
If you don't love me now: JsonWebToken could break the software supply chain (again)
The JsonWebToken library has a flaw that could have lead to remote code execution (RCE).

The JsonWebToken library has a flaw that could have lead to remote code execution (RCE).

Researchers compromised source code and development infrastructure for Mercedes-Benz and SiriusXM Connected Vehicle Services, raising security concerns.

In this latest attack on software development environments, the CircleCI platform may have exposed secrets used by millions of software developers.

The collaboration between SOCs and software development teams is essential to taking on the challenge of software supply chain attacks. Here's why.
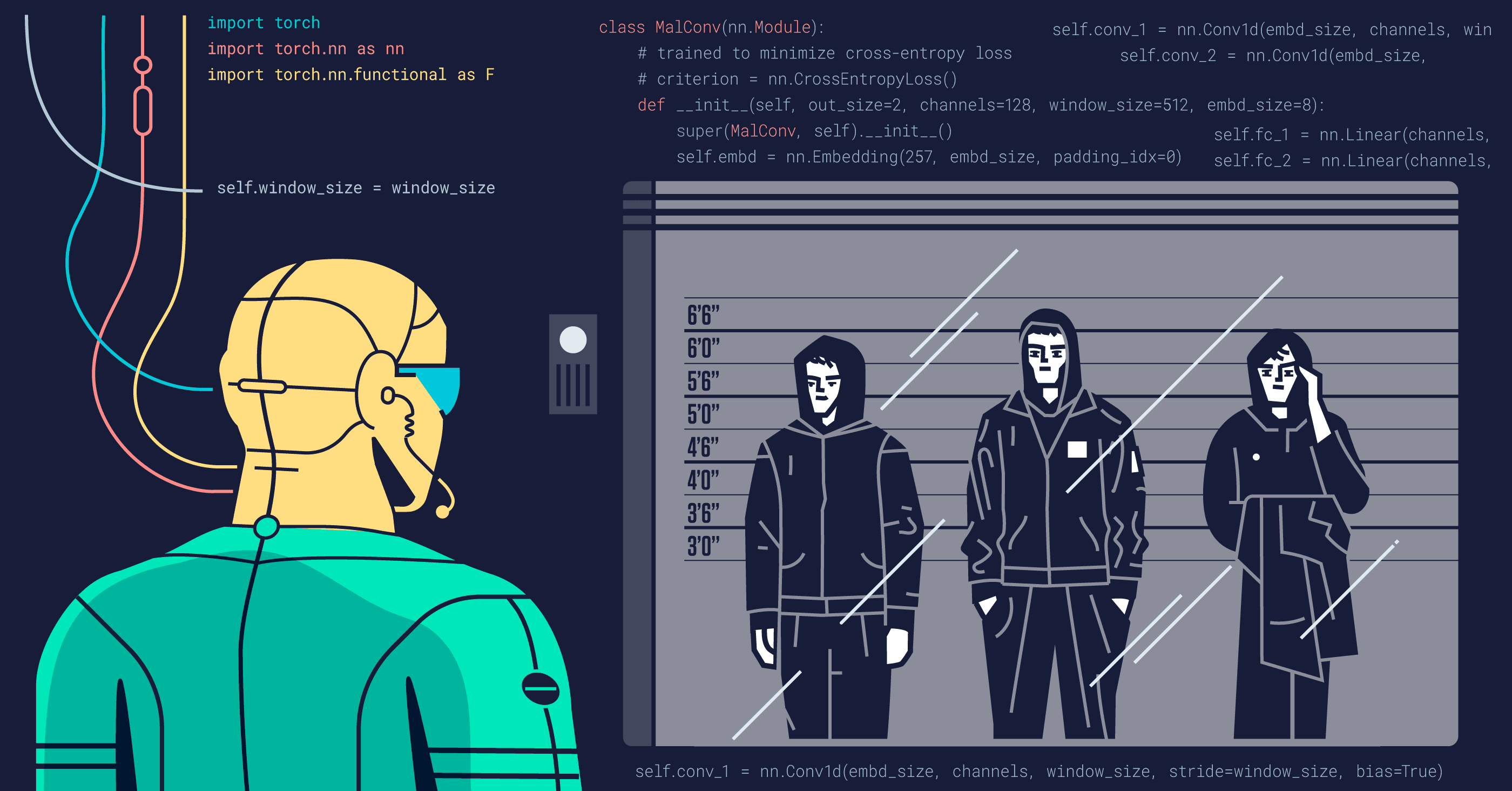
As attacks become more sophisticated, it is imperative to harden machine learning (ML) models and reduce the adversary’s ability to evade detection.

Welcome to 2023’s first edition of The Week in Security, which brings you the newest headlines from both the world and our team across the full stack of security: application security, cybersecurity, and beyond.
.webp&w=3840&q=75)
A classic dependency confusion attack revealed itself last week.

Supply chain attacks are surging — and no one is immune. That has CISOs and boards worried. Learn from these notable software supply chain attacks.

Welcome to the latest edition of The Week in Security, which brings you the latest headlines across the full stack of security: application security; cybersecurity; and beyond.

...

A malicious Python file found on the PyPI repository adds backdoor and data exfiltration features to what appears to be a legitimate SDK client from SentinelOne.

Experts and a top analyst discussed the state of software supply chain security in a recent Webinar. Here are key takeaways from their discussion.

Alphabet’s DeepMind brings us AlphaCode — another AI code-generating parlor trick. And, just like its large language model cousins, it can spit out buggy code.

Welcome to the latest edition of The Week in Security, which brings you the newest headlines from both the world and our team across the full stack of security: application security, cybersecurity, and beyond.
Get your 14-day free trial of Spectra Assure
Get Free TrialMore about Spectra Assure Free Trial