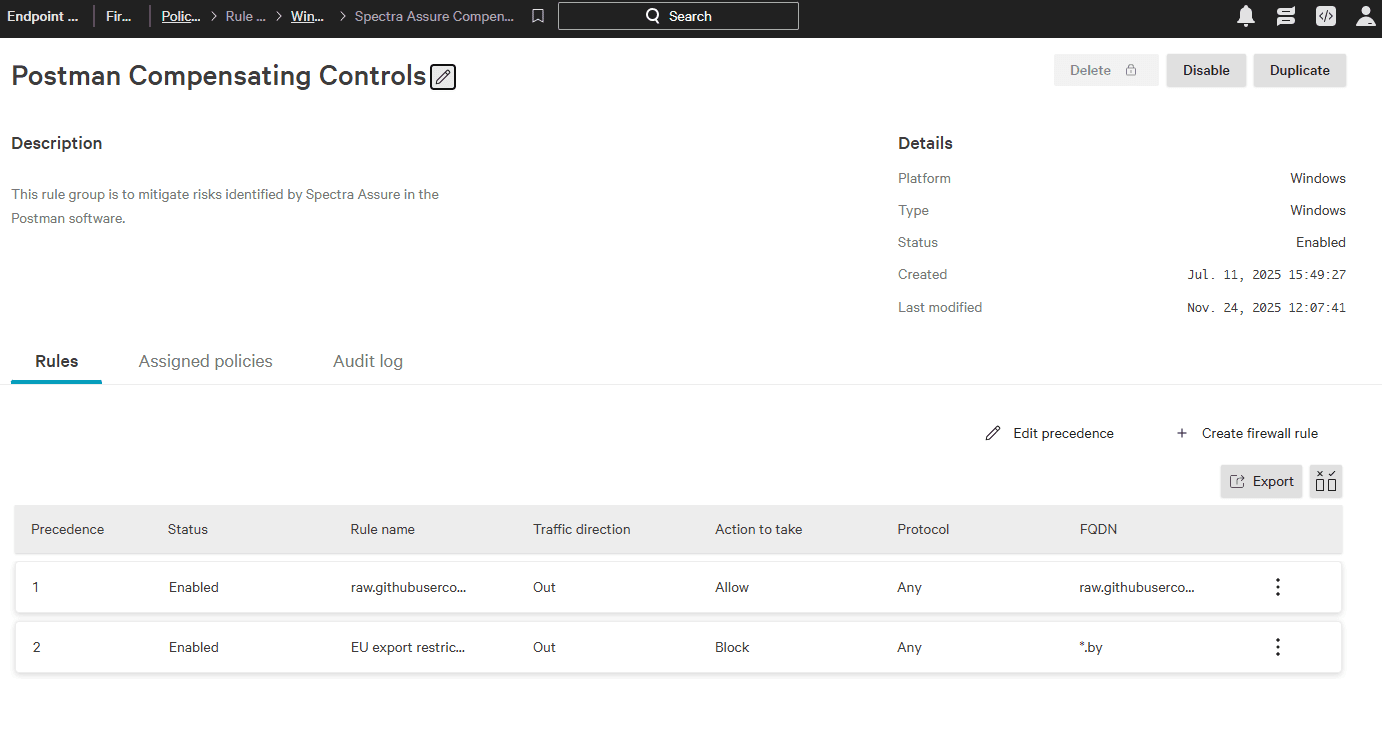
Next, a new firewall policy called Windows–Postman Risks is created and the rule group is assigned to it.

The final step is to assign the host group Developer Workstations to the new policy.
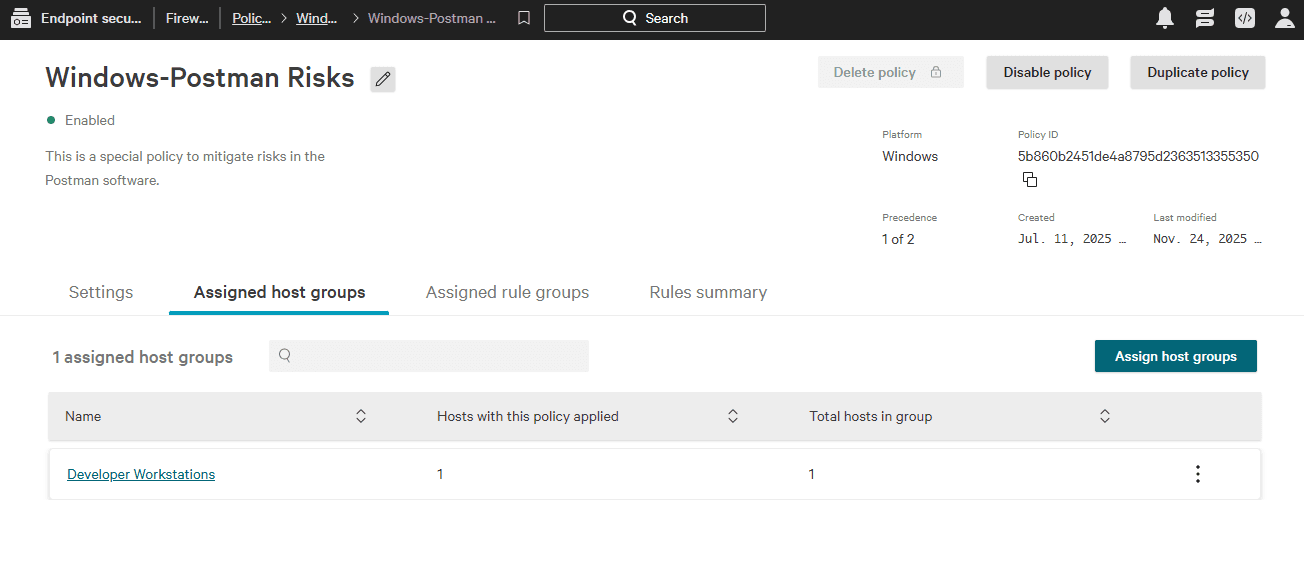
The EDR agent/sensor on each endpoint automatically checks in and retrieves the updated configuration. Once applied, the EDR-based compensating controls can be tested to confirm their effectiveness.
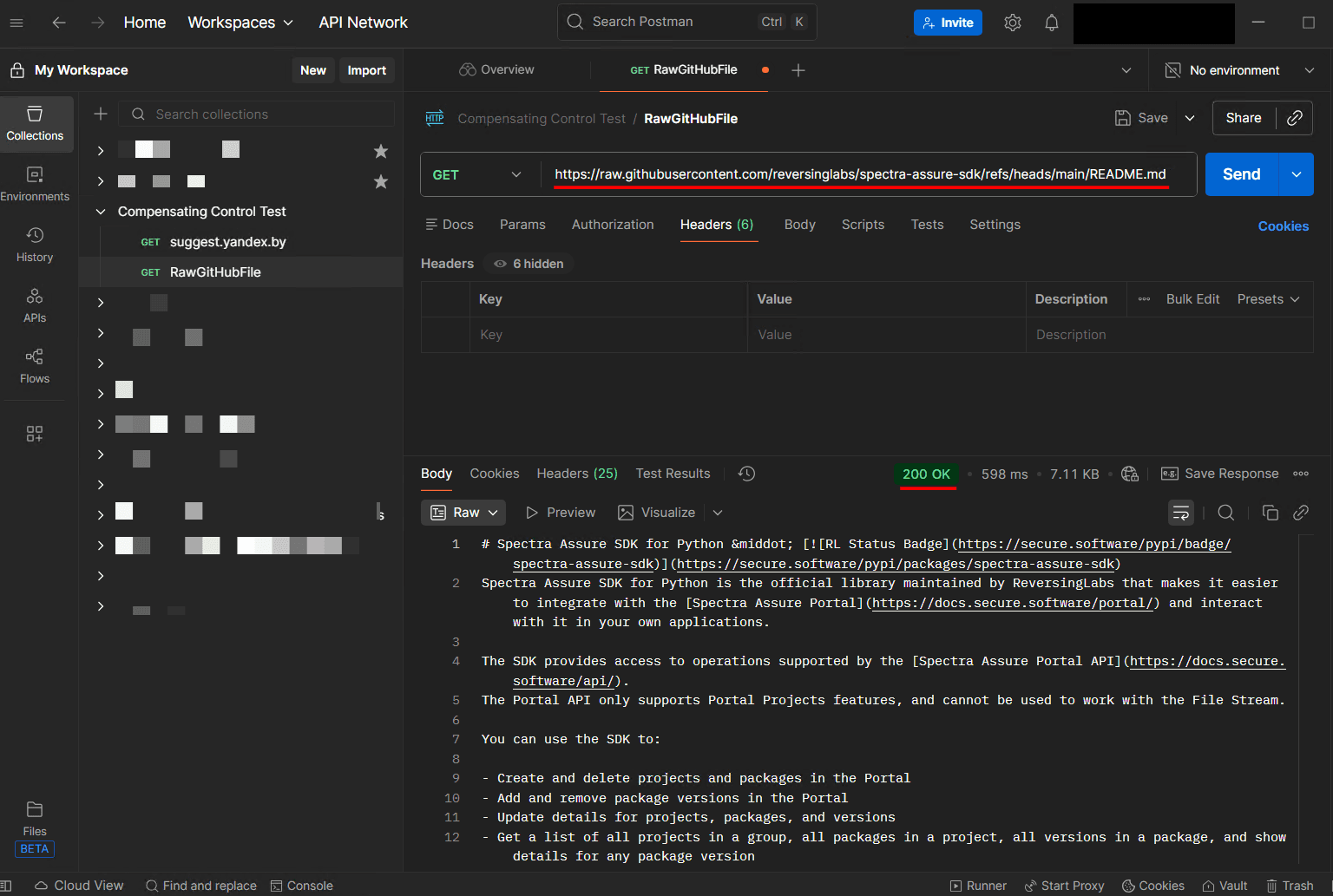
First, Postman is installed on a Windows machine being managed by Crowdstrike. While it’s not known exactly what functionality in the Postman application would cause a connection to raw.githubusercontent.com or a “.by” URL, it is not necessary for testing because of the nature of the software. Postman allows invoking API requests to specific URLs of our choosing, enabling us to run the tests.
The screenshot below shows Postman sending a file download request to raw.githubusercontent.com. The Crowdstrike agent allows the connection, and a 200 response confirms success. This behavior is expected since the rule for raw GitHub files permits such connections.
As shown below, the Crowdstrike console shows the connection under firewall activity.
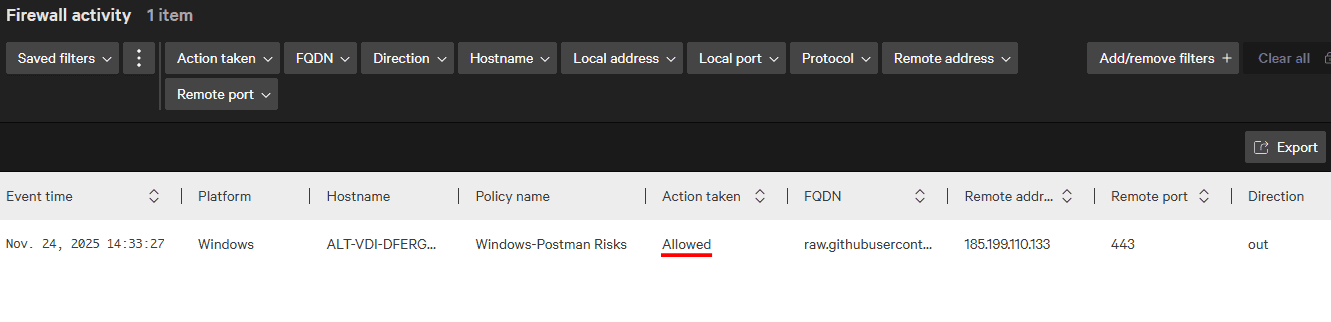
Below, Postman tries to make a request to suggest.yandex.by. As expected, the Crowdstrike agent blocks the request and Postman returns an error.
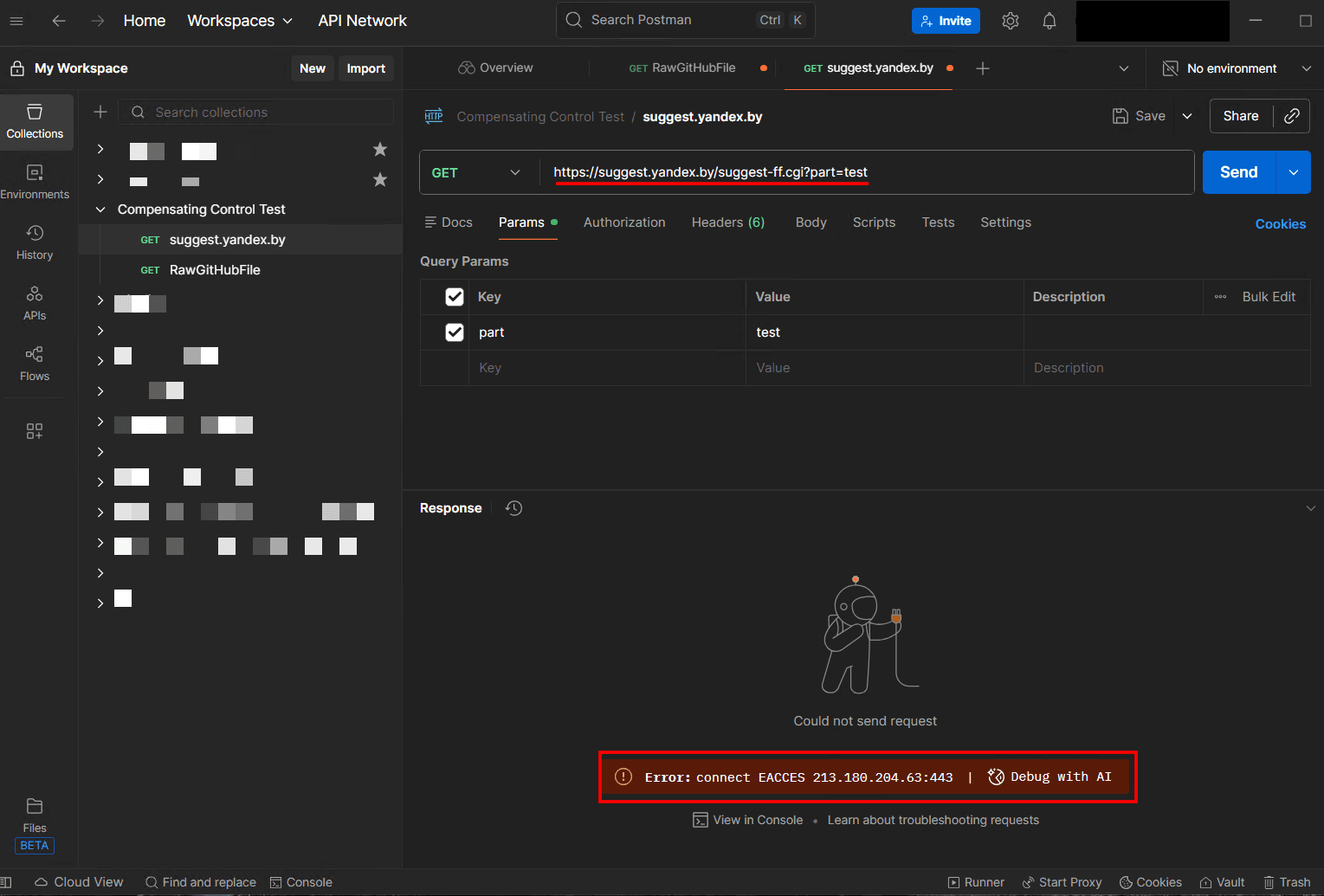
The Crowdstrike console shows the connection attempt and in this case reports that the connection was blocked.
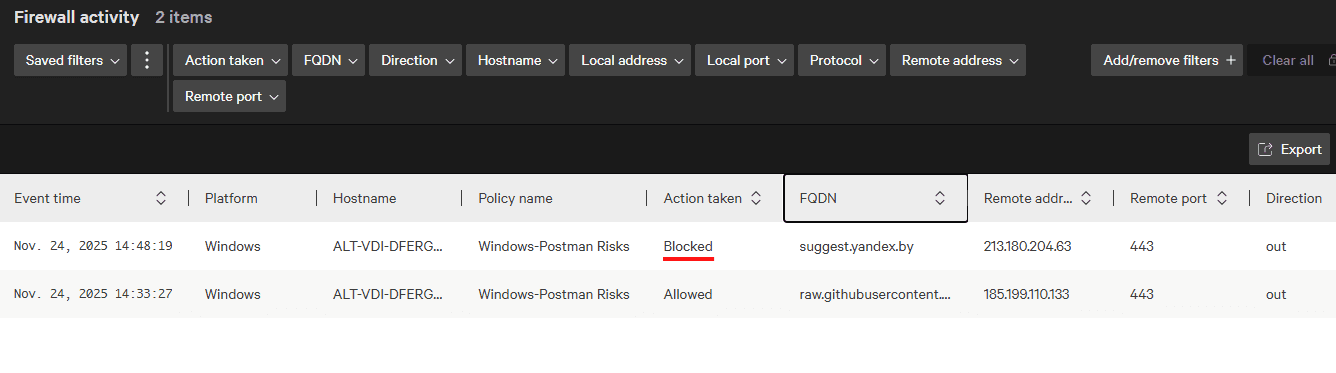
Both tests were successful demonstrating that mitigation of the risks is effective.
Win-Win Outcome
Following a risk analysis with Spectra Assure and the deployment of compensating controls through the EDR tool, security teams can be comfortable in approving the installation of Postman on developer workstations. Spectra Assure made this possible because the breadth of its policies enabled the organization to identify issues based on its risk tolerance, and the detailed results from the solution allowed for creating surgical compensating controls.
Furthermore, the enterprise security team has documented evidence of due diligence: Third-party software was thoroughly assessed, and mitigation was put into place to address issues outside of the company’s risk tolerance.
This outcome is a win-win, because the developers are happy to use their preferred tool (resulting in improved efficiency for the business), while the CISO is satisfied knowing the software underwent a rigorous security assessment and the associated risks were effectively mitigated.
Overall this approach delivers greater value in less time compared with traditional assessment methods such as trusting vendor questionnaire responses or investing in lengthy and costly penetration tests.
Explore RL's Spectra suite: Spectra Assure for software supply chain security, Spectra Detect for scalable file analysis, Spectra Analyze for malware analysis and threat hunting, and Spectra Intelligence for reputation data and intelligence.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial